Download and install the latest version.
I wrote these instructions using Wireshark 2.6.1 for the Mac on 6-28-18.
Find these features, as shown below:

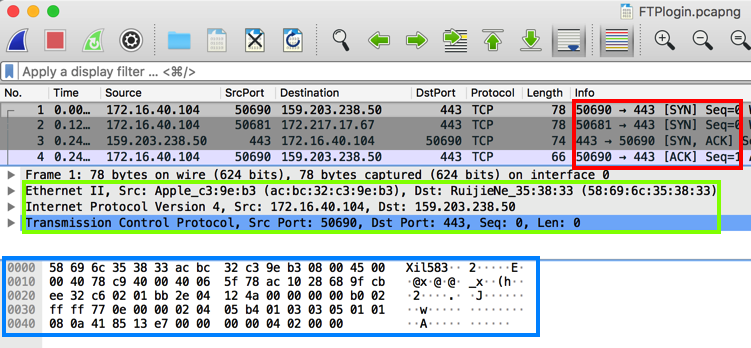
In Wireshark, at the top, in the "Apply a display filter" box, type ftp and press the Enter key.
Wireshark filters the packets, showing only the packets using File Transfer Protocol. On the right side, you can see the login process for a user named "john".
H 420.1: John's Password (5 pts)
Find John's password, which is covered by a green rectangle in the image below. That's the flag.
Download this file and double-click it to open it in Wireshark:
In Wireshark, at the top, in the "Apply a display filter" box, type http and press the Enter key.
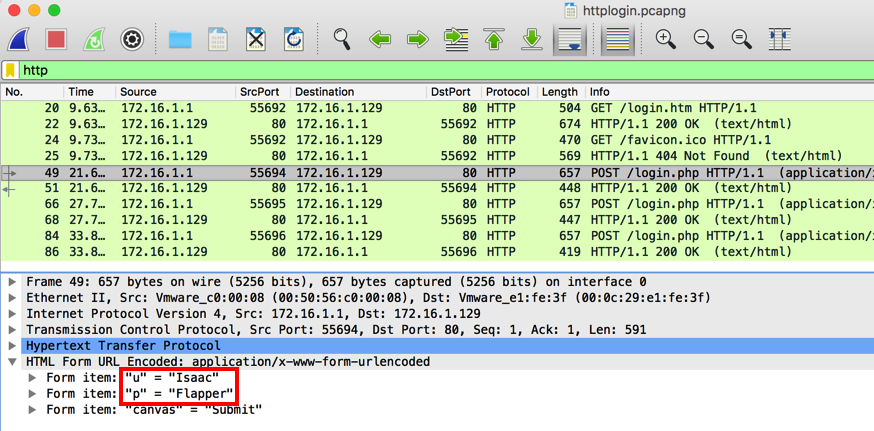
Wireshark filters the packets, showing only the packets using HTTP. In the Packet List, in the "Info" column, find the first POST request, as shown below, and click it.
In the Packet Details, expand the "Hypertext Transfer Protocol" container. The username of "Isaac" and password of "Flapper" are visibie, as outlined in red in the image below.
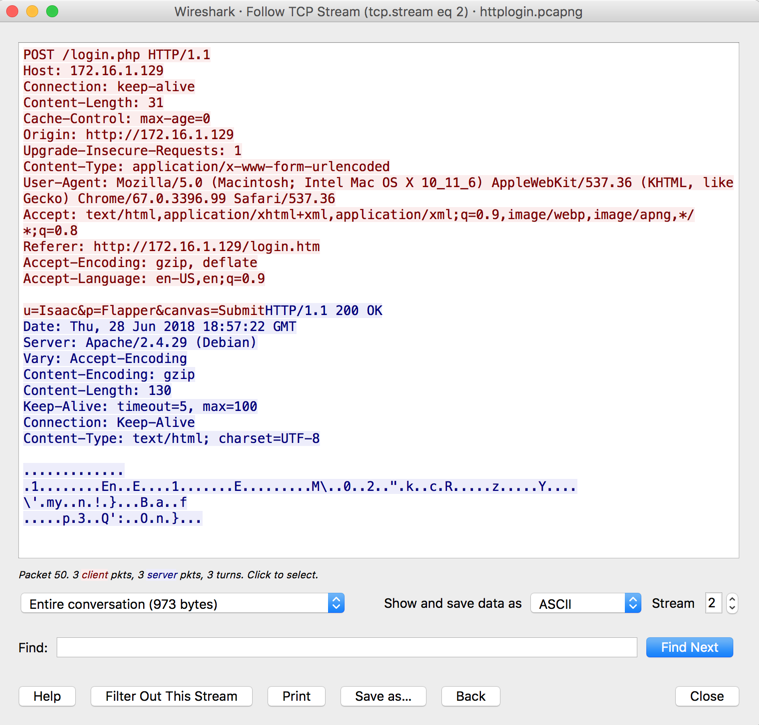
The conversation is shown, with the client's transmission in red, and the server's response in blue, as shown below.
The TCP Stream is often very helpful, but not in this case, because the reply is zipped.
In Wireshark, at the top, in the "Apply a display filter" box, on the right side, click the X to clear the filter.
In the "Apply a display filter" box, type http and press the Enter key.
All the "http" packets appear, as shown below.
In the Packet Details, expand the "Line-based test data" container. The server's reply is now readable, saying "Login Denied!", as outlined in red in the image below.
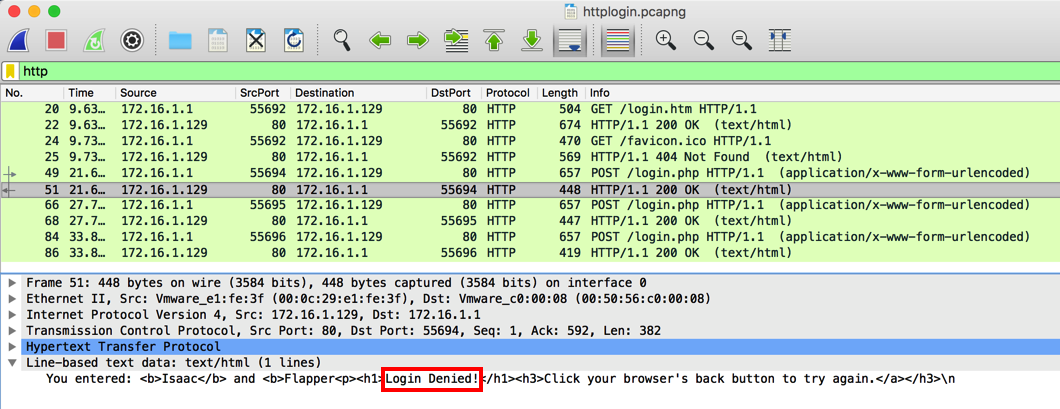
H 420.2: Isaac's Password (10 pts)
Isaac made several attempts to log in before finally entering the correct password.Find the password that worked. That's the flag.
H 420.3: HTTP Basic Authentication (15 pts)
HTTP Basic authentication obfuscates passwords with Base64 encoding before transmitting them, which is not much better than sending them in cleartext, because Wireshark automatically decodes them.Download this file and double-click it to open it in Wireshark:
A user named WALDO logged in. Find Waldo's password. That's the flag.
This file contains some APT attacker traffic, which I got in the Red Team CTF on May 16, 2020.
Analyze it and answer the following questions:
H 420.4: Encrypted Transmission (10 pts)
There is only one protocol used for encrypted communication, with more than 3 packets sent.Find the port number of the server side of the encrypted transmissions. That's the flag.
HINT: Use Statistics, "Protocol Hierarchy". Right-click a protocol to filter for it.
H 420.5: Tool (10 pts)
What tool is being used to perform encrypted communications? The tool's name is 5 letters long. That's the flag.HINT: Use a filter like:
frame contains "80"to find frames containing a command line using the port number you found in the previous flag.Don't forget the quotation marks!
Follow the streams to see the commands the attacker executed in red letters.
H 420.6: Hash of Tool (10 pts)
Provide the sha1sum of the tool used to perform encrypted communications. That's the flag.HINT: Use "frame contains" to find frames containing text including the tool name you found in the previous flag.
Follow the streams of data sent from that port. Find the stream that begins with ".ELF" -- that's a Linux executable. Save it as "Raw" data locally with the name "socat". Then calculate its hash.
H 420.7: Decrypt (15 pts)
Find the private key used for encrypted communications. Decrypt the encrypted communications and find the flag inside.HINTS: TLS Decryption
Search for text found in the PEM File Format
Follow the stream. Copy the private key into a file ending with ".pem"
In Wireshark Preferences, in the Protocol "TLS", add your key file.
Filter for the port number used in flag H 420.4
In Wireshark, click File, "Export Packet Dissections", "As Plain Text". Check "Bytes".
Open the exported file in a text editor and search for "Decrypted".
H 420.8: Port Knocking (15 pts)
There appears to be some port knocking on the network, what ports are being knocked? The flag is the answer in the form of "port,port,port", in the order the knocks are sent.HINT: Click Statistics, Conversations. Examine the TCP ports.
Look for an obvious pattern of port numbers changing by 1000.
Examine the unfiltered traffic near those conversations.
Filter for SYN packets from the same source IP to see the time sequence.
H 420.9: Exploitation (20 pts)
On several occasions, after three knocks, the attacker got a shell on a target machine.Find the shell session with the largest number of bytes transferred. The attacker executed over 40 shell commands.
The flag is the last command executed in that session.
HINT: Filter for SYN packets on the first port number in the knocking sequence.
There are 11 knocking attempts.
Filter by source IP address. All 11 knocking attempts are visible together.
Follow the streams to see which session is the largest.
Revised to new flag system 5-17-2020
420.5 hint improved 6-14-2020
420.7 hints added 7-25-2020
420.5 hint improved more 7-26-2020
420.7 hint added 8-1-2020
Background changed to white 10-7-21
Hints added to last challenges 4-5-23
Video added 4-24-23
Hint added to flag 5 7-22-23