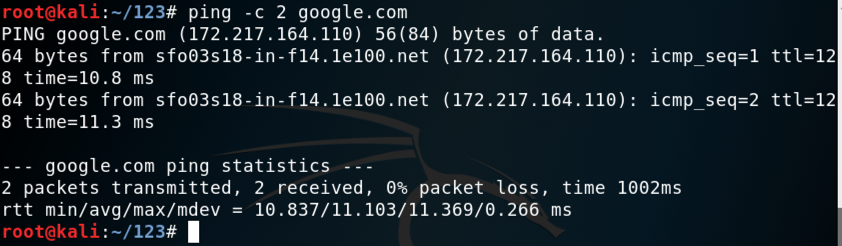
ping -c 2 google.com

sudo apt update
sudo apt install git -y
git clone https://github.com/secdev/scapy.git
cd scapy
sudo ./run_scapy
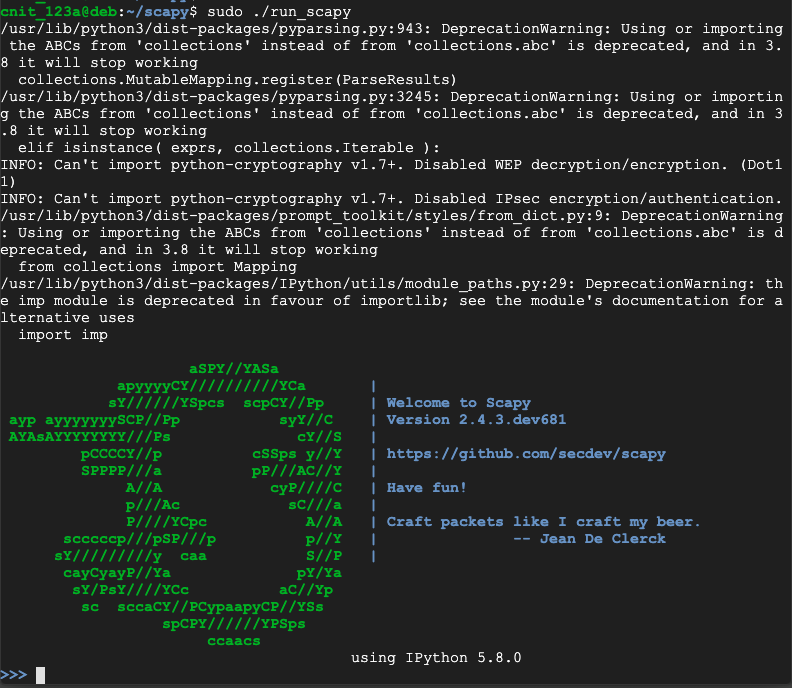
i = IP()
i.display()
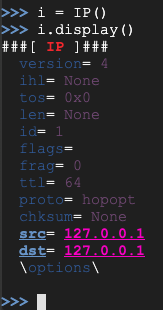
Use these commands to set the destination IP address and display the properties of the i object again. Replace the IP address in the first command with the IP address of your Target machine:
i.dst="google.com"
i.display()
Use these commands to create an object named ic of type ICMP and display its properties:
ic = ICMP(id=100)
ic.display()
There aren't many properties for this object--it's just an echo-request, as shown below on this page.
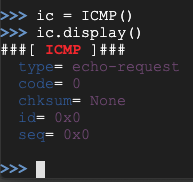
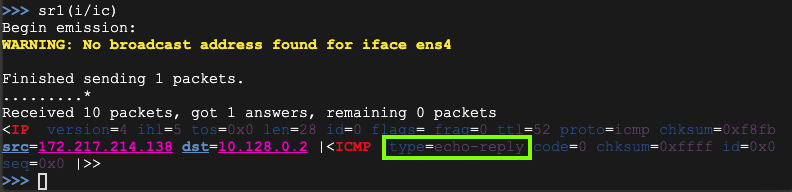
Use this command to send the packet onto the network and listen to a single packet in response. Note that the third character is the numeral 1, not a lowercase L:
sr1(i/ic)
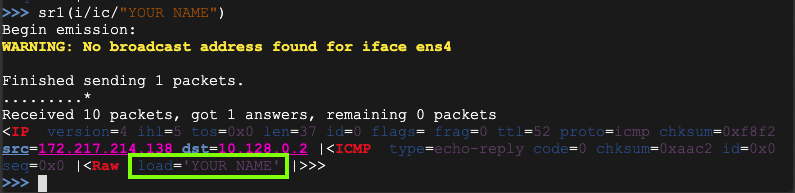
Use this command to send a packet that is IP at layer 3, ICMP at layer 4, and that contains data with your name in it (replace YOUR NAME with your own name):
sr1(i/ic/"YOUR NAME")
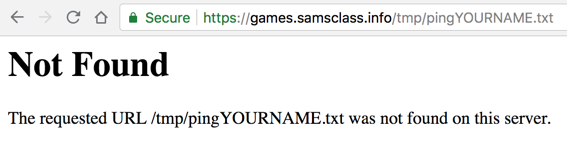
https://games.samsclass.info/tmp/pingYOURNAME.txtThe page is not found, as shown below on this page.
Use Scapy to send an ICMP request with these properties:
H 430.1: Web Page (10 pts)
Refresh the Web page a few times. After a few seconds the flag will appear, as covered in a green box in the image below.
i = IP()
i.dst = "1.1.1.1"
u = UDP()
d = DNS()
d.qd=DNSQR(qname="www.google.com")
d.display()

Execute this command to send the request:
sr1(i/u/d)
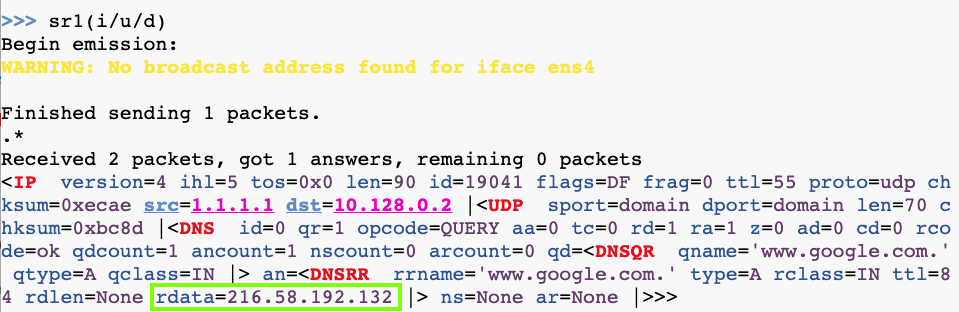
H 430.3: IP of Flag0 (5 pts)
Find the IP address of this server:That IP address is the flag.
H 430.4: CNAME of Flag1 (10 pts)
Find the CNAME record for this server:That CNAME contains the flag.
H 430.5: DNS Record of Flag2 (15 pts)
Find a DNS record containing a flag for this server:Hint: Know the eight most common DNS records
H 430.6: One (20 pts)
Perform a reverse DNS lookup for this address:Make sure the answer is correct, outlined in green in the image below.The flag is the text covered by a green rectangle in the image below.