Launch Task Manager.
On the left side, click Details.
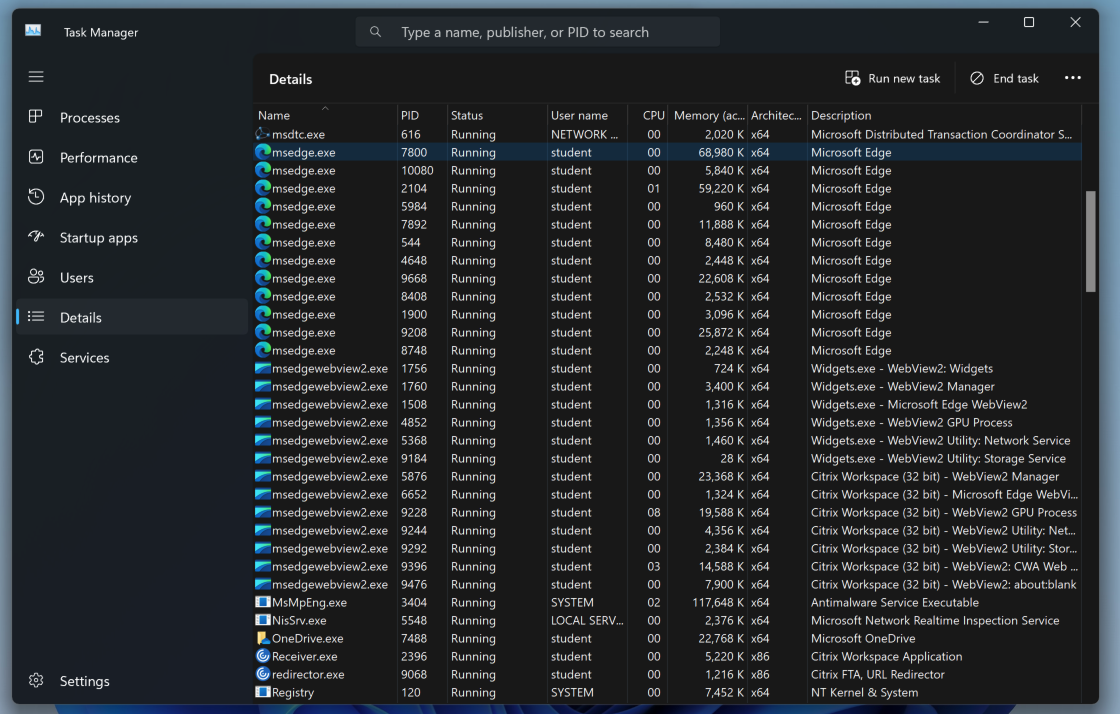
There are a lot of msedge.exe processes. Find the one with the most memory usage.
In the image below, it's PID=7800. It will be a different number on your system.

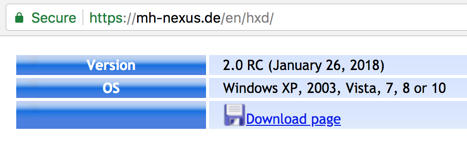
In a Web browser, go to https://mh-nexus.de/en/hxd/
Scroll down and find the download link for modern Windows versions, as shown below.
Click the download link, download the English version, unzip it, and install it with the default options.
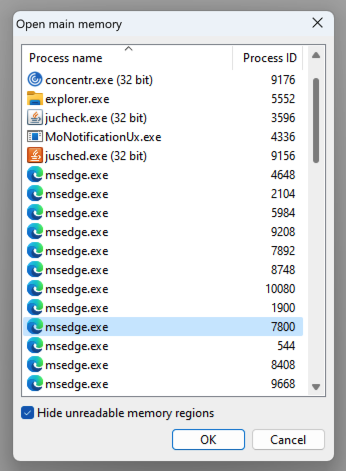
Find the msedge process you identified in Task Manager and double-click it, as shown below.
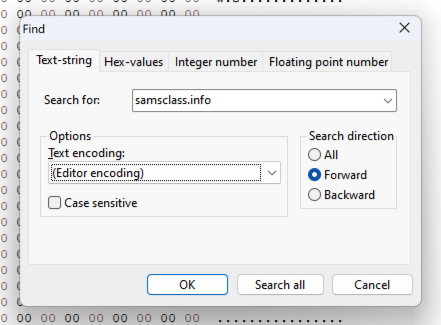
In HxD, click Search, Find.
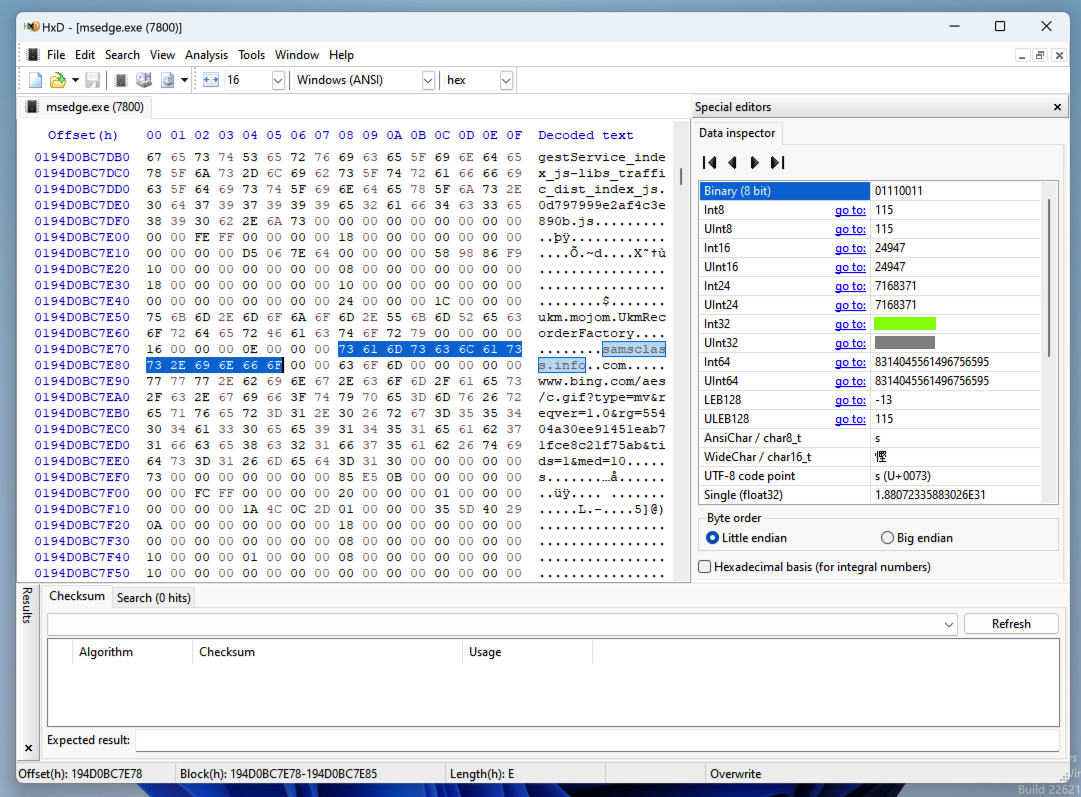
On the Text-string tab, search for
samsclass.infoas shown below.
Flag IR 303.1: Int32 Value (15 pts)
On the right side of the HxD window, a pane shows various interpretations of this byte sequence.If you don't see this pane, click View, "Data inspector".
The Int32 value is a long number beginning with 19, covered by a green box in the image below. That's the flag.
Updated to Cloud, removed BCDEdit steps: 8-18-19
Integrated with Canvas 8-20-18
Typos fixed, RAM reducing added, and "net user" removed 8-27-18
Administrator Command Prompt instructions added 8-28-18
Updated to Windows 11 3-29-24