
"Command Prompt" is found, as shown below.

Click "Command Prompt".
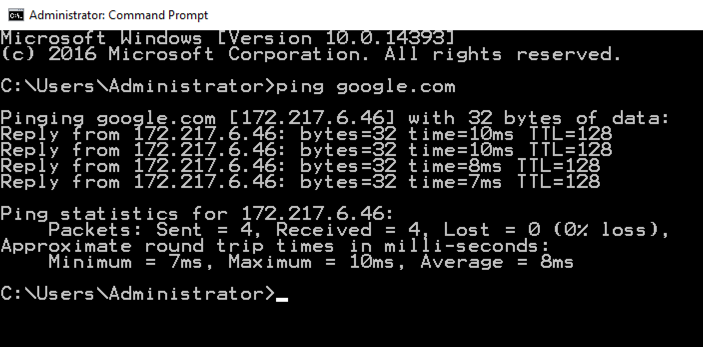
In the Command Prompt window, execute this command, as shown below.
ping google.com
Type FIREWALL.
In the Search results, click "Windows Firewall", the second result in the image below.
In the Windows Firewall box, on the left side, click "Turn Windows Firewall on or off".
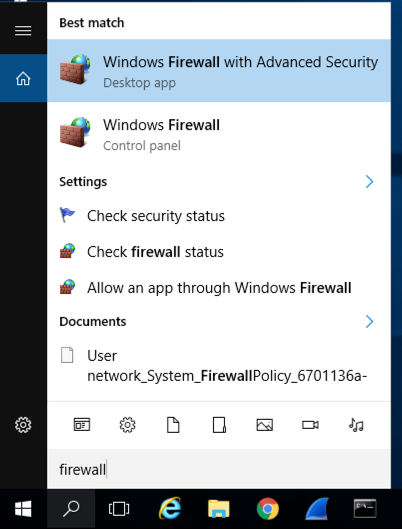
Check both of the boxes labelled "Turn off Windows Firewall (not recommended)", as shown below.
Click OK.
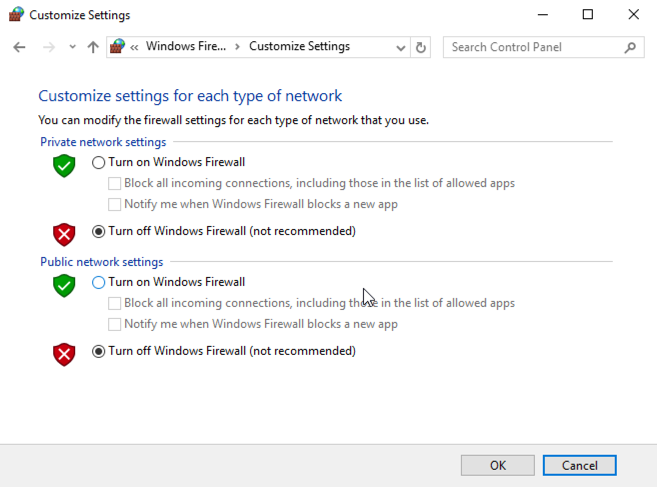
In the left pane, click "Local Server".
In the right pane, in the "Remote Desktop" line, click the blue word Disabled.
In the System Properties box, click "Allow remote connections to this computer".
Click OK. Click OK.
In Server Manager, at the top right, click the circular icon with two curved arrows to refresh the view.
Remote Desktop is now Enabled, as shown below.
ipconfig
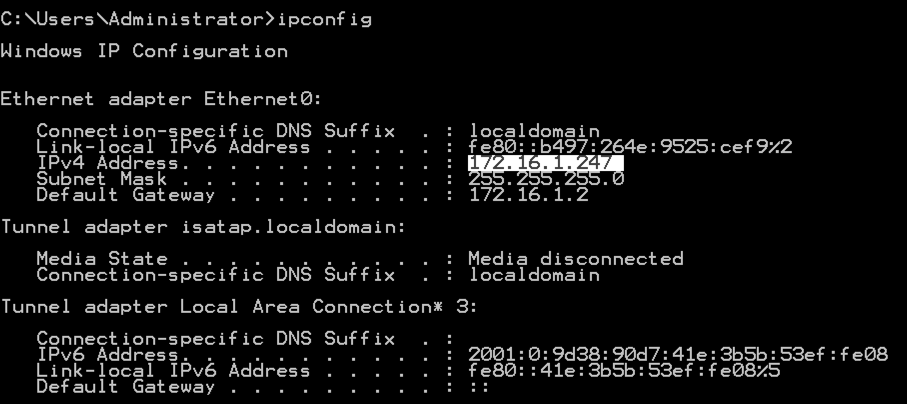
On your Linux machine, in the Terminal window, execute this command, as shown below, replacing the IP address with the IP address of your Windows Server machine.
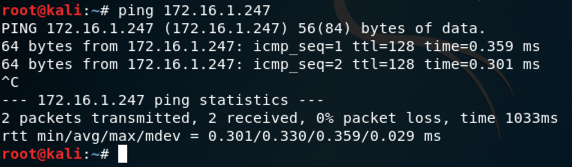
ping 172.16.1.247
You should see replies, as shown below. If you do not, perform the "Troubleshooting" steps in the box above. You should also make sure the Windows firewall is off, as explained in an earlier project.
sudo apt update
sudo apt install nmap -y
sudo nmap 192.168.100.4
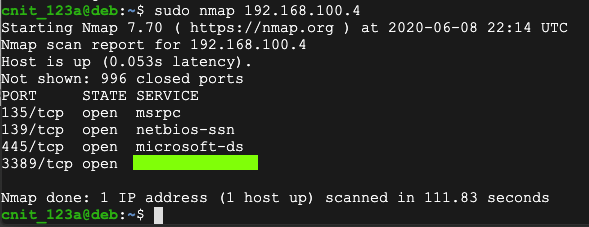
H 410.1: "SERVICE" name (15 pts)
Find the "SERVICE" name for port 3389, which is covered by a green box in the image above. That's the flag.
https://svn.nmap.org/nmap/docs/nmap.usage.txt
These are the most important ones:
Your results should be similar to those shown below.
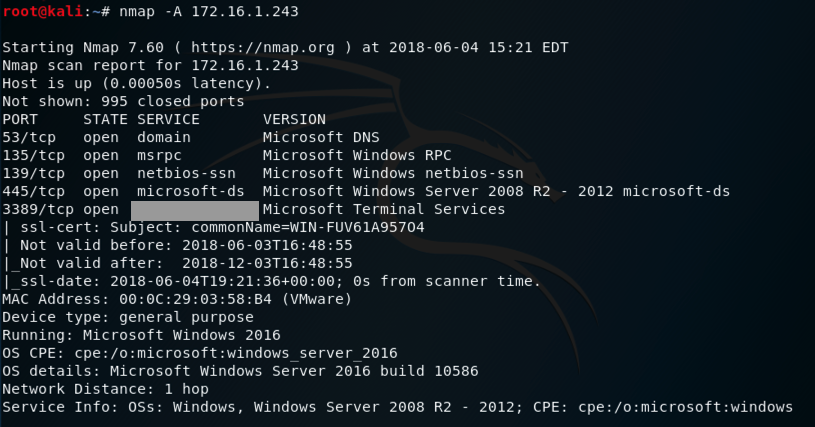
H 410.2: My packets (10 pts)
Find the TCP port on the ad.samsclass.info server that returns this banner: "My packets are your packets."That port number is the flag.
H 410.3: Key to the Universe (15 pts)
Find the TCP port on the ad.samsclass.info server that returns this banner: "The key to the Universe."That port number is the flag.
H 410.4: Key to the Universe (15 pts)
Use rustscan to scan all TCP ports on target1.bowneconsulting.comThe flag is covered by a green rectangle in the image below.
Moved to local server 3-21-19
Forms removed 7-9-19
Generalized to non-cloud servers and renumbered to H 410 6-8-2020
Minor format fix 8-1-2020
Minor edits 4-5-23
Rustscan added 2-2-25