You need 7-zip to extract the file. If you don't have it installed, download and install the 64-bit version from:
Right-click the key.7z file and click 7-Zip, "Extract Here". Enter a password of malware
The sample appears, named key.exe.
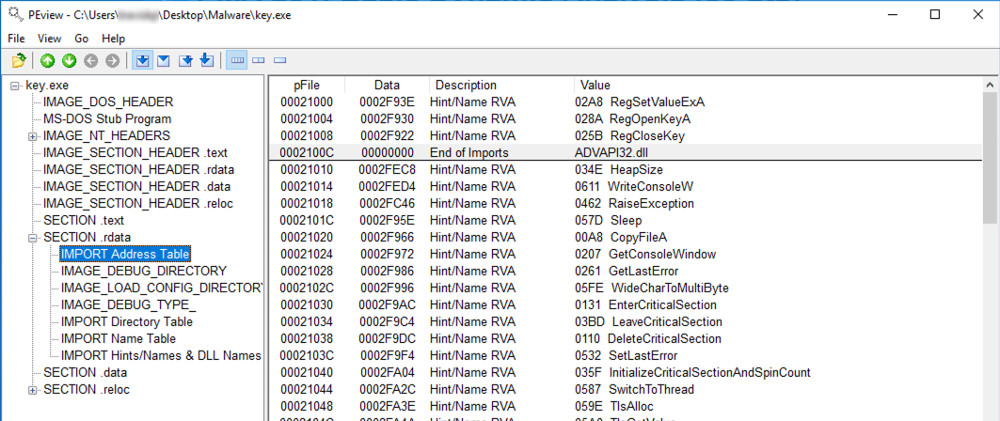
As shown below, if you expand "SECTION .rdata" and click "IMPORT Address Table", one of the three DLL's imported is advapi32.dll.
As you scroll you will see functions such as WriteConsoleW, GetConsoleWindow, WideCharToMultiByte, and GetStringType which assist us in identifying what the exe is doing.
The other two DLLs are kernel32.dll, and user32.dll.

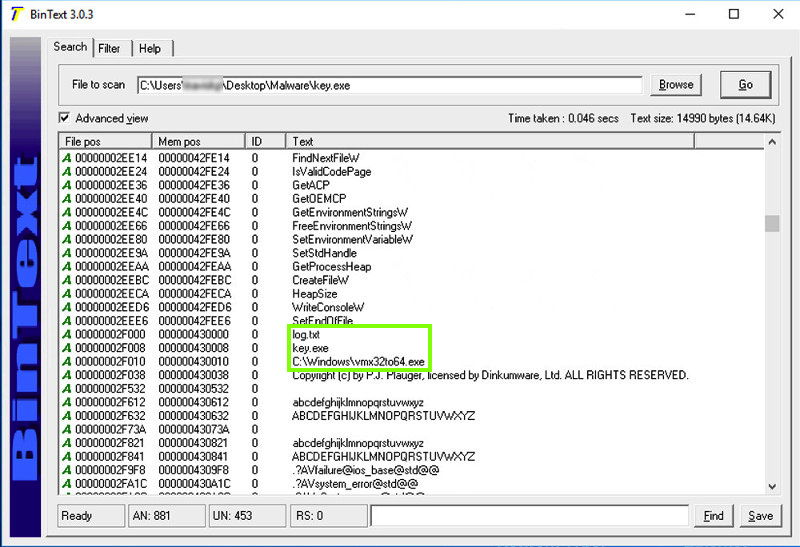
Scroll up and find the key definitions, including #SHIFT# and #CAPS_LOCK#, as shown below. These look like strings used by a keylogger.
We will use these three programs to see what the malware does:
Download Process Explorer from https://docs.microsoft.com/en-us/sysinternals/downloads/process-explorer
Extract the zip file and open procexp64
Process Explorer shows currently running processes, with far more detail than Task Manager. It doesn't keep a log of them, so it's harmless to leave running.
Install Wireshark with the default options
Start Wireshark and begin capturing packets from the interface that goes to the Internet, it should be "Ethernet".
There will be a lot of traffic at the start because you are running RDP from your host machine to the Windows cloud machine.
To filter out the RDP traffic, enter this into the Wireshark command line, replacing 192.168.10.10 with your host machine IP address:
!(ip.addr == 192.168.10.10)
Note: To get the ip of your host machine, Google search "What's My IP?
Once that command is entered, you can stop and start the capture again by clicking the red box and the blue fin above the command line. Close any open web browsers to limit the traffic.
Note: For this project, no web requests will be made by the malware, but it's a good idea to monitor network traffic when running malware.
It's best to start Process Monitor last, so you can exclude all the harmless processes the other tools are using.
Go to https://docs.microsoft.com/en-us/sysinternals/downloads/procmon and download / extract Process Monitor.
Note: if you are running Windows on ARM, download the zip file at the link above, unip it, and launch procmon64a.exe
Launch Process Monitor. If a Security Warning box pops up, allow the software to run.
Agree to the license.
You see Process Monitor, with a lot of visible events, as shown below.
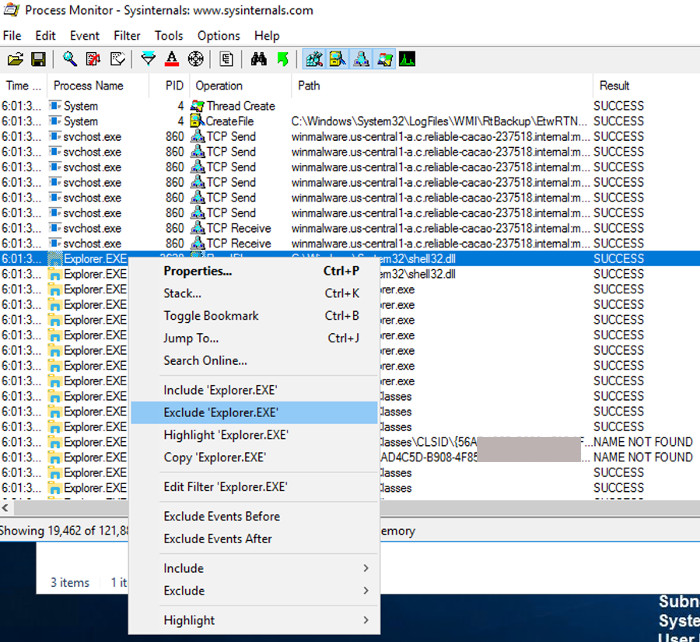
Repeat the process until all current processes are hidden, as shown below. There were a lot of processes to ignore, around 15 to 20.
Open Windows Security (search for it in the Start menu).
Click App & browser control.
Click Smart App Control settings.
Toggle to Off.
Flag 221.1: Viewing the Running Malware in Process Explorer (10 pts)
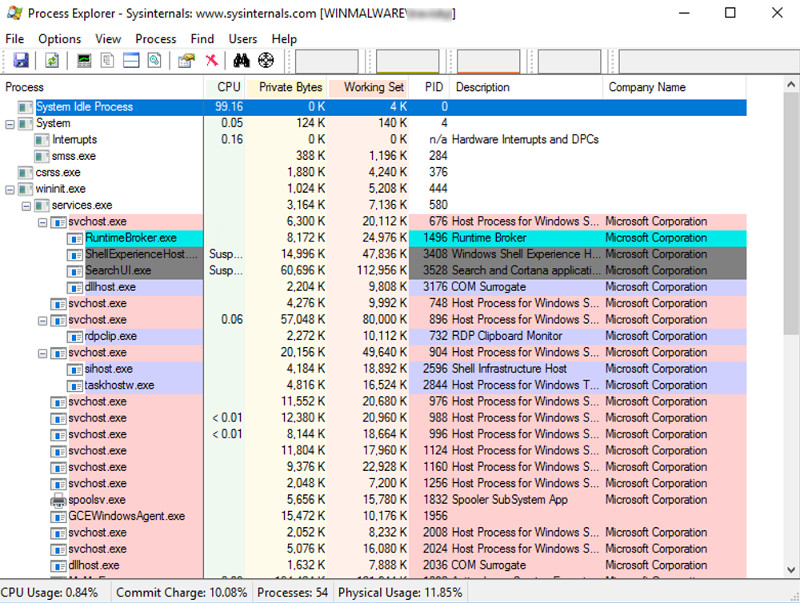
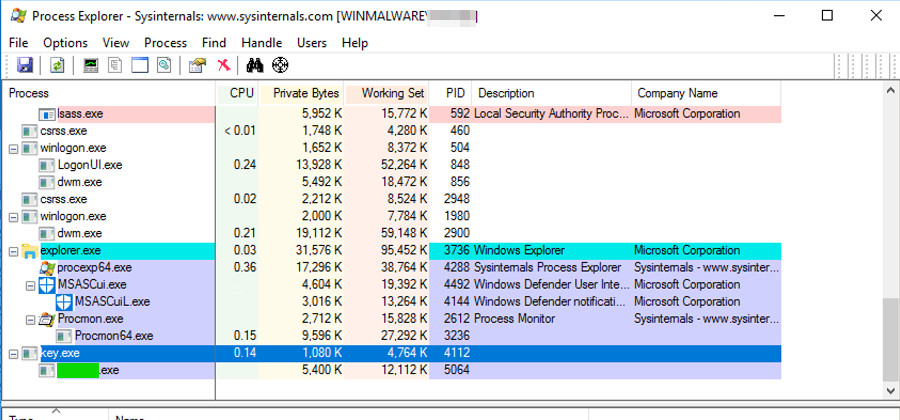
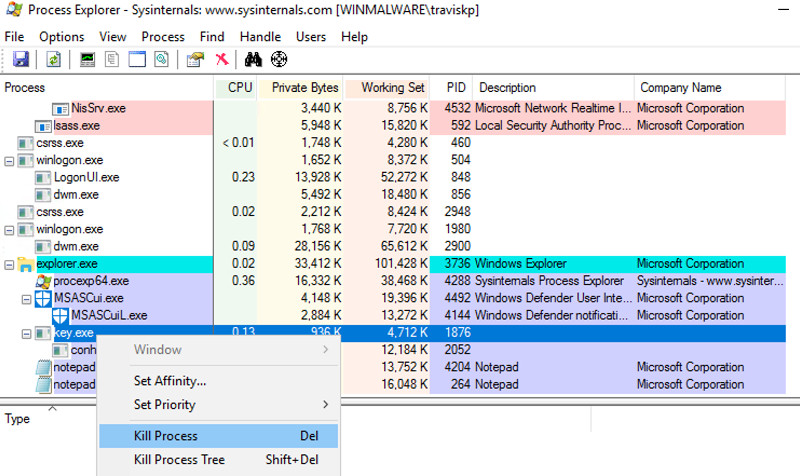
In Process Explorer, in the top pane, find key.exe and click it.Find the name of the exe covered in green in the image below. That is the flag.
Flag 221.2: Viewing the Running Malware in Process Monitor (5 pts)
Go to ProcMon and scroll until you get to key.exe. You can view the steps the malware is taking.
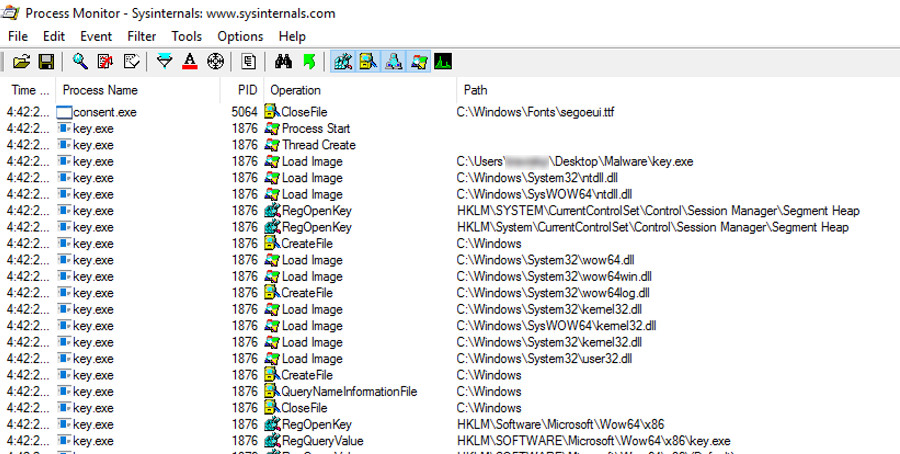
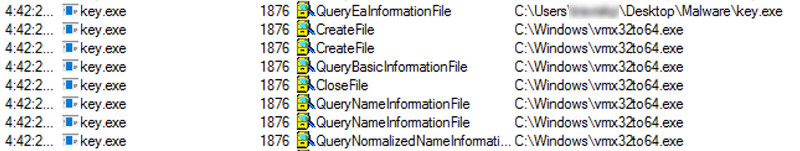
This malware creates an executable file in the Windows directory.
The malware also creates persistence by modifying the run registry key for the current user (HKCU = HKEY_CURRENT_USER). The programs referenced in this key will be executed when the user logs in.
Find the path of that key and take note of it.
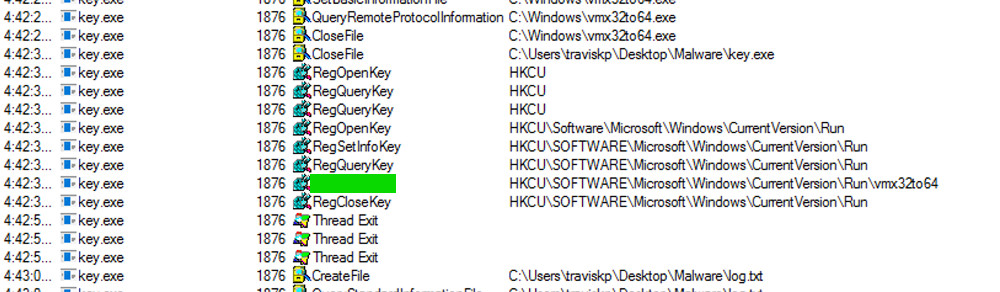
The flag is the text covered in green.
In File Explorer, go to the folder where key.exe is, find log.txt and open it. You see the captured keystrokes, as shown below.
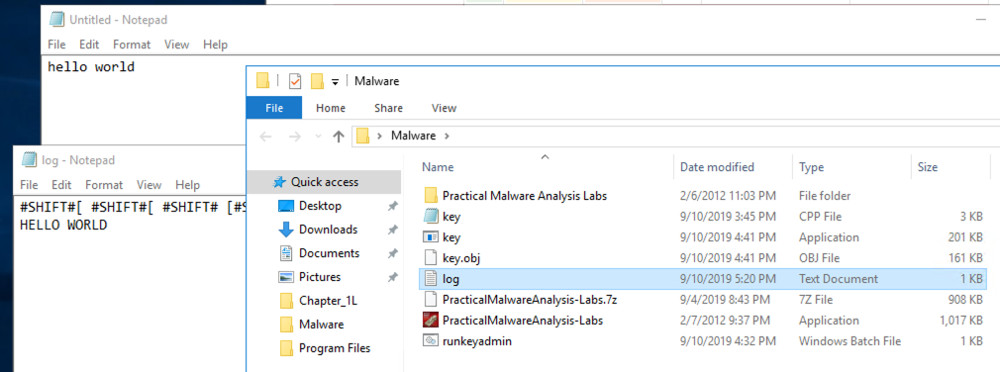
This stops the keylogger for the current sesssion. However, the malware has written itself into the registry, so it will start back up at the next reboot.
Restart the machine and reconnect through RDP.
Flag 221.3: Persistence (10 pts)
Open Process Explorer, find and click the new keylogger file, vmx32to64.exe.From the Process Explorer menu bar, click View, "Show Lower Pane" View, "Lower Pane View", Handles.
The flag is covered by a green rectangle in the image below.
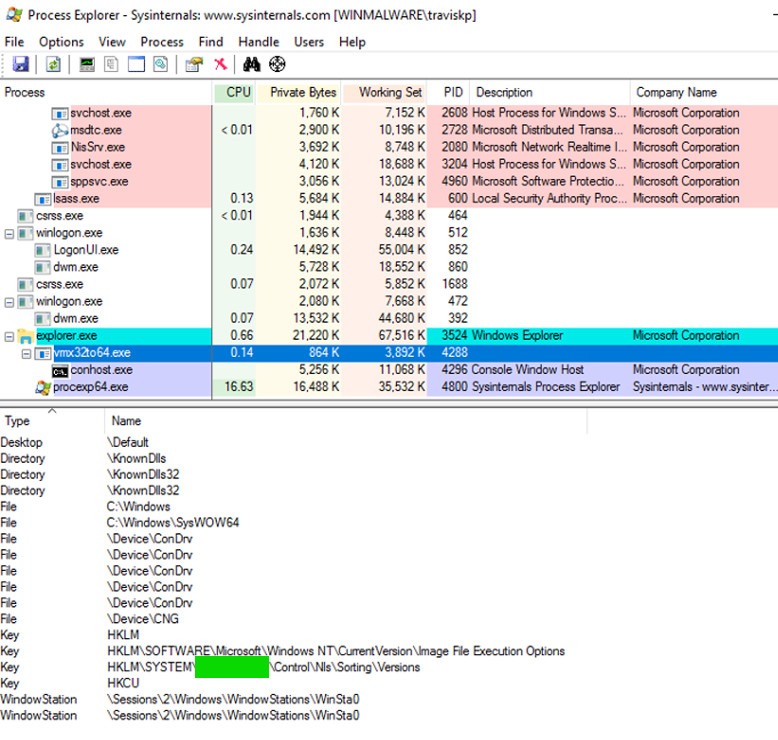
Flag 221.4: Removing persistence (5 pts)
Open command prompt and type in regeditNavigate to the path we saw in 2.2: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
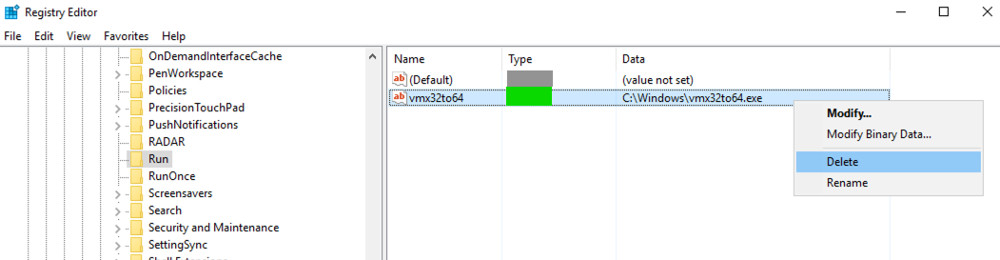
The flag is the text covered in green.
Right click vmx32to64 and delete the registry key.
Flag 221.5: Run Key (10 pts extra)
Download this sample and unzip it with the password malwareUse the same dynamic anaysis tools to monitor the behavior of this sample. Find the Registry action shown below. The flag is covered by a green rectangle.
Flag 221.6: DNS Traffic (10 pts extra)
Examine the network traffic generated by the key12.exe sample.Find the key in the DNS traffic, as shown below.
Flag 221.7: HTTP Traffic (10 pts extra)
Download this sample and unzip it with the password malwareExamine the network traffic generated by the key13.exe sample.
Find the key in the HTTP traffic, as shown below.