
This is such a serious security flaw that the FTC punished Fandango and Credit Karma for doing the same thing in 2014 .这是一个严重的安全漏洞, FTC惩罚Fandango和Credit Karma在2014年做同样的事情 。
A31a: Burp and Genymotion on Mac or Linux A31a:Mac或Linux上的Burp和Genymotion
A31b: Burp and Nox on Windows A31b:Windows上的Burp和Nox
Install the " Harvard Health Info " app, as shown below.安装“ 哈佛健康信息 ”应用程序,如下所示。

Troubleshooting故障排除
If Google Play won't connect, you are probably using the proxy.如果Google Play无法连接,您可能正在使用代理。In Settings, tap Wi-Fi , and adjust the networking to use a proxy of None .在“设置”中,点按“ Wi-Fi” ,然后调整网络以使用“ 无”代理。
Archived App存档的应用程序
If the app is unavailable, use this archived copy .如果应用程序不可用,请使用此存档副本 。
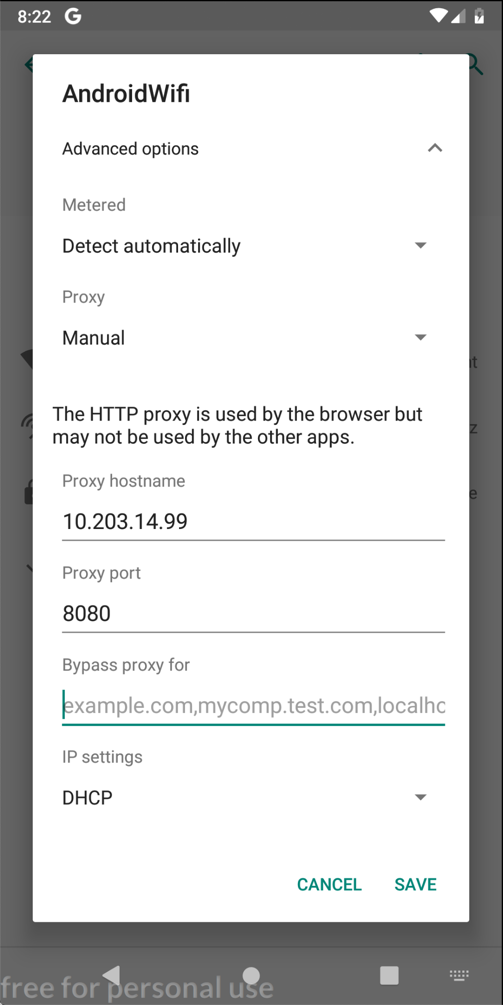
On your Android device, click SAVE .在Android设备上,单击“ 保存” 。
At the bottom center of the device, click the round Home button.在设备的底部中心,单击圆形主页按钮。
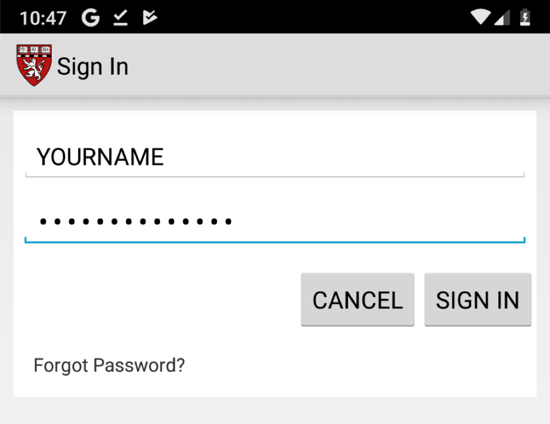
Click " Sign in " and enter test credentials, as shown below.单击“ 登录 ”并输入测试凭据,如下所示。

Click " SIGN IN ".点击“ 登录 ”。
In Burp, on the Proxy tab, click the " HTTP Requests " sub-tab.在Burp的“代理”选项卡上,单击“ HTTP请求 ”子选项卡。
Find the POST method going to /GenieMD.Com/resources/Email/SignIn.找到转到/GenieMD.Com/resources/Email/SignIn的POST方法。
The username and password appear in Burp, as shown below:用户名和密码显示在Burp中,如下所示:

If you have been doing these projects in order, and you are using a Mac, this is not a security problem, because you have the PortSwigger certificate installed--your Android device has been told to trust Burp.如果您按顺序执行这些项目,并且使用的是Mac,则这不是安全问题,因为您已安装了PortSwigger证书 - 您的Android设备已被告知要信任Burp。
In Burp, on the Proxy tab, on the " HTTP history " sub-tab, right-click any entry and click " Clear history ".在Burp中,在“ 代理”选项卡上的“ HTTP历史记录 ”子选项卡上,右键单击任何条目,然后单击“ 清除历史记录 ”。 Click Yes .单击是 。
If you are using a Mac or Linux host, do this:如果您使用的是Mac或Linux主机,请执行以下操作:
On your Android device, in Settings, click " Security & location ", Advanced , " Encryption & credentials ", " Clear credentials ".在Android设备上的“设置”中,点击“ 安全和位置 ”, 高级 ,“ 加密和凭据 ”,“ 清除凭据 ”。
Click OK .单击确定 。
Enter your PIN.输入您的PIN码。
You should see an error message, as shown below.您应该看到一条错误消息,如下所示。
(When I did this on an Android 9.0 Genymotion device, the green padlock remained visible, even though the page would not load; another Android bug.) (当我在Android 9.0 Genymotion设备上执行此操作时,绿色挂锁仍然可见,即使页面无法加载;另一个Android错误。)
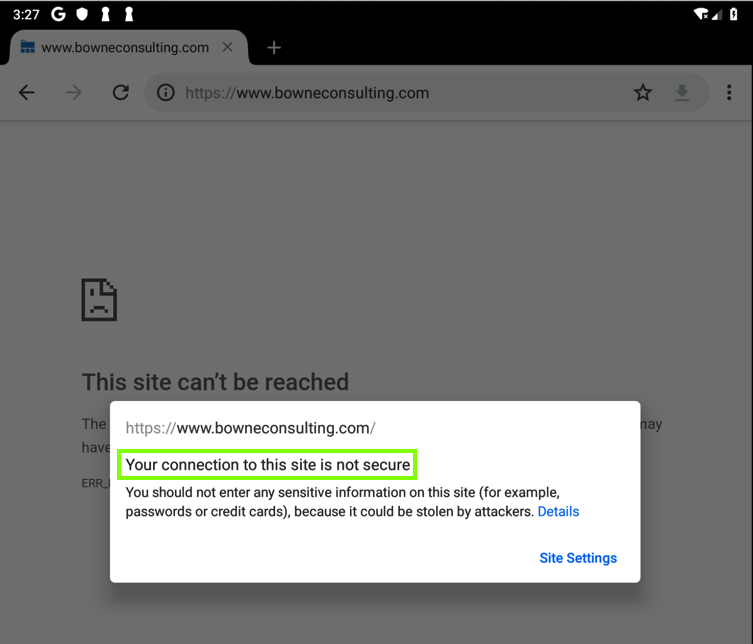
No valid HTTPS connections can be made from your device now, because it no longer trusts Burp.现在无法从您的设备进行有效的HTTPS连接,因为它不再信任Burp。
Click " Sign in " and enter test credentials, including your name, as shown below.单击“ 登录 ”并输入测试凭据,包括您的姓名,如下所示。
Find the POST method going to /GenieMD.Com/resources/Email/SignIn.找到转到/GenieMD.Com/resources/Email/SignIn的POST方法。
The username and password still appear in Burp, as shown below:用户名和密码仍显示在Burp中,如下所示:

This is a big problem--the MITM attack is allowed.这是一个大问题 - 允许MITM攻击。 GenieMD exposes its users to this attack, because they don't bother to validate SSL certificates. GenieMD将其用户暴露给此攻击,因为他们无需验证SSL证书。
The flag is the text covered by a green box in the image below.标志是下图中绿色框所覆盖的文本。
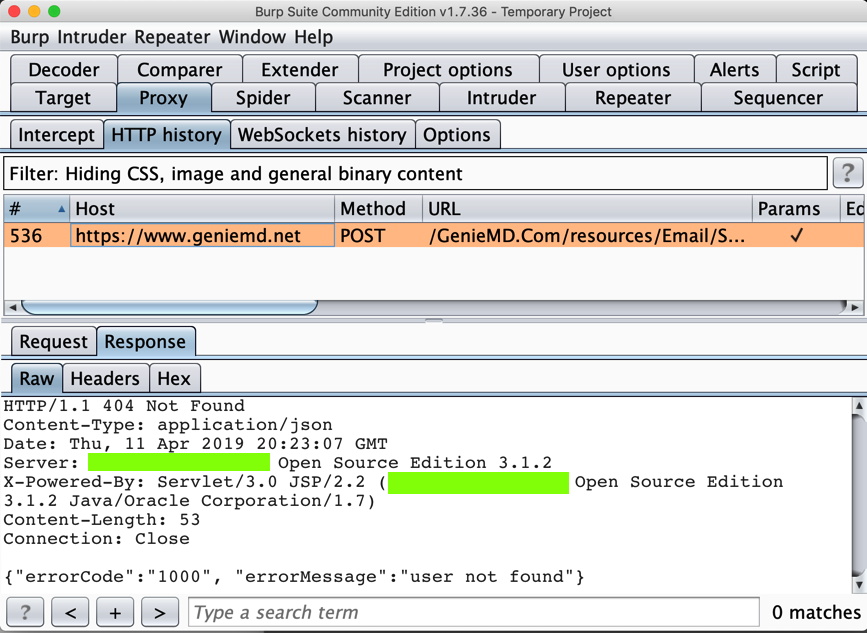
Execute a login request.执行登录请求。 The flag is the domain name of the server it sends a POST request to.该标志是它发送POST请求的服务器的域名。
It asks for a registration code.它要求注册码。
On your Kali machine, execute this command to unpack the app:在您的Kali机器上,执行此命令以解压缩应用程序:
apktool d A31.2.apk apktool d A31.2.apk