

Archived APK存档APK
This project requires the 2016 version of the app, which was the version in Google Play in April, 2019, when I wrote this project.该项目需要2016版本的应用程序,这是我在2019年4月编写此项目时的Google Play版本。 If that version is no longer available, use this archived copy of the app:如果该版本不再可用,请使用此应用程序的存档副本:
Fill in the form, as shown below, but don't click the " Sign Up " button yet.填写表格,如下所示,但不要点击“ 注册 ”按钮。

https://www.wireshark.org/ https://www.wireshark.org/
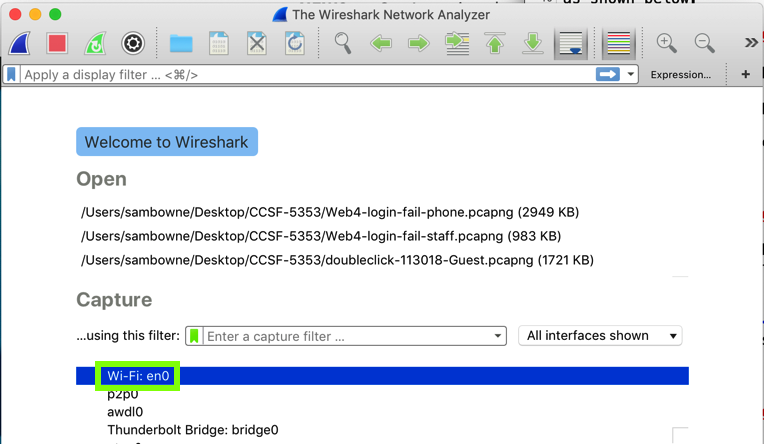
In the main Wireshark window, double-click the network interface that is being used to reach the Internet.在Wireshark主窗口中,双击用于访问Internet的网络接口。 On my system, it is " Wi-Fi: en0 ", outlined in green in the image below.在我的系统上,它是“ Wi-Fi:en0 ”,在下图中以绿色标出 。
Wirehark starts displaying packets. Wirehark开始显示数据包。 At the top, in the Filter bar, enter this display filter:在顶部,在过滤器栏中,输入以下显示过滤器:
http HTTP
On your Android device, in EquityPandit, click the " Sign Up " button.在您的Android设备上,在EquityPandit中,单击“ 注册 ”按钮。
In Wireshark, two POST requests appear, as shown below.在Wireshark中,出现两个POST请求,如下所示。
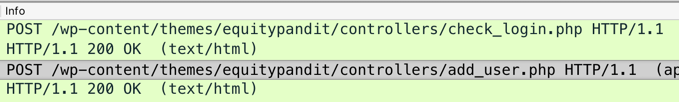
Right-click the second POST request, the one calling "add_user.php", and click Follow , " TCP Stream ".右键单击第二个POST请求,即调用“add_user.php”的请求,然后单击Follow ,“ TCP Stream ”。
The request appears, as shown below, containing your username and password in plaintext.如下所示,请求显示包含明文用户名和密码的请求。
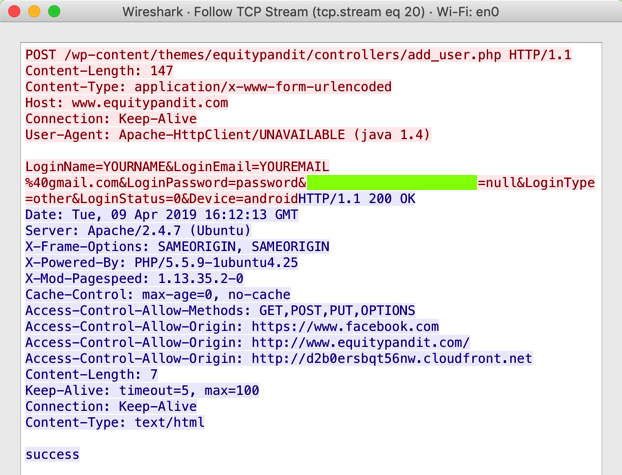
To record your success, enter that flag into the scoring engine at the top of the main course page.要记录您的成功,请将该标志输入主课程页面顶部的评分引擎。
Execute a login request.执行登录请求。 The flag is the domain name of the server it sends a POST request to.该标志是它发送POST请求的服务器的域名。
Execute a login request.执行登录请求。 The flag is the domain name of the server it attempts to connects to.该标志是它尝试连接的服务器的域名。
From Kali, connect to your Android device with adb connect .从Kali,使用adb connect连接到您的Android设备。
If you are not root, first root your device.如果您不是root用户,请首先root设备。 To root BlueStacks, see a later project.要根BlueStacks,请参阅以后的项目。
Open a shell on the Android device with adb shell使用adb shell在Android设备上打开shell
Now you can use normal Bash commands, including these:现在您可以使用普通的Bash命令,包括:
Find the locally stored copy of your password.查找本地存储的密码副本。 The name of the file containing it is the flag.包含它的文件的名称是标志。ls LS cd光盘 pwd PWD find找 grep grep的 nano纳米 more更多 date日期 whoami我是谁
From Kali, find your Android device with the netdiscover command.从Kali,使用netdiscover命令找到您的Android设备。
Connect to it with adb connect .使用adb connect连接到它。
View the log with adb logcat使用adb logcat查看日志
Find your password in the log, as shown below.在日志中找到您的密码,如下所示。 The flag is the word covered by a green box in the image below.标志是下图中绿色框所覆盖的单词。
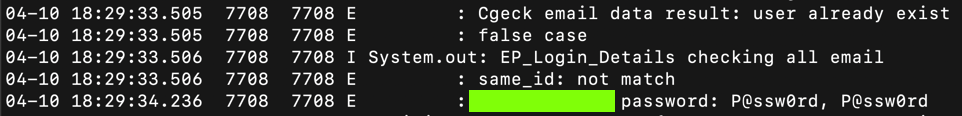
Find my password.找到我的密码。 My password is the flag.我的密码是标志。
Note: don't perform any scans or attacks against any server--we don't have authorization for that. 注意:不要对任何服务器执行任何扫描或攻击 - 我们没有授权。 It is possible to get my password by using the app itself, without performing any attack at all. 可以通过使用应用程序本身来获取我的密码,而不会执行任何攻击。
If you have any questions, talk to your supervisor or your instructor before taking any questionable actions.如果您有任何疑问,请在采取任何可疑行动之前与您的主管或教师联系。