sudo apt update
sudo apt install hashcat -y
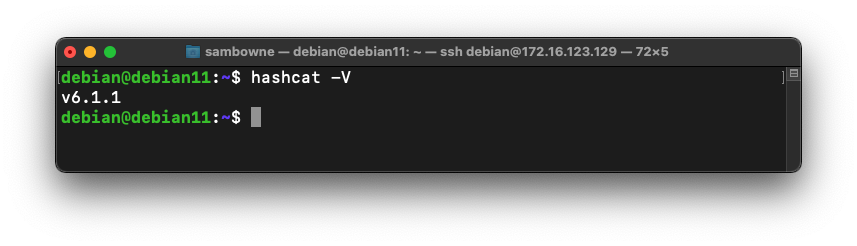
hashcat -V

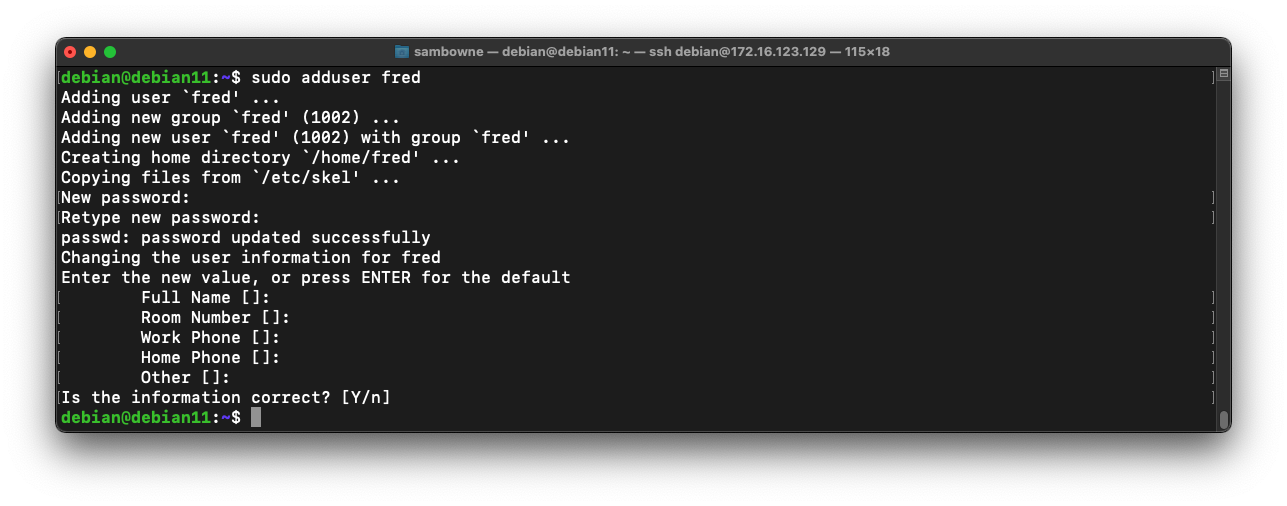
sudo adduser fred
At the "Retype new UNIX password" enter a password of password
Press Enter to accept defaults for the other options, as shown below:
sudo tail -n 1 /etc/shadow
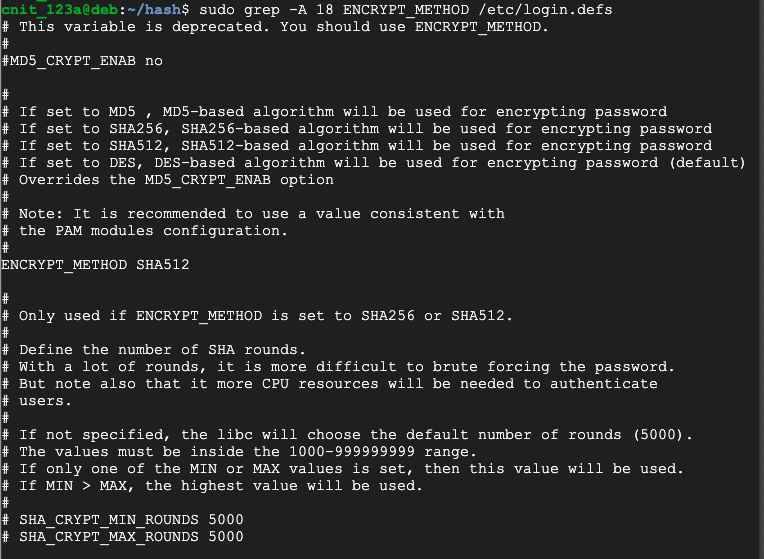
The $y$ prefix indicates that this is a yescrypt hash, which cannot be cracked by hashcat as of 2023. It can be cracked with john, however.
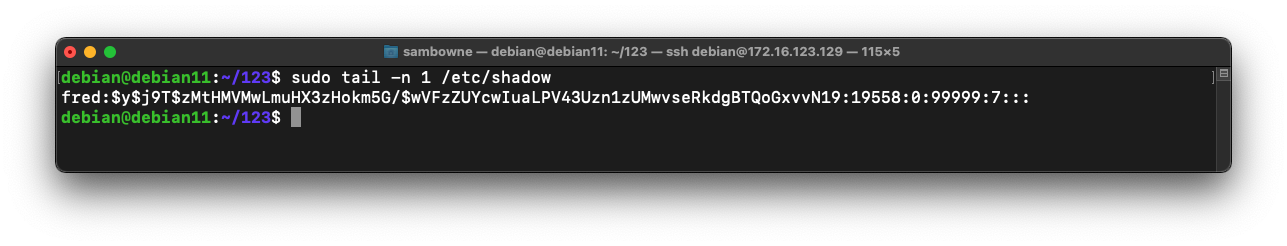
The $6$ indicates a type 6 password hash (SHA-512, many rounds).
sudo apt update
sudo apt install whois
mkpasswd -m sha-512 password SALTSALT > crack1.hash
cat crack1.hash
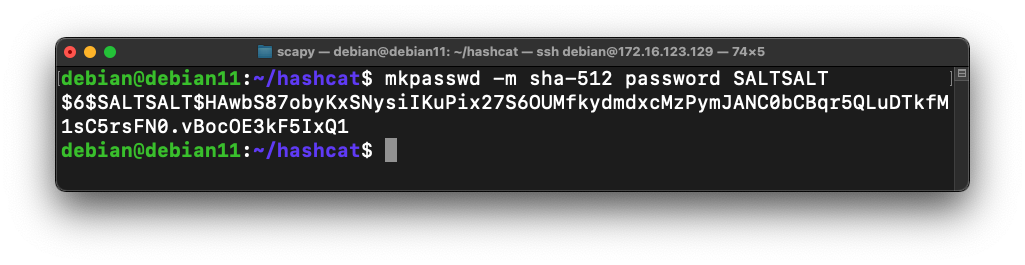
In the image above, the SALT is SALTSALT
sudo grep -A 18 ENCRYPT_METHOD /etc/login.defs
sudo apt install wget -y
wget https://github.com/hashcat/hashcat/raw/master/example.dict
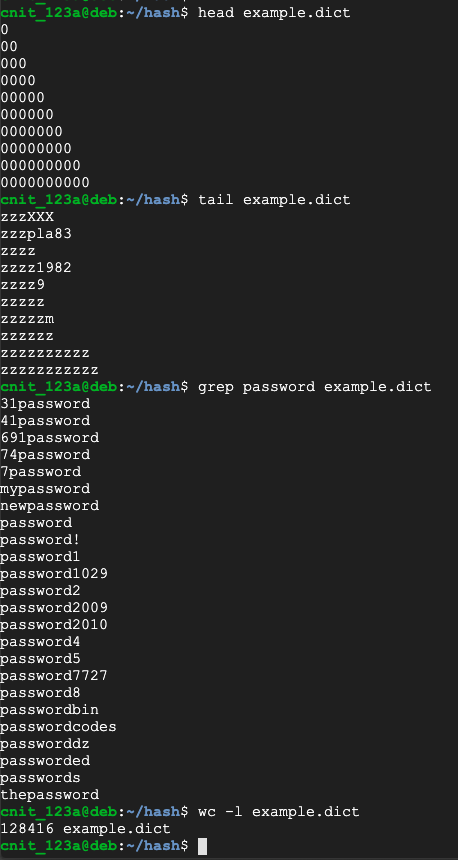
head example.dict
tail example.dict
grep password example.dict
wc -l example.dict
hashcat -m 1800 -a 0 crack1.hash example.dict
H 520.1: Status (10 pts)
After a few minutes, hashcat will find the password, outlined in yellow in the image below.
The flag is covered by a green rectangle in the image above.
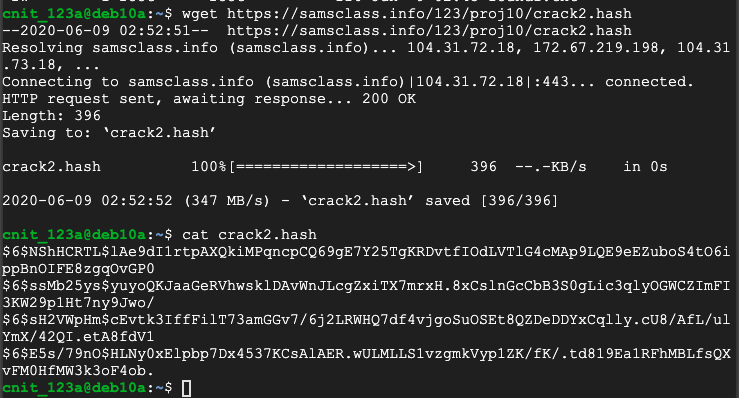
wget https://samsclass.info/123/proj10/crack2.hash
cat crack2.hash
H 520.2: p-Password (10 pts)
Crack the hashes using the same wordlist. One of the passwords begins with the letter "p". That password is the flag.If you're waiting for 20 minutes, you're doing it the hard way. Try trimming the wordlist before performing the crack.
H 520.3: s-Password (10 pts)
Crack the hashes using the same wordlist. One of the passwords begins with the letter "s". That password is the flag.
wagner:"":"":AAD3B435B51404EEAAD3B435B51404EE:4F2D47B681C9FCFFBE11ED6E9F7DF1BA
waldo:"":"":AAD3B435B51404EEAAD3B435B51404EE:76BF100CEA9B9F7B9E0C78419998AE1B
walter:"":"":AAD3B435B51404EEAAD3B435B51404EE:A60E7EB7B49FD0C2E7DD4739FF2AE76B
Hint: remove extraneous text from the hashes to avoid confusing hashcat.
H 520.4: Word (10 pts)
One of the passwords is in the example wordlist, like "password". That password is the flag.
H 520.5: Word Plus Digit (10 pts)
One of the passwords is a word in the example wordlist with a digit added to it, like "password1".That password is the flag.
H 520.6: Word Plus Two Digits (10 pts)
One of the passwords is a word in the example wordlist with two digits added to it, like "password11".That password is the flag.
http://hashcat.net/files/hashcat_user_manual.pdf
How To Use hashcat On CPU Only