In a Web browser, go to https://portswigger.net/burp在Web浏览器中,转到https://portswigger.net/burp
In the "Community Edition" column, click Download ", as shown below.在“社区版”列中,单击“ 下载 ”,如下所示。

Install the software with the default options.使用默认选项安装软件。
Click Start , " Burp Suite Community Edition ".单击开始 ,“ Burp Suite Community Edition ”。
An agreement appears.出现协议。 Click " I Accept ".点击“ 我接受 ”。
In the next page, click the Start Burp button.在下一页中,单击Start Burp按钮。
The main Burp window opens, as shown below.主Burp窗口打开,如下所示。
Click the Proxy tab.单击“ 代理”选项卡。 Click the Intercept sub-tab.单击“ 拦截”子选项卡。
The third button says " Intercept is on ", as shown below.第三个按钮显示“ 拦截打开 ”,如下所示。
On the Proxy tab, click the Options sub-tab.在“ 代理”选项卡上,单击“ 选项”子选项卡。
In the central box, click the Interface address to highlight it, as shown below.在中央框中,单击接口地址以突出显示它,如下所示。

On the left side, click the Edit button.在左侧,单击“ 编辑”按钮。
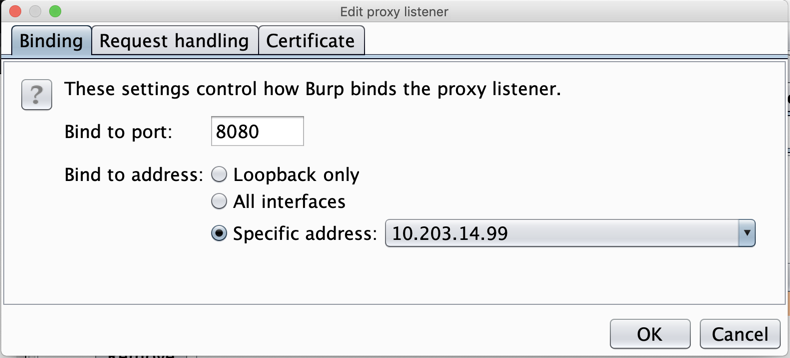
In the "Edit proxy listener" box, click the " Specific address " button, and select your computer's IP address that is used to connect to the Internet, as shown below.在“编辑代理侦听器”框中,单击“ 特定地址 ”按钮,然后选择用于连接到Internet的计算机的IP地址,如下所示。
Click OK .单击确定 。
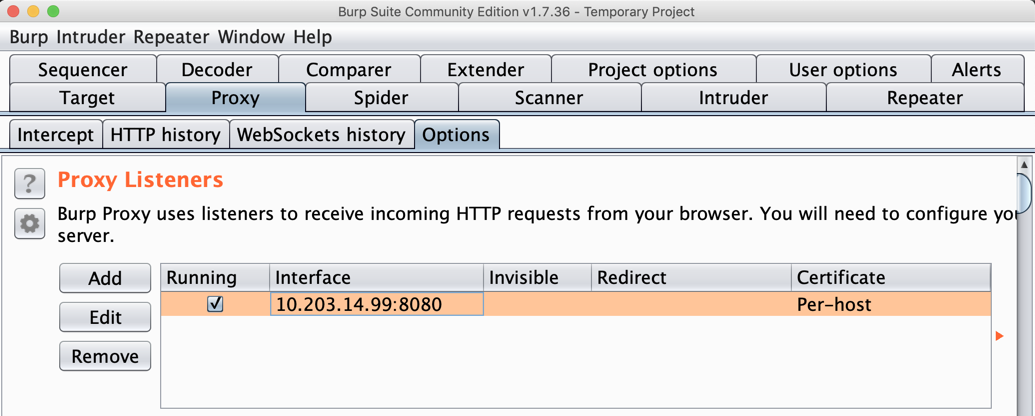
Burp shows a proxy listener on your IP address and port 8080, as shown below. Burp在您的IP地址和端口8080上显示代理侦听器,如下所示。
Make a note of this address--you will need it below.记下这个地址 - 下面你需要它。
https://www.bignox.com/ https://www.bignox.com/
Download and install the Nox emulator.下载并安装Nox仿真器。 When it launches, click " Skip Tutorial ".启动时,单击“ 跳过教程 ”。
Click OK .单击确定 。
Nox launches, as shown below. Nox发布,如下所示。

On the lower right, in the black bar of icons, click the second icon from the bottom, which is shaped like an envelope.在右下方的黑色图标栏中,单击底部的第二个图标,形状像信封。
The Nox home page opens, as shown below.将打开Nox主页,如下所示。

On the Nox home page, click Tools .在Nox主页上,单击“ 工具” 。
Click Settings .单击设置 。
In Settings, click Wi-Fi , as shown below.在“设置”中,单击“ Wi-Fi” ,如下所示。

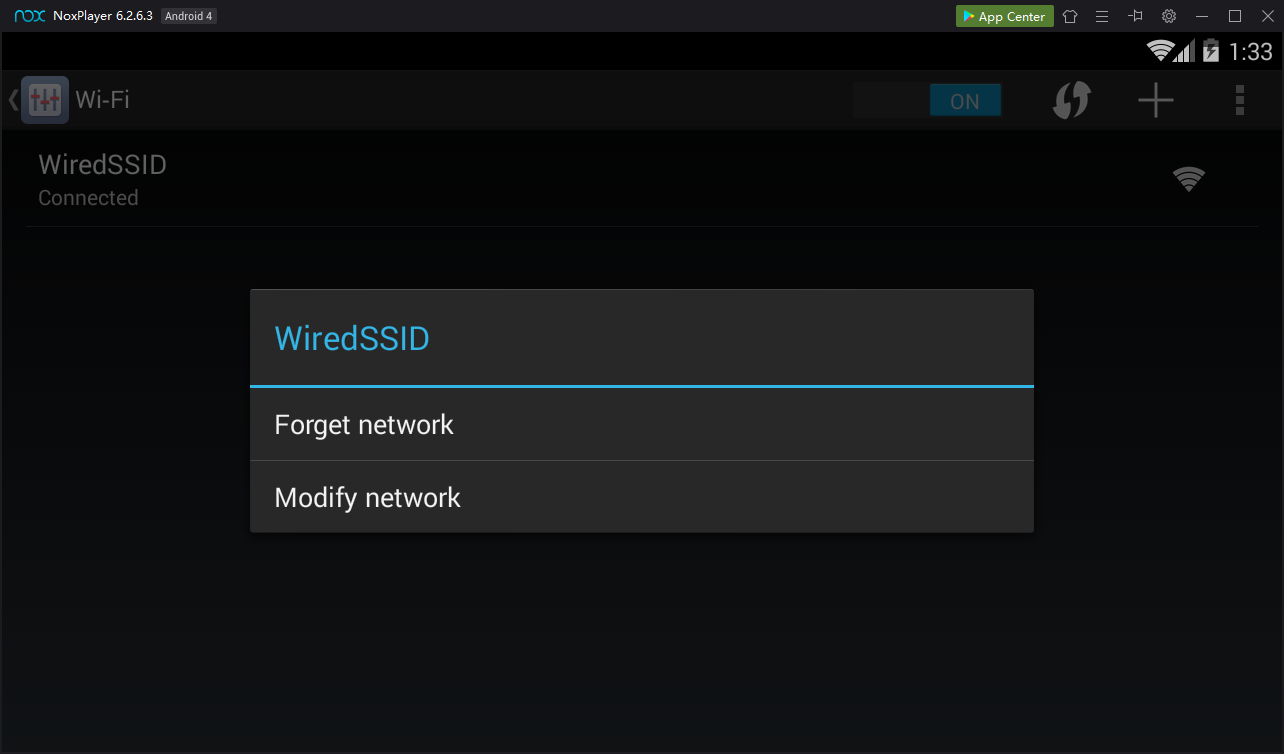
On the next screen, point to WiredSSD .在下一个屏幕上,指向WiredSSD 。 Press and hold down the left mouse button.按住鼠标左键。
A "WiredSSD" box pops up, as shown below.弹出“WiredSSD”框,如下图所示。
Click " Modify network ".单击“ 修改网络 ”。
In the "WiredSSD" box, click the " Show advanced options " box.在“WiredSSD”框中,单击“ 显示高级选项 ”框。
Scroll down and set the Proxy type to Manual .向下滚动并将代理类型设置为手动 。
Enter the IP address you set in Burp above, and a port of 8080 , as shown below.输入您在上面的Burp中设置的IP地址,以及一个8080的端口,如下所示。
Click Save .单击保存 。

On the Nox home page, at the top left, click Browser .在Nox主页的左上角,单击“ 浏览器” 。
A "Security warning" box pops up, as shown below.弹出“安全警告”框,如下所示。
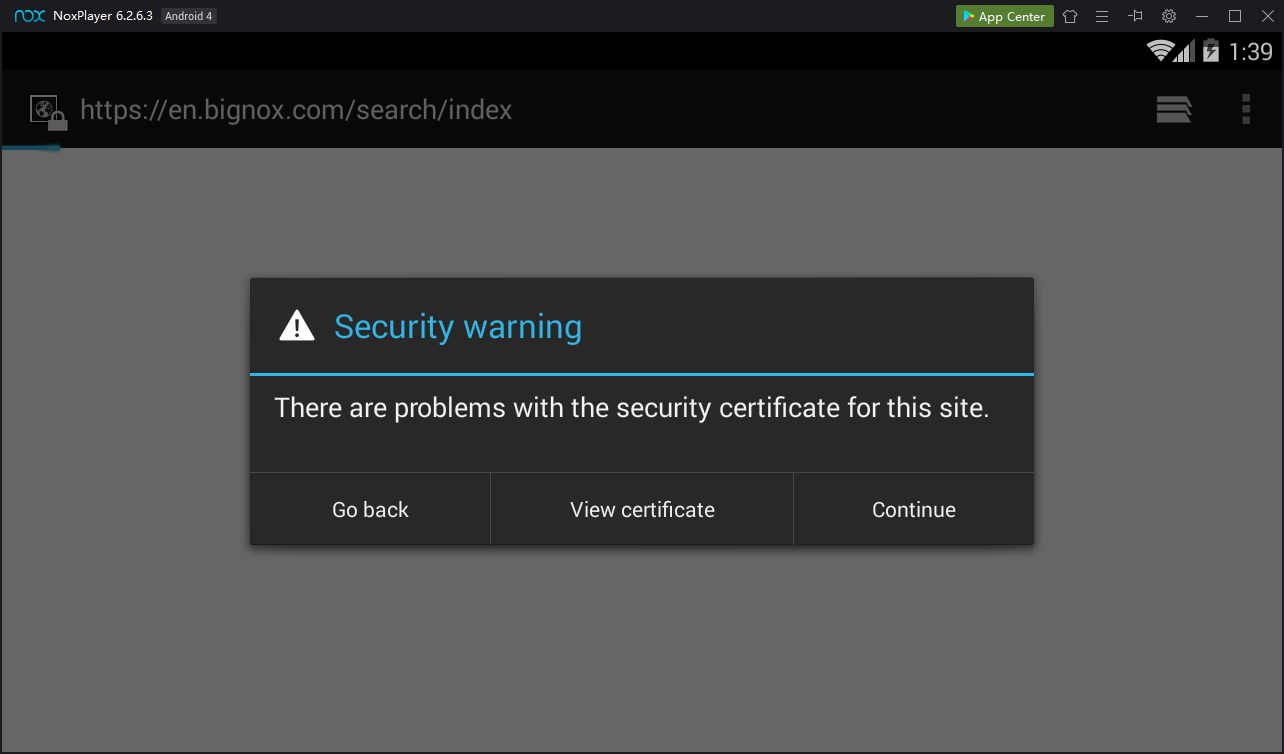
This is good!这很好! Burp is performing a man-in-the-middle attack and the Android browser is detecting it. Burp正在进行一次中间人攻击,Android浏览器正在检测它。
In the "Security warning" box, click Continue as many times as necessary, to get the boxes out of the way.在“安全警告”框中,根据需要多次单击“ 继续 ”,以使框不碍事。
When you can get to the address bar, enter this address:当您可以到达地址栏时,请输入以下地址:
ad.samsclass.info ad.samsclass.info
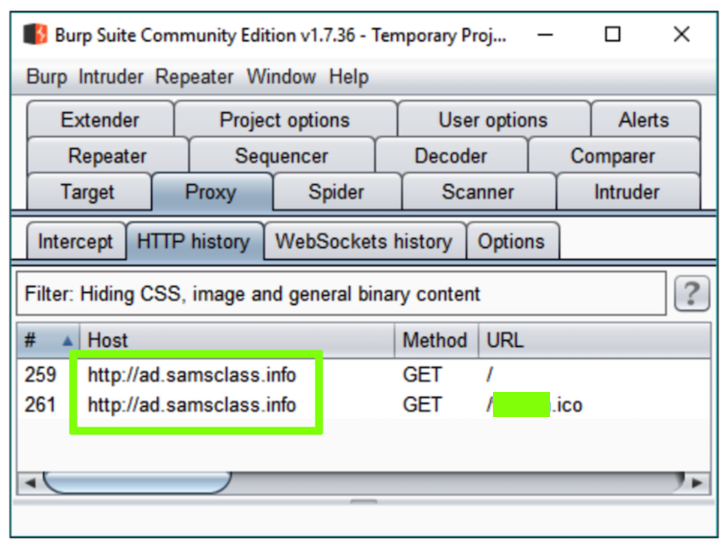
A web page opens, as shown below.将打开一个网页,如下所示。
Scroll down and find traffic to ad.samsclass.info as shown below.向下滚动并查找ad.samsclass.info的流量,如下所示。