PMA 41: Windows 10 or 11 with Analysis ToolsThe malware samples are on your desktop.
Otherwise, download the malware from:
https://github.com/mikesiko/PracticalMalwareAnalysis-Labs
This project uses files in this folder:
Practical Malware Analysis Labs\BinaryCollection\Chapter_1L
https://github.com/mfput/McAfee-Tools,
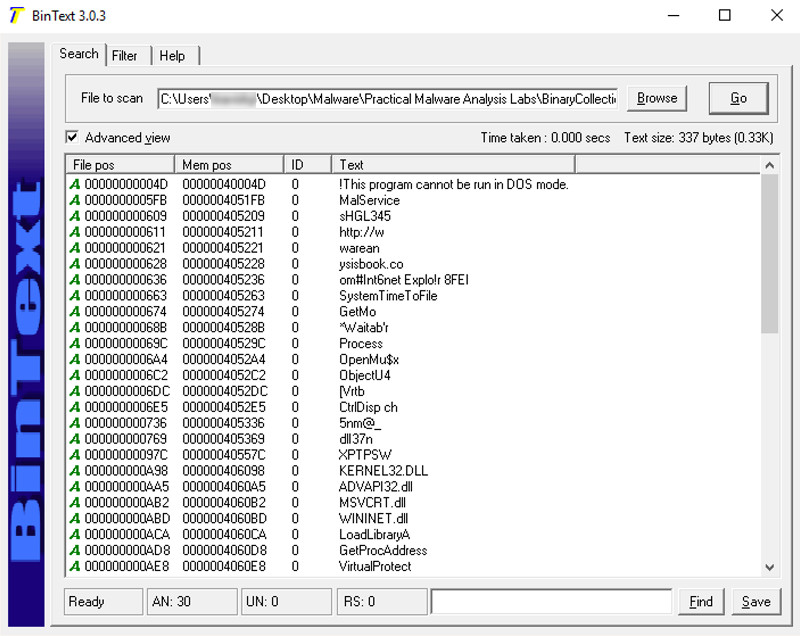
Examine the strings in Lab01-02.exe with BinText.
There are only a few strings, and they call only a few ordinary Windows API commands, as shown below.
These strings aren't from the malware--they are from the UPX packer, as we will show below.

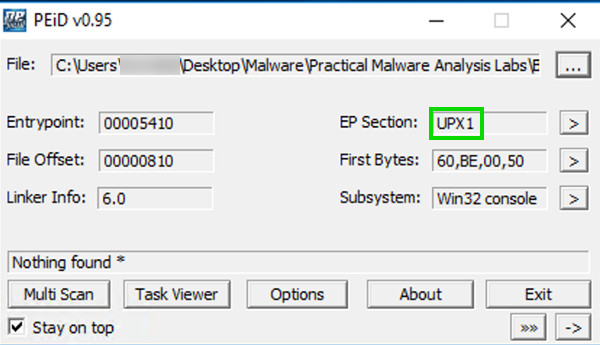
These are section names produced by the UPX packer.
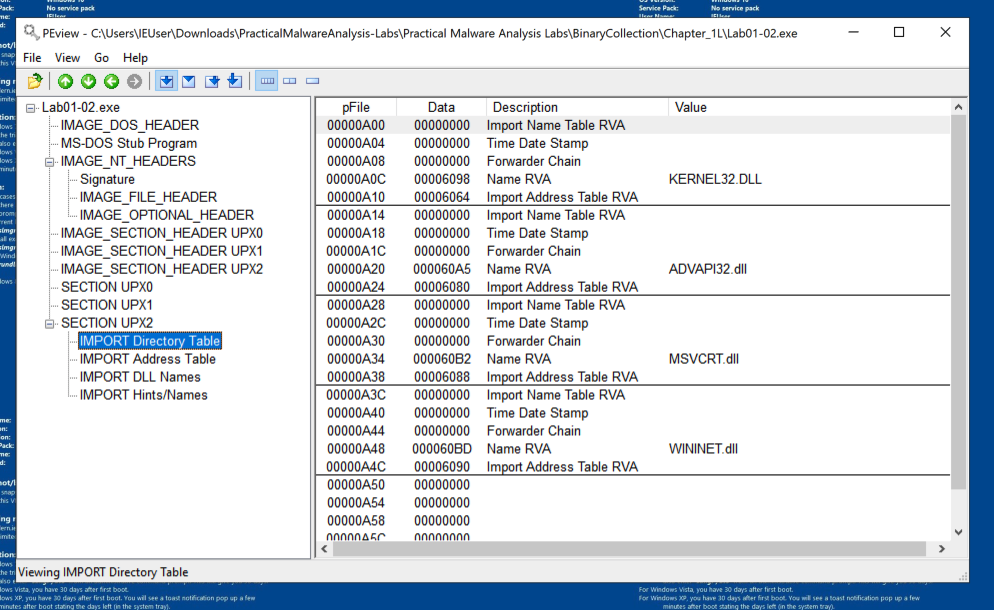
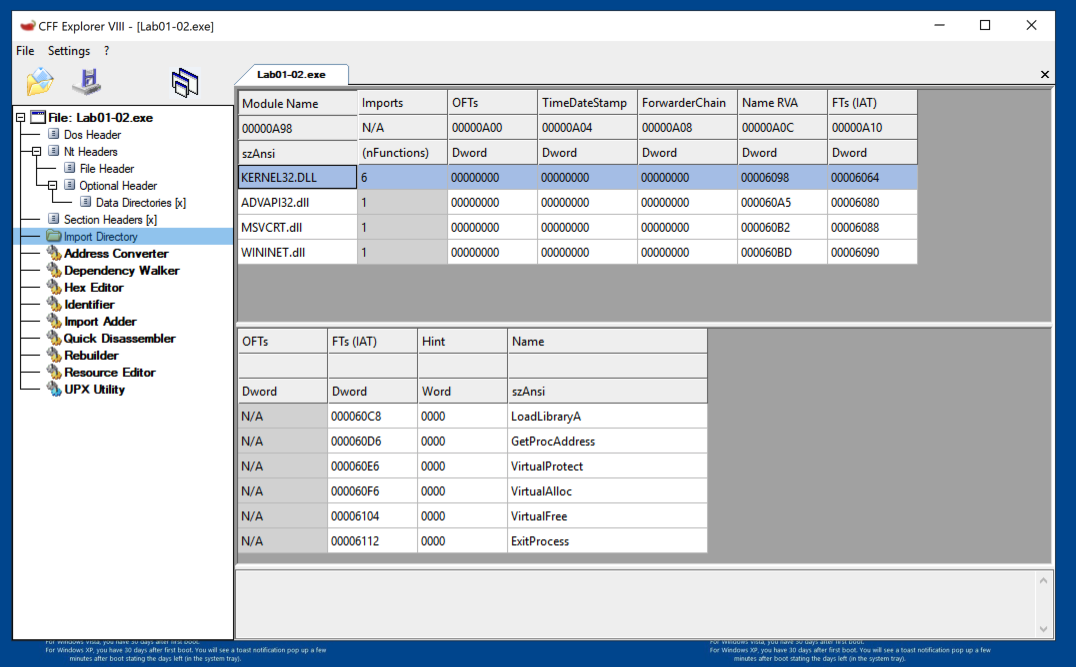
Navigate to the Import Directory Table, as shown below. This file only imports four libraries.
https://ntcore.com/?page_id=388
In the left pane, click "Import Directory". In the right pane, click KERNEL32.dll.
As shown below, this file only uses six functions from KERNEL32.DLL, and even fewer from the other imports.
UPX
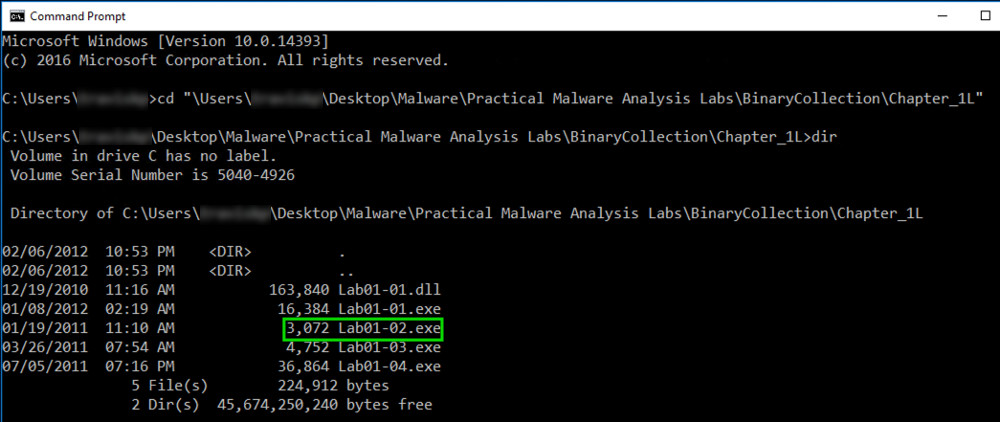
Execute these commands (replacing YourName with your username) to move to the directory containing the malware samples, and list the files there.
Use tab completion to speed up the process:
cd "\Users\YourName\Desktop\Malware\Practical Malware Analysis Labs\BinaryCollection\Chapter_1L"
DIR
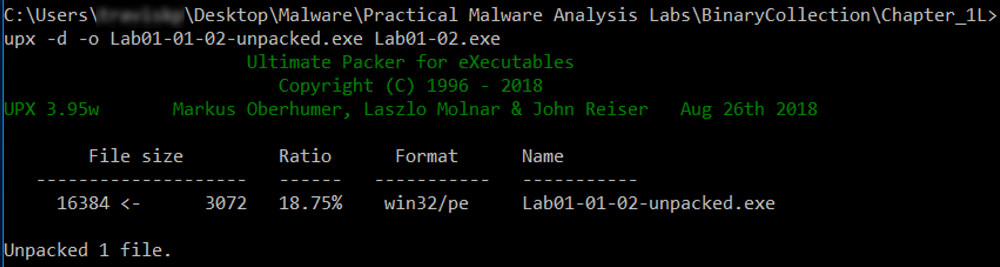
Execute these commands to unpack the file, and list the files again:
UPX -d -o Lab01-02-unpacked.exe Lab01-02.exe
DIR
Analyze the unpacked file with PEiD. It now is recognized as a "Microsoft Visual C++ 6.0" file, as shown below.
Flag PMA 102.1: Entrypoint (10 pts)
On the left side of the PeID box, find the Entrypoint value, which is covered by a green box in the image below. That's the flag.
Now the file has the usual sections labeled .text, .rdata, and .data, as shown below.
The imports from KERNEL32.DLL, ADVAPI32.DLL, and MSVCRT.DLL are uninformative generic functions used by almost every program.
However, the WININET.DLL imports are InternetOpenUrlA and InternetOpenA, as shown below. This indicates that the malware connects to a URL.

You should see the API names InternetOpenURLA and InternetOpenA, and the Command-and-Control URL http://www.malwareanalysisbook.com, as shown below.
These suggest that infected machines will connect to http://www.malwareanalysisbook.com. The name of the running service, MalService, is also visible.
Flag PMA 102.2: Last String (5 pts)
The last string is covered by a green box in the image below. That's the flag.
Ported to Google Cloud 9-5-19
Flag PMA 102.3: Packer (10 pts)
Find the packer used for sample Lab01-03.exe.Ignore everything except the primary packer name, which consists of three capital letters. That's the flag.