Equity Pandit权益Pandit
So please use one of these apps instead.因此,请使用其中一个应用程序。 They all used plaintext network transmission on Feb 10, 2019, but eventually they may be fixed or removed.它们都在2019年2月10日使用了明文网络传输,但最终它们可能被修复或删除。
Equity Pandit权益Pandit
|
Archived APK存档APK
If you don't have access to Google Play, use this archived copy of the app:如果您无法访问Google Play,请使用此应用的存档副本:
https://www.wireshark.org/ https://www.wireshark.org/
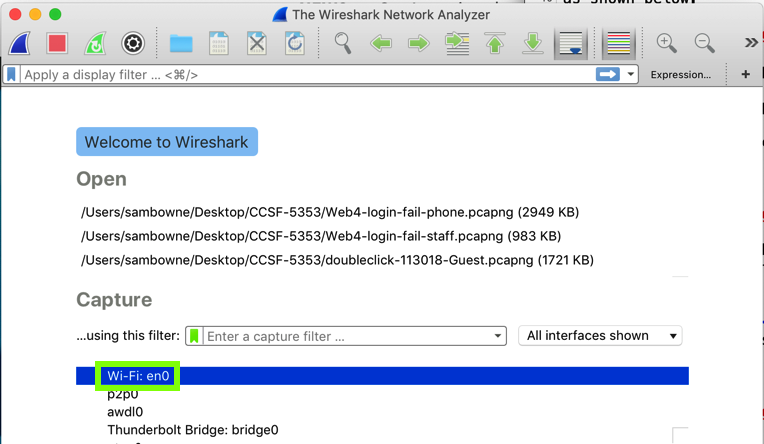
In the main Wireshark window, double-click the network interface that is being used to reach the Internet.在Wireshark主窗口中,双击用于访问Internet的网络接口。 On my system, it is " Wi-Fi: en0 ", outlined in green in the image below.在我的系统上,它是“ Wi-Fi:en0 ”,在下图中以绿色标出 。
Wirehark starts displaying packets. Wirehark开始显示数据包。 At the top, in the Filter bar, enter this display filter:在顶部,在过滤器栏中,输入以下显示过滤器:
http HTTP
On your Android device, in the vulnerable app, use the "Create Account" page to make an account.在您的Android设备上,在易受攻击的应用中,使用“创建帐户”页面来创建帐户。
Wireshark shows a captured POST request, as shown below. Wireshark显示捕获的POST请求,如下所示。
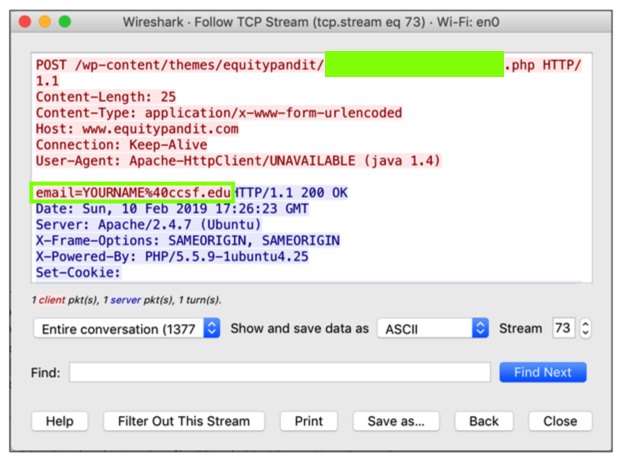
In the top pane of Wireshark, right-click the POST request, and click Follow , " TCP Stream ", as shown above.在Wireshark的顶部窗格中,右键单击POST请求,然后单击Follow ,“ TCP Stream ”,如上所示。
Troubleshooting故障排除
If you don't see any packets, try these fixes:如果您没有看到任何数据包,请尝试以下修复:
- Click the red square button to stop the capture单击红色方块按钮以停止捕获
- From the menu, click Capture , Options从菜单中,单击“ 捕获” ,“ 选项”
- Choose a different network adapter选择其他网络适配器
- If the "Link-layer header" is set to "802.11...", scroll to the right and uncheck the monitor box如果“链路层标头”设置为“802.11 ...”,请向右滚动并取消选中监视器框
The request appears, containing your credentials, as shown below.将显示包含您的凭据的请求,如下所示。
