WARNING ABOUT AZURE
If you are using an Azure or other cloud Windows server, this project may cause you to lose access to it. I don't recommend doing it. You may be able to do it by first configuring Google Remote Desktop on the cloud Windows server, but that might not work.
https://tailscale.com/ On the left side, click the "Get started for free" button.
Click "Sign up with Google" and log in to your Google account.
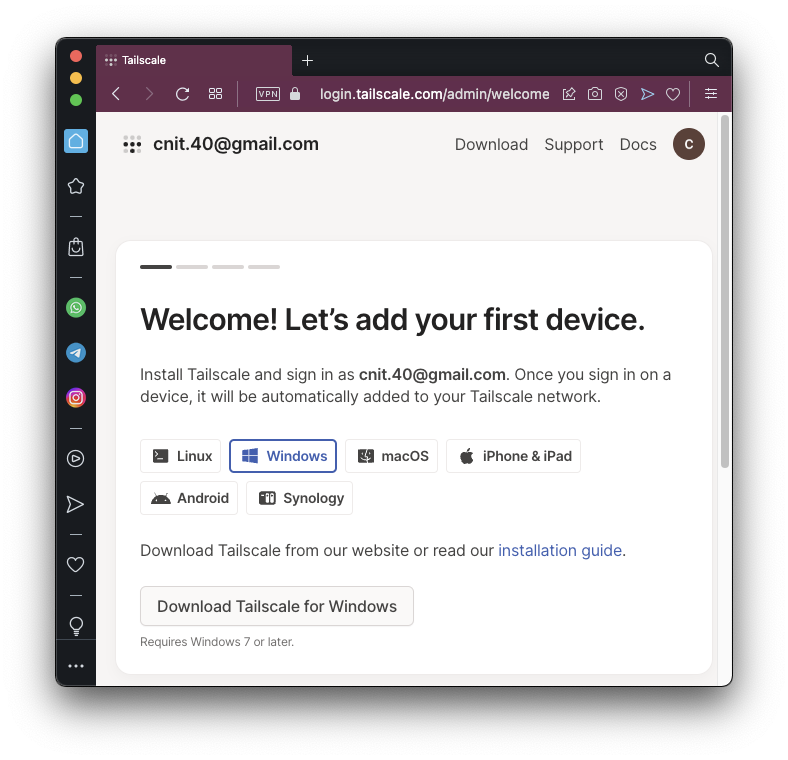
You see the Welcome page shown below.
Click the "Download Tailscale for Windows" button.

On the next page, click the blue "Download Tailscale for Windows" button.
Run the installer you downloaded. When you see the "Installation Succesfully Completed" message, click Close.
In the lower right corner of your desktop, click the up-arrow. Click the Tailscale icon, which is nine dots in a square, outlined in red in the image below.
A Web page opens. Log in with your Google account. Click Connect.
On your Debian Linux server, in a Terminal session, execute these commands:
curl -fsSL https://pkgs.tailscale.com/stable/debian/bullseye.noarmor.gpg \
| sudo tee /usr/share/keyrings/tailscale-archive-keyring.gpg >/dev/null
curl -fsSL https://pkgs.tailscale.com/stable/debian/bullseye.tailscale-keyring.list \
| sudo tee /etc/apt/sources.list.d/tailscale.list
sudo apt update
sudo apt install tailscale -y
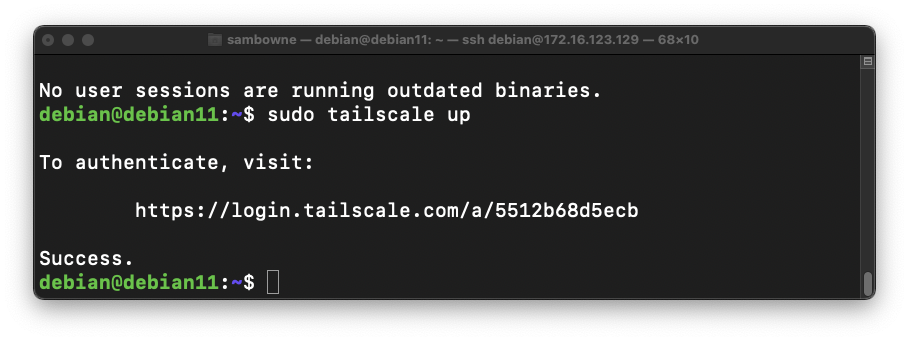
sudo tailscale up
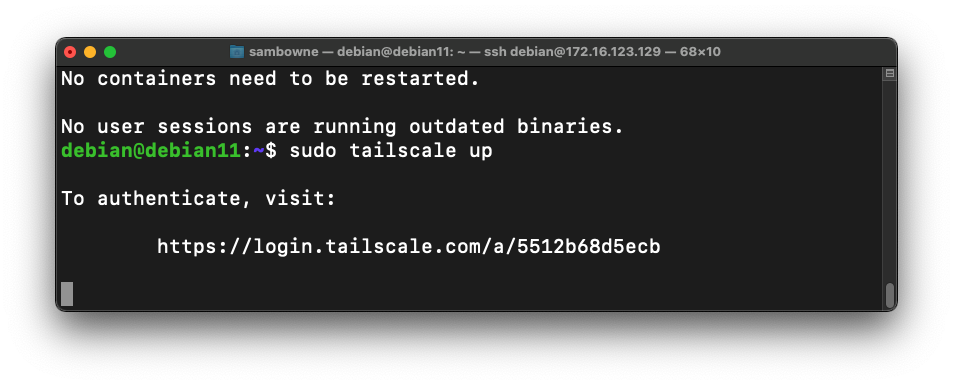
Open that URL in a browser on any machine. Log in to the same Google account you used on Windows.
Click Connect.
The "tailscale up" command finishes, returning a "$" prompt, as shown below.
Now we need to enable IP forwarding and make the Linux machine an exit node.
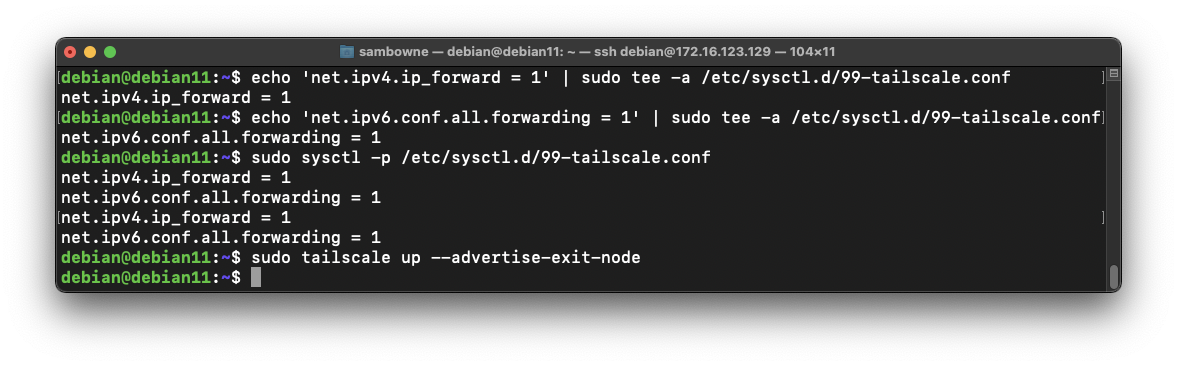
On your Debian Linux server, in a Terminal session, execute these commands:
echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf
echo 'net.ipv6.conf.all.forwarding = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf
sudo sysctl -p /etc/sysctl.d/99-tailscale.conf
sudo tailscale up --advertise-exit-node
https://login.tailscale.com/admin/machines
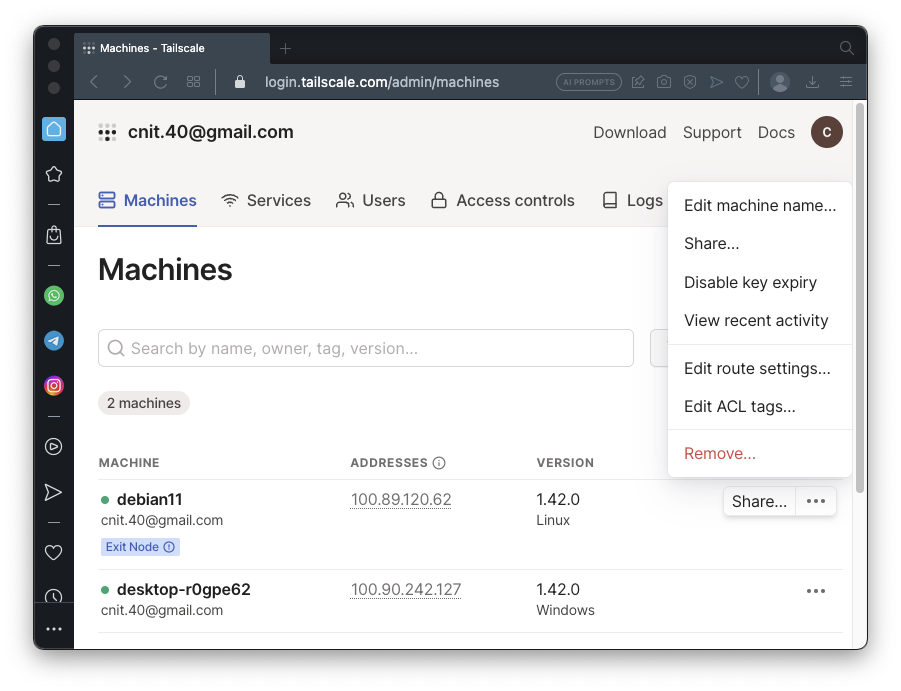
You see two machines, as shown below.
On the "debian11" line, on the right side, click the three-dot icon. Click "Edit route settings...".
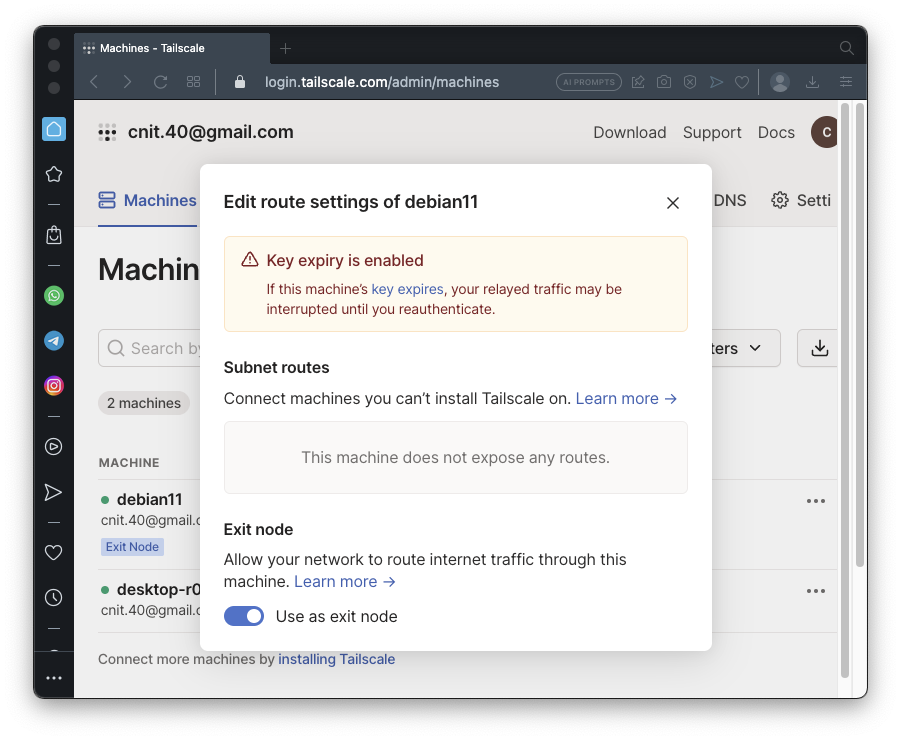
Click the "Use as exit node" slider, as shown below.
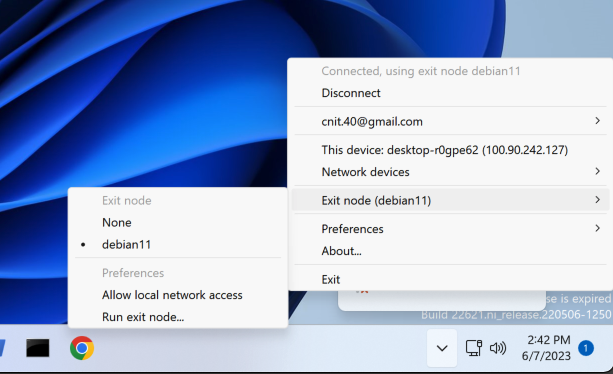
tracert 8.8.8.8
Traffic is being routed through the VPN!
In the main Wireshark window, double-click Ethernet0, or whatever adapter connects to the Internet on your system, as shown below.
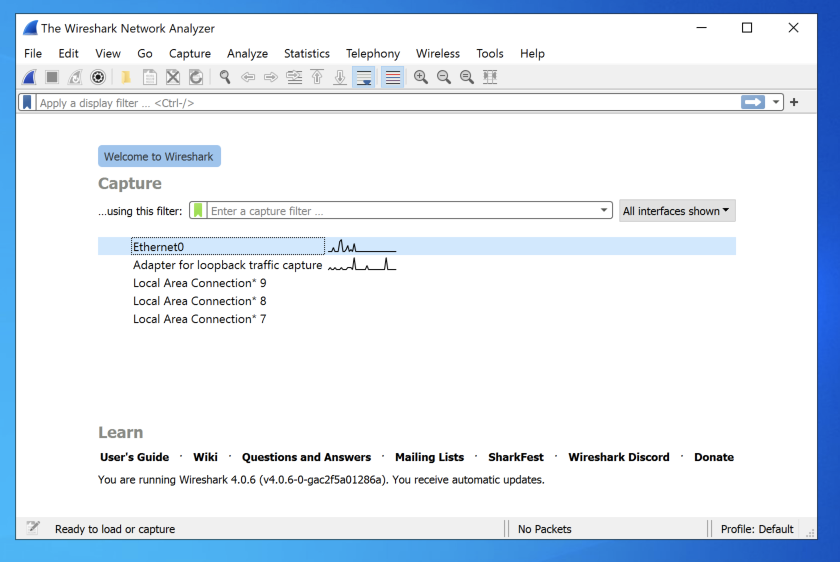
In the the "Capturing from Ethernet0" window, at the top left, in the "Apply a display filter" bar, type this:
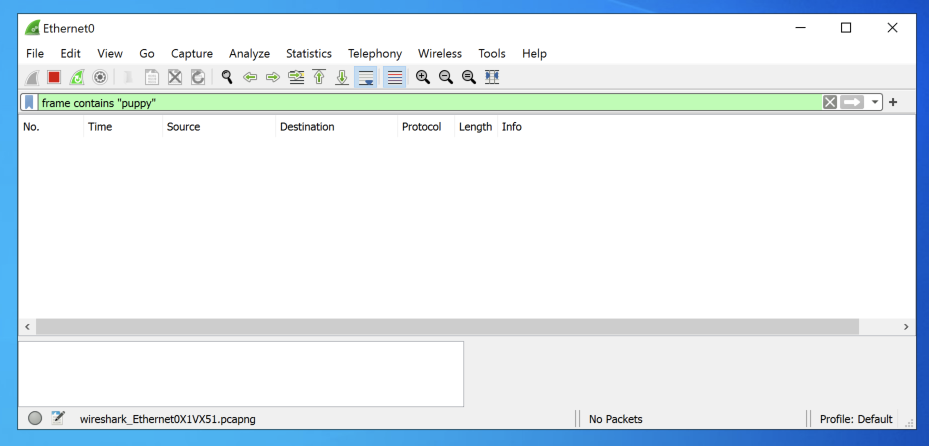
frame contains "puppy"
The filter bar turns green, as shown below.
Wireshark is now listening for any packets containing the word "puppy".
In Settings, search for
secure dns
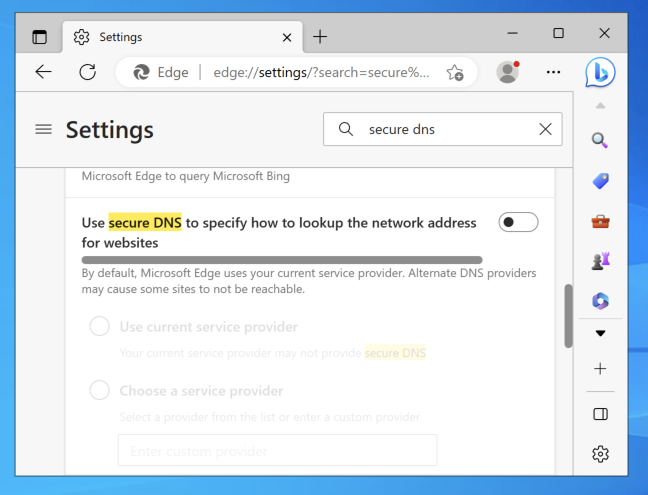
as shown below.
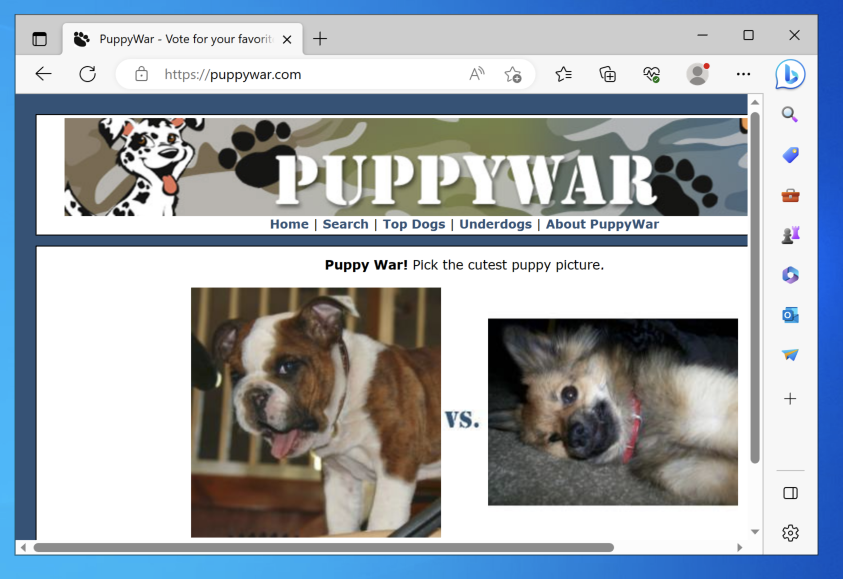
You will likely see some DNS traffic leaking outside the VPN, as shown below.
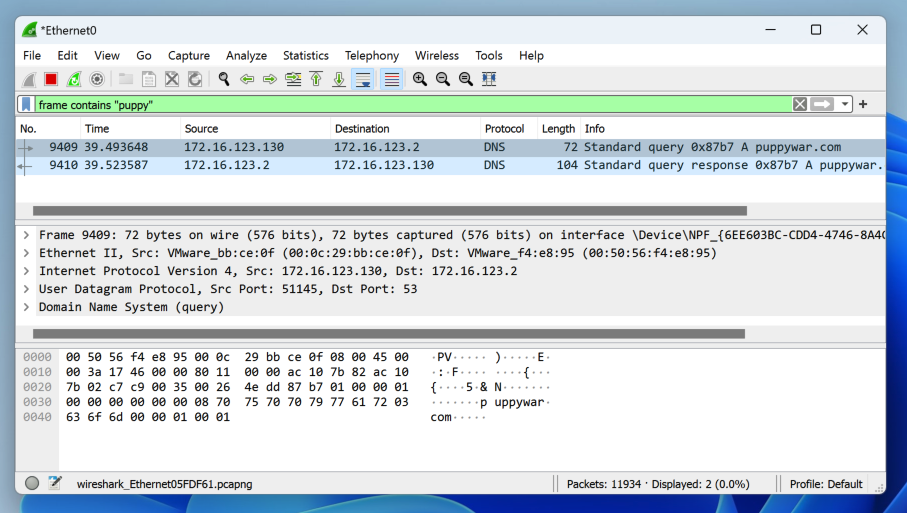
Click Start. Type NETWORK. Click "View network commections".
Right-click Ethernet0 and click Properties.
Double-click "Internet Protocol Version 4 (TCP/IPv4)".
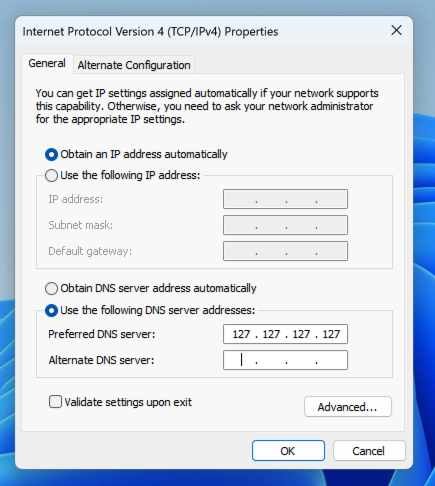
Change the DNS server address to 127.127.127.127, as shown below.
Click OK. Click OK.
Click "Continue without Saving".
Wireshark is listening for new "puppy" packets, as shown below.

as shown below.
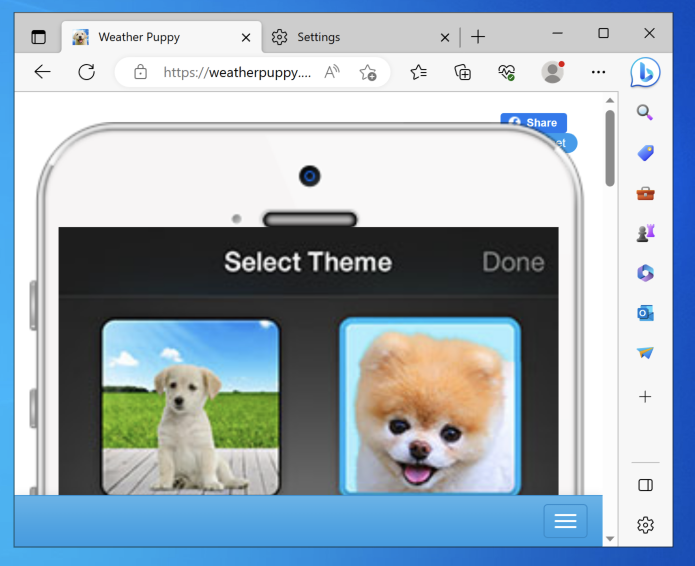
The page loads, and Wireshark doesn't detect any traffic containing "puppy". The leak is fixed!
Flag H 241.1: Adapter Name (15 pts)
On your Windows machine, click Start and type CMD. Open a Command Prompt and execute this command:The flag is covered by a green rectangle in the image below.
Posted 6-7-23
Old project note added 10-30-25