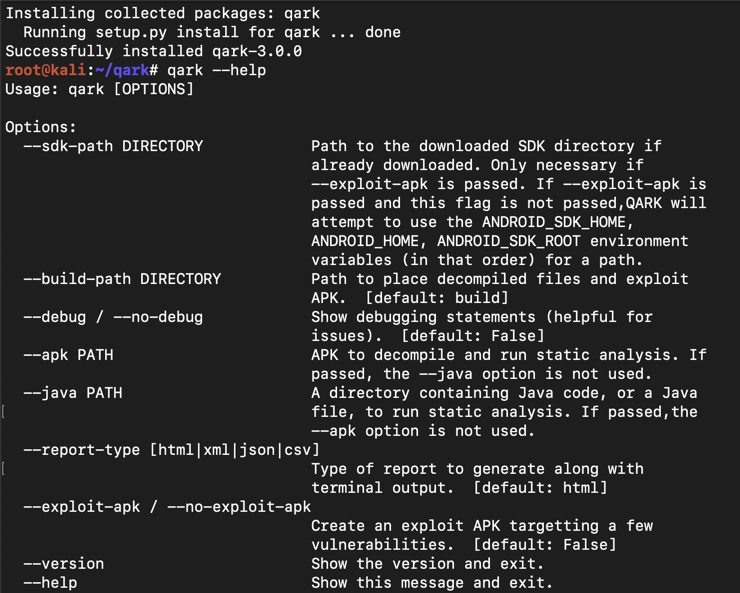
You see a Qark help message, as shown below.您会看到Qark帮助消息,如下所示。git clone https://github.com/linkedin/qark git clone https://github.com/linkedin/qark cd qark cd qark pip install -r requirements.txt pip install -r requirements.txt pip install .点子安装。 qark --help qark --help

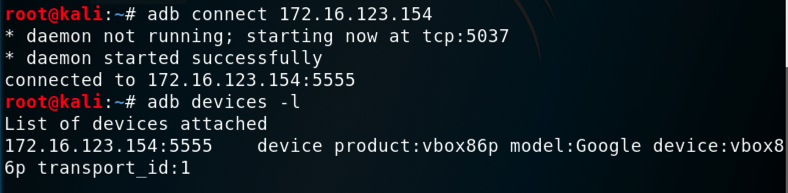
You should see your Genymotion device in the "List of devices attached", as shown below.您应该在“附加设备列表”中看到您的Genymotion设备,如下所示。adb connect 172.16.123.154 adb connect 172.16.123.154 adb devices -l adb devices -l

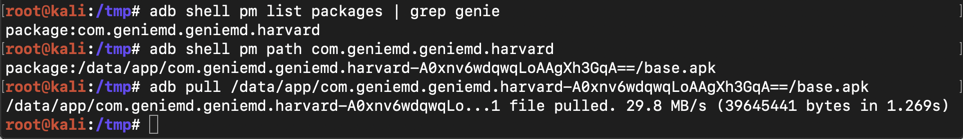
To see the complete package name, on Kali, execute this command:要查看完整的软件包名称,请在Kali上执行以下命令:
The reply shiows the package name, as shown below.回复显示包名称,如下所示。 Use that package name in the next command to get the APK path:在下一个命令中使用该包名称来获取APK路径:adb shell pm list packages | adb shell pm list packages | grep genie grep genie
adb shell pm path com.geniemd.geniemd.harvard adb shell pm path com.geniemd.geniemd.harvard
adb pull /data/app/com.geniemd.geniemd.harvard-A0xnv6wdqwqLoAAgXh3GqA==/base.apk adb pull /data/app/com.geniemd.geniemd.harvard-A0xnv6wdqwqLoAAgXh3GqA==/base.apk
qark --apk base.apk qark --apk base.apk
After the report is generated, move it to a more convenient location and name with this command:生成报告后,将其移动到更方便的位置并使用以下命令命名:
mv /usr/local/lib/python2.7/dist-packages/qark/report/report.html genie.html mv /usr/local/lib/python2.7/dist-packages/qark/report/report.html genie.html
Navigate to the genie.htm file, as shown below, and double-click it.导航到genie.htm文件,如下所示,然后双击它。
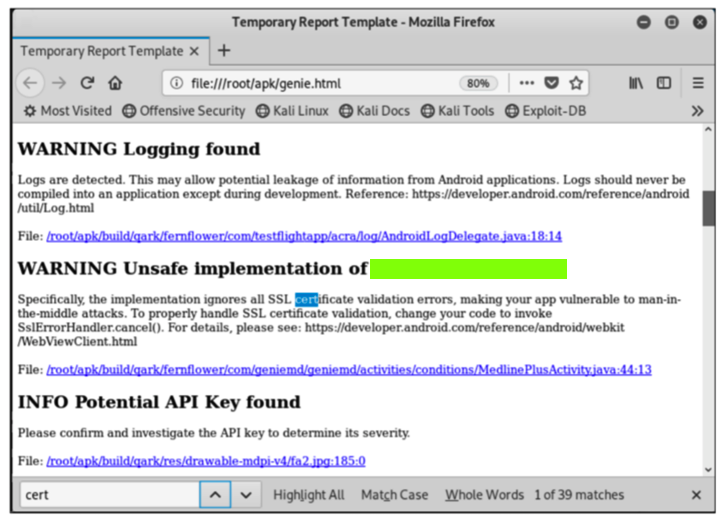
The report opens in Firefox, as shown below.该报告在Firefox中打开,如下所示。
Type Ctrl+F and search for cert to find the SSL certificate validation error, as shown below.键入Ctrl + F并搜索cert以查找SSL证书验证错误,如下所示。