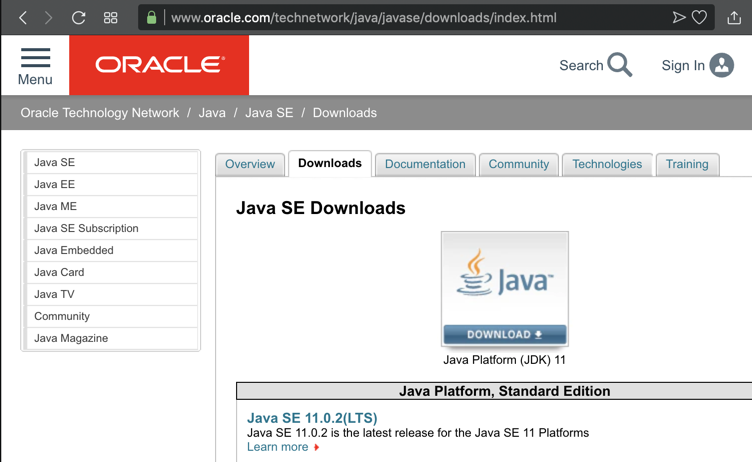

In a Web browser, go to在Web浏览器中,转到
https://www.oracle.com/technetwork/java/javase/downloads/index.html https://www.oracle.com/technetwork/java/javase/downloads/index.html
Click the DOWNLOAD button, as shown below.单击DOWNLOAD按钮,如下所示。

On the next page, download the correct version for your OS, as shown below.在下一页,下载适用于您的操作系统的正确版本,如下所示。
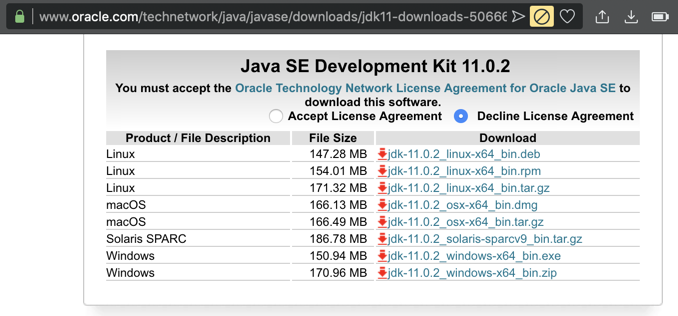
Install the software with the default options, as shown below.使用默认选项安装软件,如下所示。
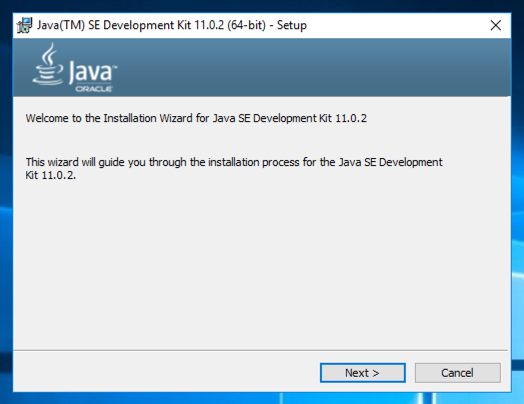
https://ghidra-sre.org/ https://ghidra-sre.org/
Click the " Download Ghidra " button, as shown below.单击“ 下载Ghidra ”按钮,如下所示。 Save the ghidra_9.0_PUBLIC_20190228.zip file in your Downloads folder.将ghidra_9.0_PUBLIC_20190228.zip文件保存在“下载”文件夹中。
Unzip the file.解压缩文件。 In Windows, don't double-click it;在Windows中,不要双击它; that just appears to unzip it.这似乎只是解压缩它。 You must right-click it, click " Extract All... ", and Extract .您必须右键单击它,单击“ Extract All ... ”和Extract 。
If you are on a Mac or Linux, double-click ghidraRun , as shown below.如果您使用的是Mac或Linux,请双击ghidraRun ,如下所示。 If you are using Windows, double-click ghidraRun.bat .如果您使用的是Windows,请双击ghidraRun.bat 。
An agreement pops up.弹出协议。 Click " I Agree ".点击“ 我同意 ”。
Ghidra opens, as shown below. Ghidra打开,如下所示。
In the little "Tip of the Day" box, click the Close button.在“每日提示”框中,单击“ 关闭”按钮。
One by one, right-click the links below and download the files.一个接一个,右键单击下面的链接并下载文件。 Save them in your Downloads folder.将它们保存在Downloads文件夹中。
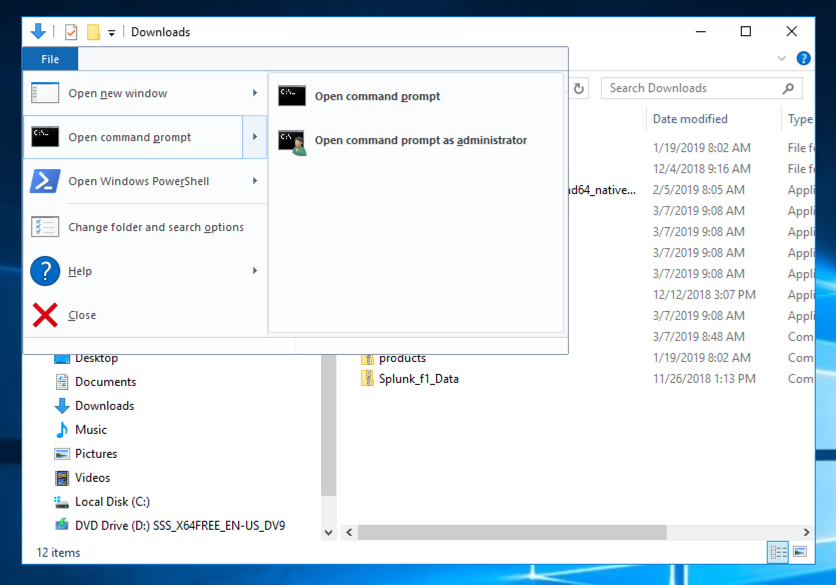
Click Start , " File Explorer ".单击开始 ,“ 文件资源管理器 ”。 In the left pane, click Downloads .在左侧窗格中,单击“ 下载” 。
At the top left of this window, click File , " Open command prompt ", " Open command prompt ", as shown below.在此窗口的左上角,单击文件 ,“ 打开命令提示符 ”,“ 打开命令提示符 ”,如下所示。
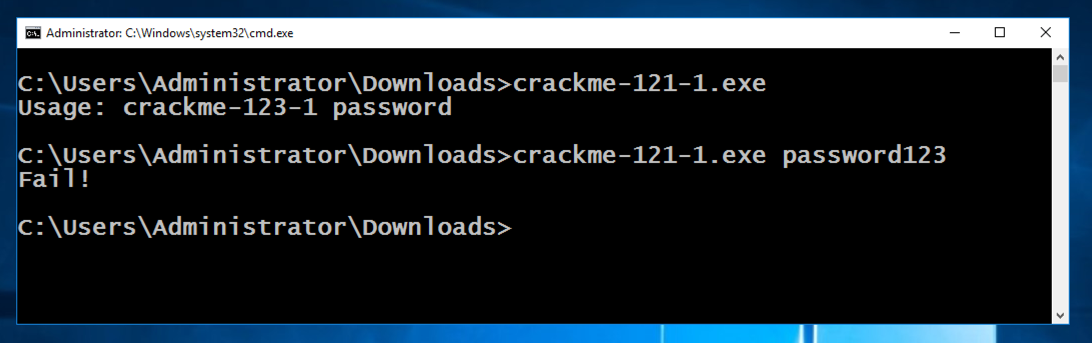
In the Command Prompt, execute these commands:在命令提示符中,执行以下命令:
This is a simple password guessing game.这是一个简单的密码猜谜游戏。 Unless you enter the correct password, it says "Fail!", as shown below.除非您输入正确的密码,否则会显示“失败!”,如下所示。crackme-121-1.exe的crackme-121-1.exe crackme-121-1.exe password123 crackme-121-1.exe密码123
Close the Command Prompt window.关闭命令提示符窗口。
In the "Select Project Type" page, accept the default option of " Non-Shared Project " and click Finish .在“选择项目类型”页面中,接受默认选项“ 非共享项目 ”,然后单击“ 完成” 。
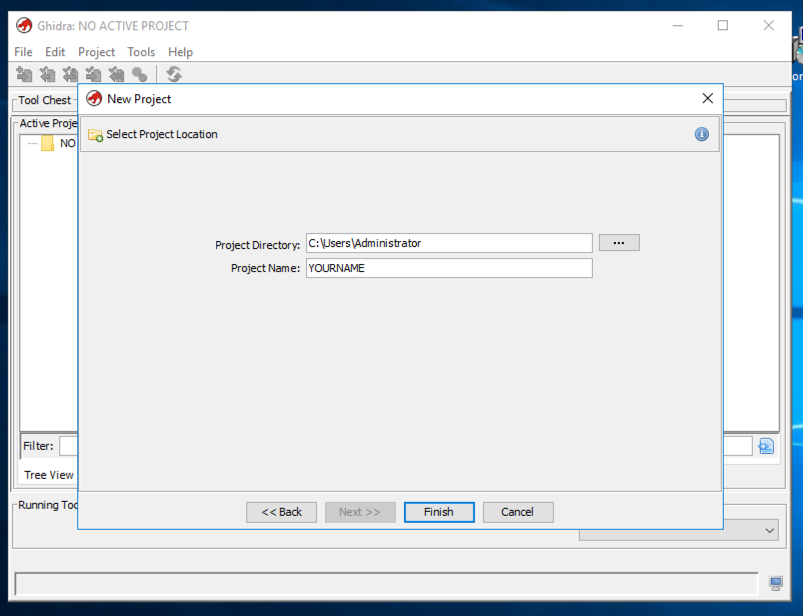
In the "Select Project Location" page, enter your name into the "Project Name" field, as shown below, and click Next>> .在“选择项目位置”页面中,在“项目名称”字段中输入您的名称,如下所示,然后单击下一步>> 。
In the "Ghidra:YOURNAME" window, at the top left, click File , " Import File... ".在“Ghidra:YOURNAME”窗口的左上角,单击“ 文件 ”,“ 导入文件... ”。
In the "Select File to Import" window, double-click Downloads and double-click crackme-121-1.exe .在“选择要导入的文件”窗口中,双击“ 下载” ,然后双击“ crackme-121-1.exe” 。
A box pops up.弹出一个框。 Click OK .单击确定 。
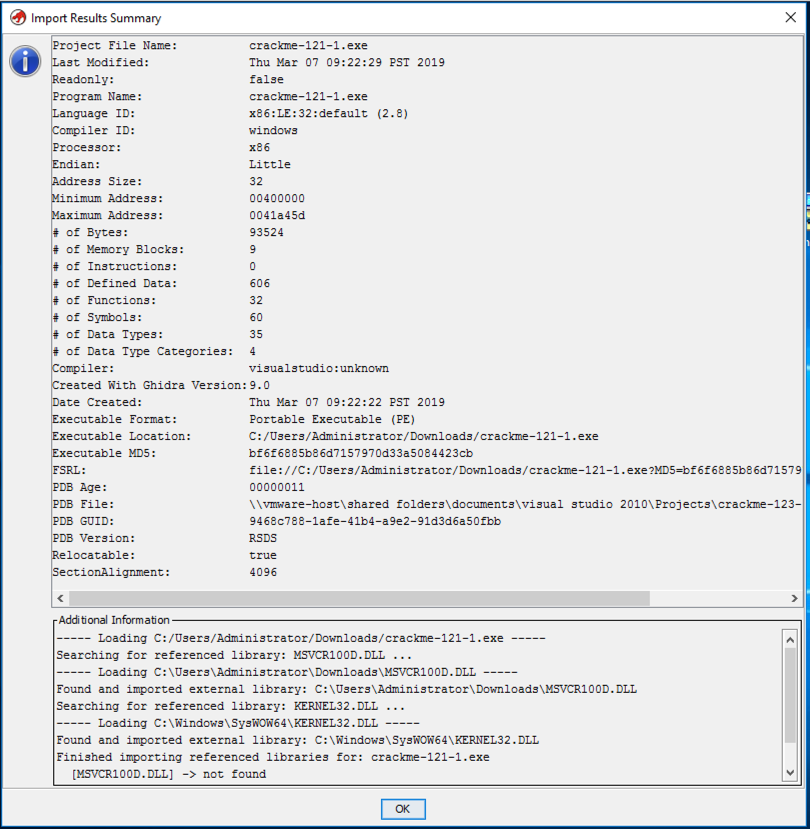
After a few seconds, an "Import Results Summary" box appears, as shown below.几秒钟后,将出现“导入结果摘要”框,如下所示。
Click OK .单击确定 。
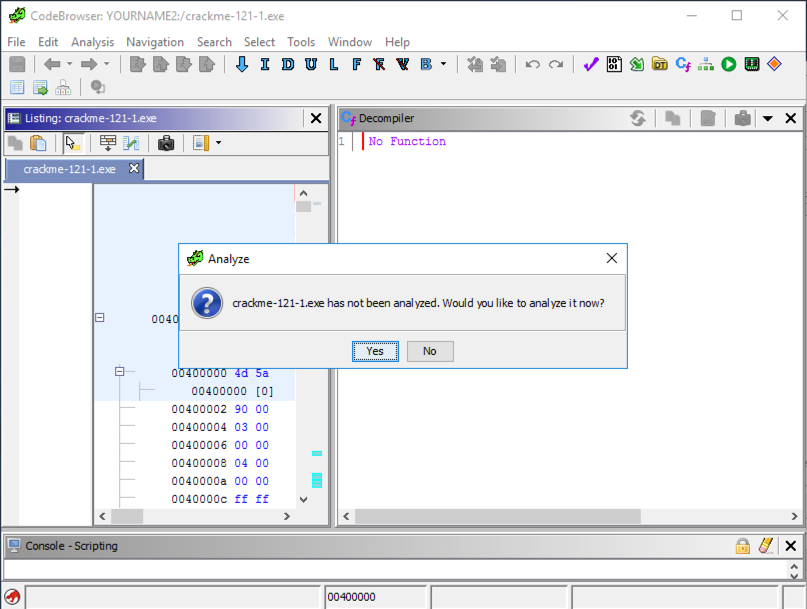
A big window opens, with an "Analyze" box on top, as shown below.打开一个大窗口,顶部有一个“分析”框,如下所示。 In the "Analyze" box, click Yes .在“分析”框中,单击“ 是” 。
In the "Analyze Options" box, click Analyze .在“分析选项”框中,单击“分析”。
In the "Auto-Analysis Summary" box, click OK .在“自动分析摘要”框中,单击“ 确定” 。
The main Ghidra window appears, showing the assembly code for the file in the large central pane, beginning at address 00400000 with the letters "MZ", as shown below.出现主Ghidra窗口,显示大型中央窗格中文件的汇编代码,从地址00400000开始,字母为“MZ”,如下所示。
All Windows executables start with those letters, at that relative address.所有Windows可执行文件都以相对地址的字母开头。
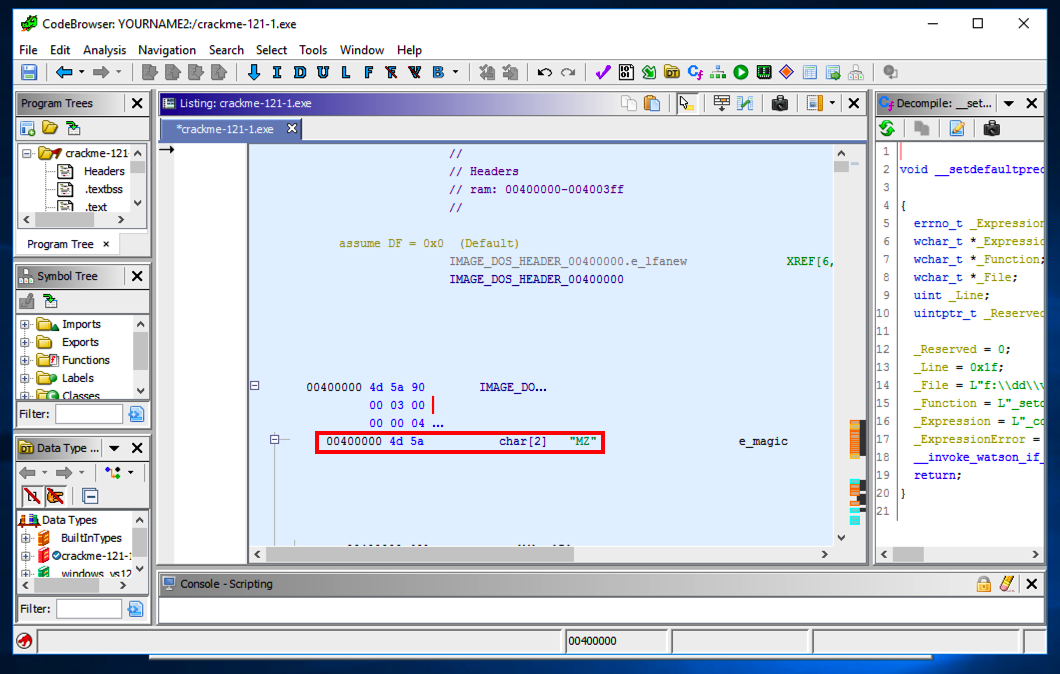
On the right side, a box appears showing readable strings.在右侧,出现一个显示可读字符串的框。
Click Fail!点击失败! . 。
The left pane shows the address where that string is stored, as shown below.左侧窗格显示存储该字符串的地址,如下所示。
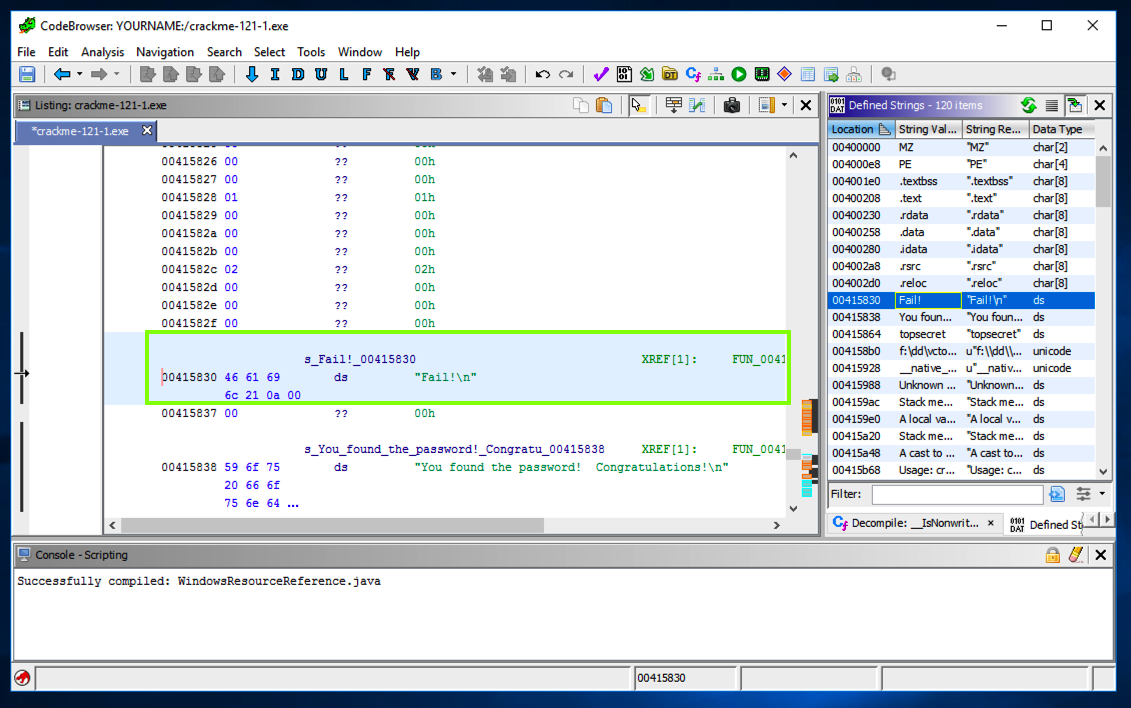
In the left pane, on the line showing the "Fail!\n" string, on the right side, after the "XREF" label, double-click FUN .在左侧窗格中,在显示“Fail!\ n”字符串的行上,在“XREF”标签后的右侧,双击FUN 。
The left pane shows the assembly code that uses this string, with a "PUSH" command, as shown below.左侧窗格显示使用此字符串的汇编代码,带有“PUSH”命令,如下所示。
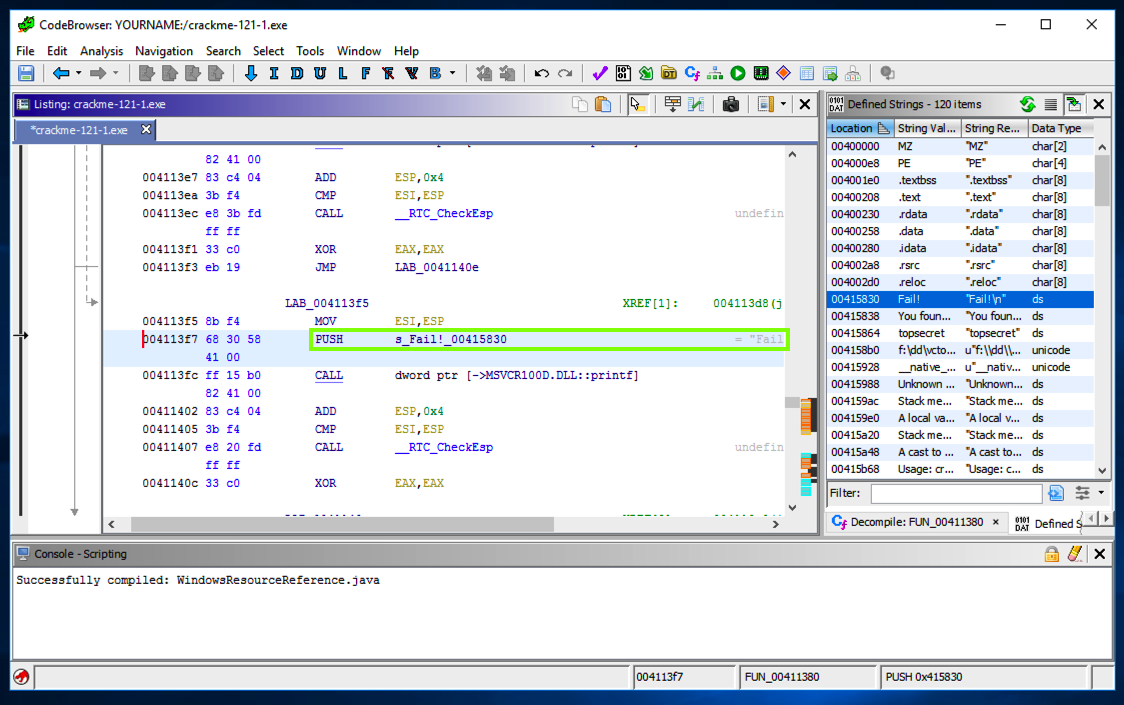
A "Decompile" pane appears, as shown below.将出现“反编译”窗格,如下所示。
This is readable C code, and you can easily see that the password is topsecret这是可读的C代码,您可以很容易地看到密码是topsecret
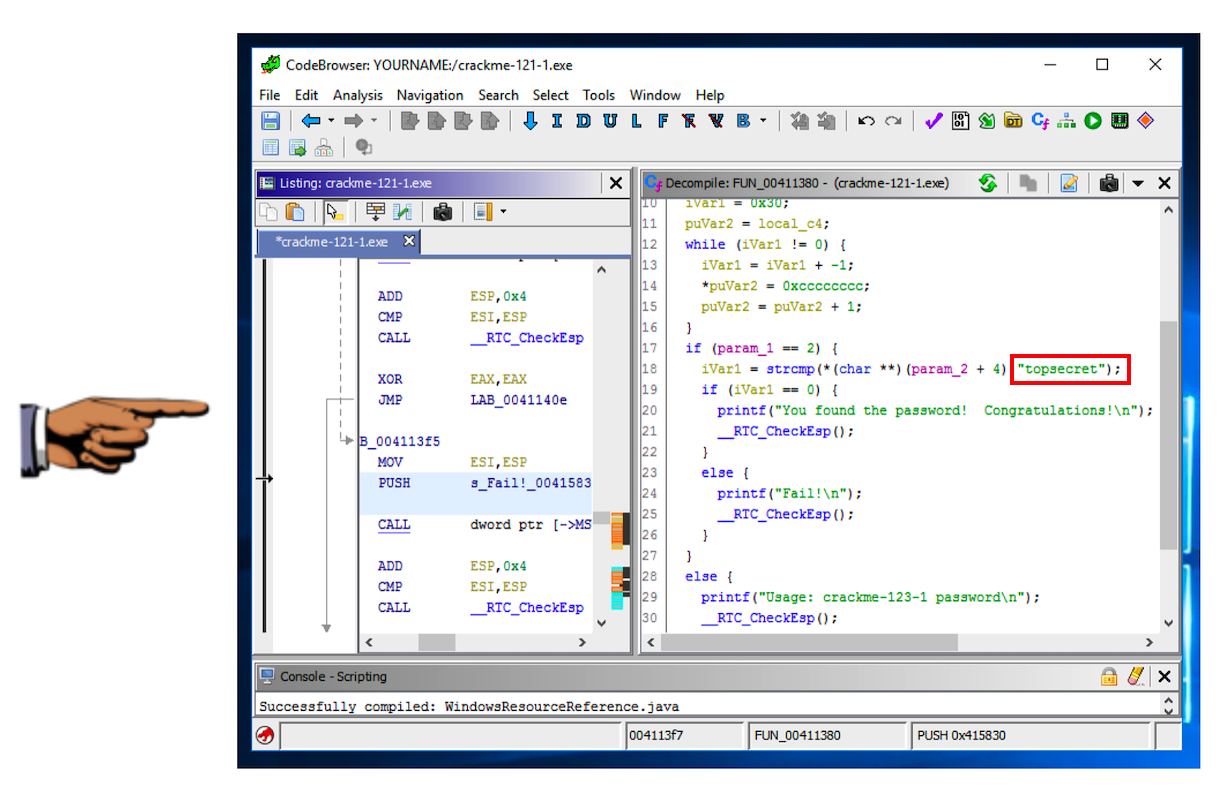
The password is the flag.密码是标志。
The password is the flag.密码是标志。
The flag is that complete command line, like this:标志就是完整的命令行,如下所示:
notepad.exe topsecret