https://github.com/mikesiko/PracticalMalwareAnalysis-Labs
This project uses two files in this folder:
Practical Malware Analysis Labs\BinaryCollection\Chapter_1L
The two files are Lab01-01.exe and Lab01-01.dll.
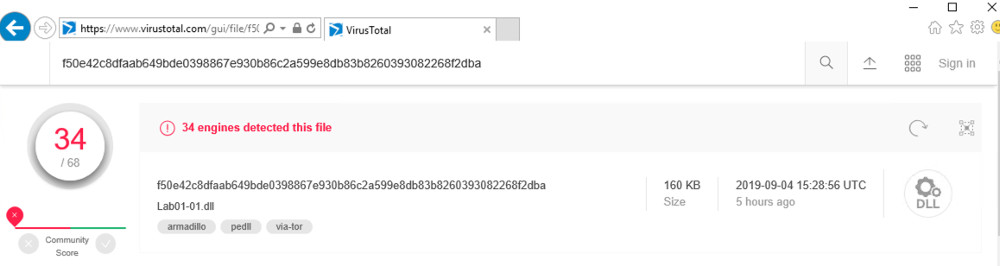
Upload Lab01-01.dll. As shown below, some of the engines detect it as malware.
VirusTotal compares a file to a database of antivirus engines. You can upload files, but that may alert attackers that you have detected an intrusion. Using it to search for a hash value of a sample is safer.

Goto http://wjradburn.com/software/.
Download PEview version 0.9.9 and unzip it. Double click PEview.exe
Click Run at the security warning.
Navigate to C:\Users\yourname\Desktop\Malware\Practical Malware Analysis Labs\Binary Collection\Chapter_1L and open Lab01-01.exe.
On the left side, expand the IMAGE_NT_HEADERS container and click IMAGE_FILE_HEADER.
The "Time Date Stamp" shows when the files were compiled. This is often used as an indication of the time zone the attackers live in. Files that were compiled at the same time are also often regarded as part of the same package.
Flag PMA 101.1: Data (5 pts)
Find the Data that is covered by a green box in the image below. That's the flag.
Download this file.
Extract all the files and run the PEiD application.In PEid, in the "File" line, at the right side, click the ... button.
Goto the Chapter_1L folder and open the Lab01-01.exe file.
On the bottom left, you can see that this file was written in "Microsoft Visual C++", as shown below.
Flag PMA 101.2: First Bytes (5 pts)
On the right side, note the "First Bytes", covered by a green box in the image below. That's the flag.
Download BinText from bintext303.zip
Extract and open BinText and click Run at the Security prompt.
Click the Browse button.
Goto the Chapter_1L folder, select the Lab01-01.exe file and click Go.
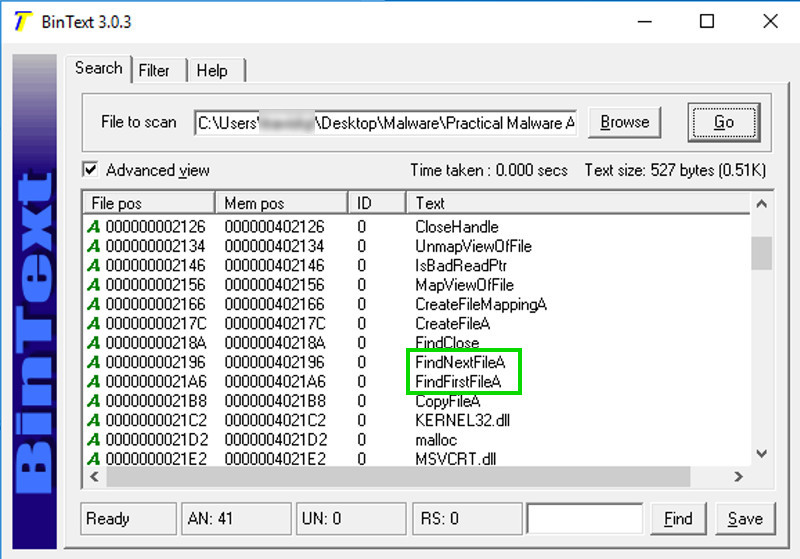
Notice FindNextFileA and FindFirstFileA, as shown below. These are Windows API functions used to search through a directory.
Scroll down and find these items, as shown below.
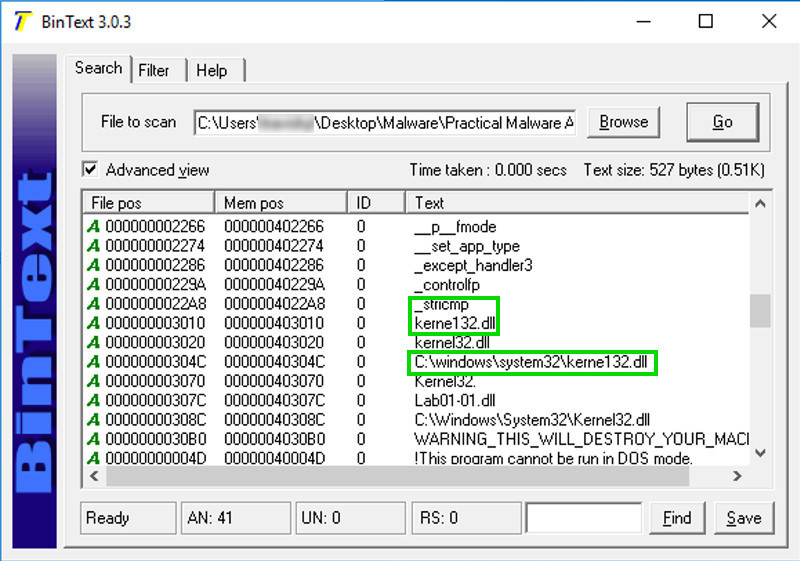
In BinText, open the Lab01-01.dll file and click Go.
Notice these items, as shown below:
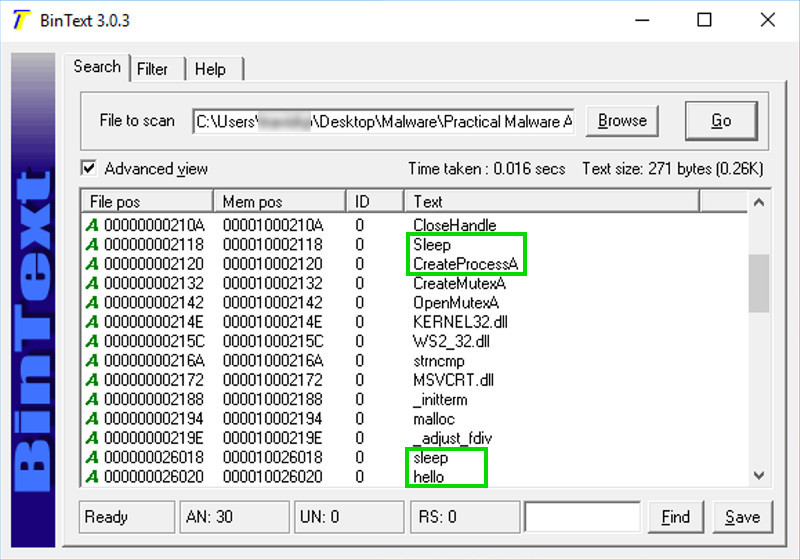
The command to launch a program is missing. To see it, click the Filter tab and adjust the "Min. text length" to 4 as shown below.
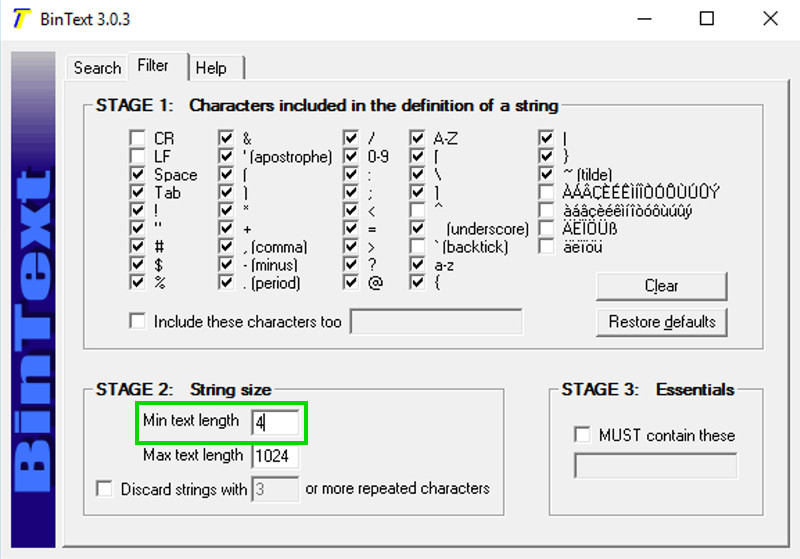
Click the Search tab. At the top right, click Go.
Now you can see that the command to launch a program is exec, appearing just above "sleep" in the image below.
Flag PMA 101.3: IP Address (5 pts)
Near the bottom, find the IP address beginning with 127, covered by a green box in the image below. That's the flag.
Extract the files and open the depends application.
In Dependency Walker, click the opening folder icon and open the Lab01-01.exe file.
An error message will popup, but you can ignore it and click ok. Learn more about it at https://stackoverflow.com/questions/33604738/dependency-walker-with-windows-10
The top left pane is called the
"Module Dependency Tree View".
It shows the EXE file and the two
Windows libraries it uses:
MSVCRT.DLL and KERNEL32.DLL,
as shown below (click the - next to KERNEL32.DLL).
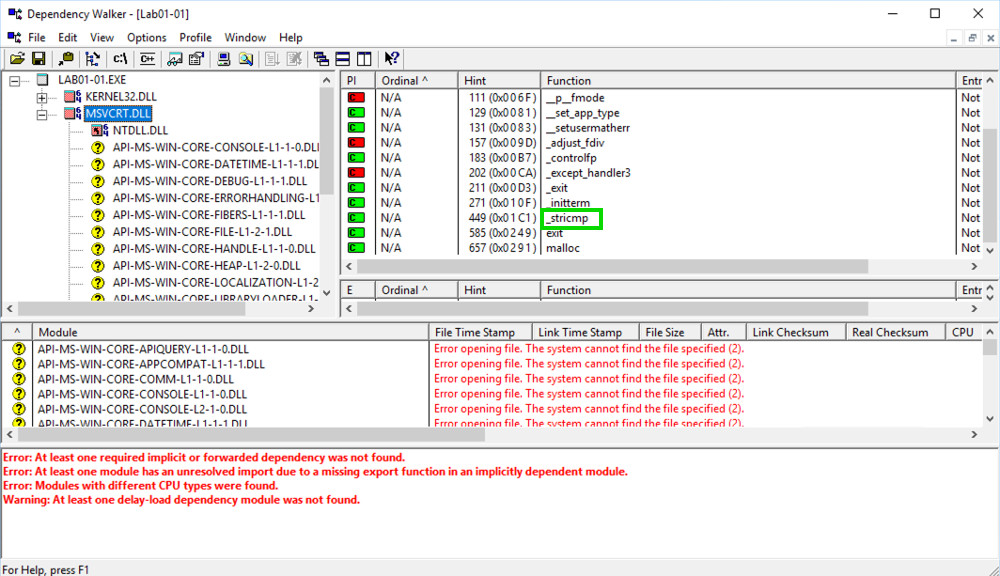
In the top left pane, click MSVCRT.DLL. The top right pane shows "Parent Imports". These are the functions the EXE file uses from the library.
As shown below, this executable uses only a small number of library functions, and none of them indicate much about its purpose. One of them is named _stricmp, which indicates that this progam performs a string copmarison, but that's a very common operation.
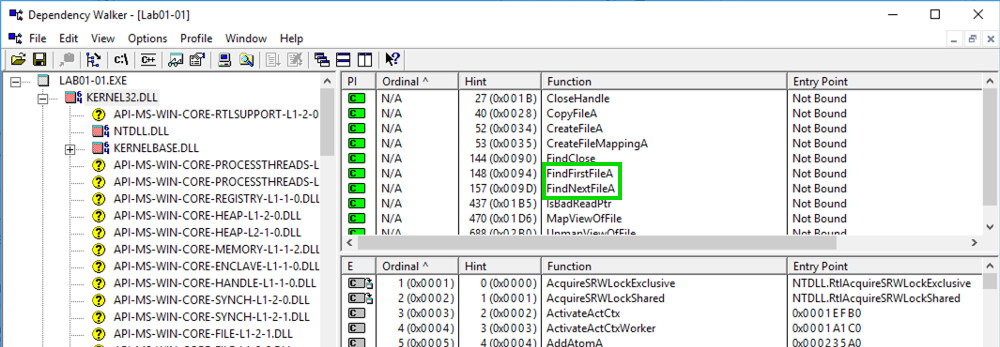
In the top left pane, click KERNEL32.DLL.
The top right pane shows that this file uses several functions that manipulate files, including FindNextFileA and FindFirstFileA, as shown below.
This suggests that the malware searches through the file system.
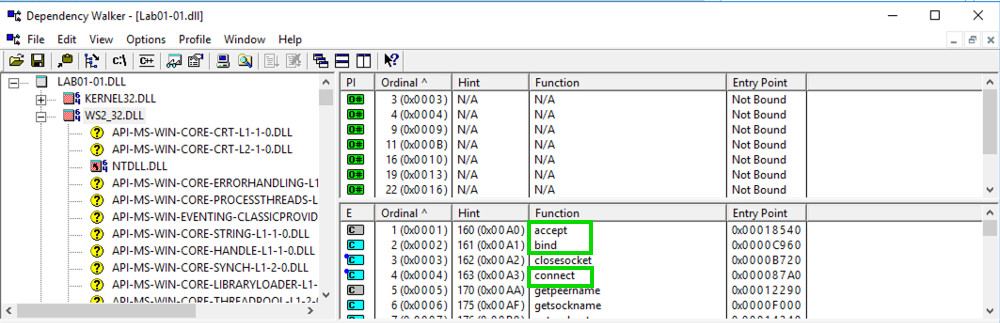
In the top left pane, partially collapse the tree to match the image below and click WS2_32.DLL.
The top right pane doesn't show function names this time, it only shows "Ordinal" numbers. This is called Linking by Ordinal, and it's an annoyance to us because we can't easily see what functions are in use.
The center-right pane shows the Exports of WS2_32.DLL, which include accept, bind, and connect. These are the standard Berkeley Sockets functions used for networking. This suggest that the malware performs some networking functions, such as connecting to a server and opening a listening port.
In the top left pane, click KERNEL32.DLL. The top right pane shows the five "Parent Imports", which include CreateProcessA and Sleep, as shown below.
Flag PMA 101.4: Function Name (5 pts)
Find the function name that is covered by a green box in the image below. That's the flag.
Flag PMA 101.5: Find the Downloaded File (10 pts extra credit)
Analyze the sample Lab01-04.exeIt downloads a file from this domain: practicalmalwareanalysis.com
Find that file's name. That's the flag.
Flag PMA 101.6: Find the Imported Function (10 pts extra credit)
Analyze the sample Lab01-04.exeIt imports a function from WINTRUST.DLL with a name ending in "Trust".
Find that function's name. That's the flag.
Flag PMA 101.7: Find the Datestamp (10 pts extra)
Find the date when sample Lab01-04.exe was compiled, like this: 2000/01/01. That's the flag.
Analyzing dependencies with Dependency Walker