ED 301: Windows Stack Protection I: Assembly Code (15 pts) ED 301:Windows堆栈保护I:汇编代码(15分)
What You Need你需要什么
- A Windows 2016 Server machine, real or virtual. Windows 2016 Server机器,真实或虚拟。 You cannot use Windows Server 2008.您无法使用Windows Server 2008。
Purpose目的
You will write a small C program and compile it with and without stack protection.您将编写一个小型C程序并使用和不使用堆栈保护进行编译。 You'll examine the executable using IDA Pro and see the code that implements the stack cookie.您将使用IDA Pro检查可执行文件,并查看实现堆栈cookie的代码。 Downloading and Installing Visual C++ Build Tools下载和安装Visual C ++生成工具
Note注意 If you already have Visual C++ Build Tools installed, click the Start button, scroll to the V secton, expand " Visual Studion 2017 ", and click " Developer Command Prompt for VS 2017 ", as shown below.如果已经安装了Visual C ++ Build Tools,请单击“ 开始”按钮,滚动到V secton,展开“ Visual Studion 2017 ”,然后单击“ VS 2017的开发人员命令提示符 ”,如下所示。 Then skip to the " Making the pwd Program in C++ " section, below on this page.然后跳到本页下面的“ 在C ++中制作pwd程序 ”部分。 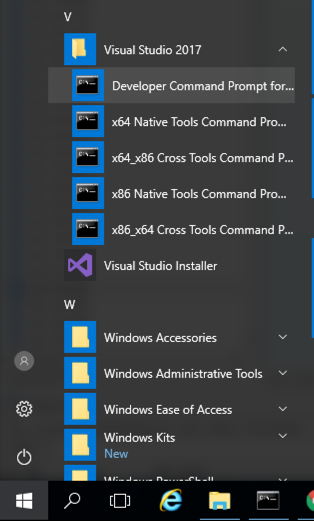
|
Open this page:打开此页面: https://visualstudio.microsoft.com/visual-cpp-build-tools/ https://visualstudio.microsoft.com/visual-cpp-build-tools/
Click the " Download Build Tools " button, as shown below.单击“ 下载构建工具 ”按钮,如下所示。
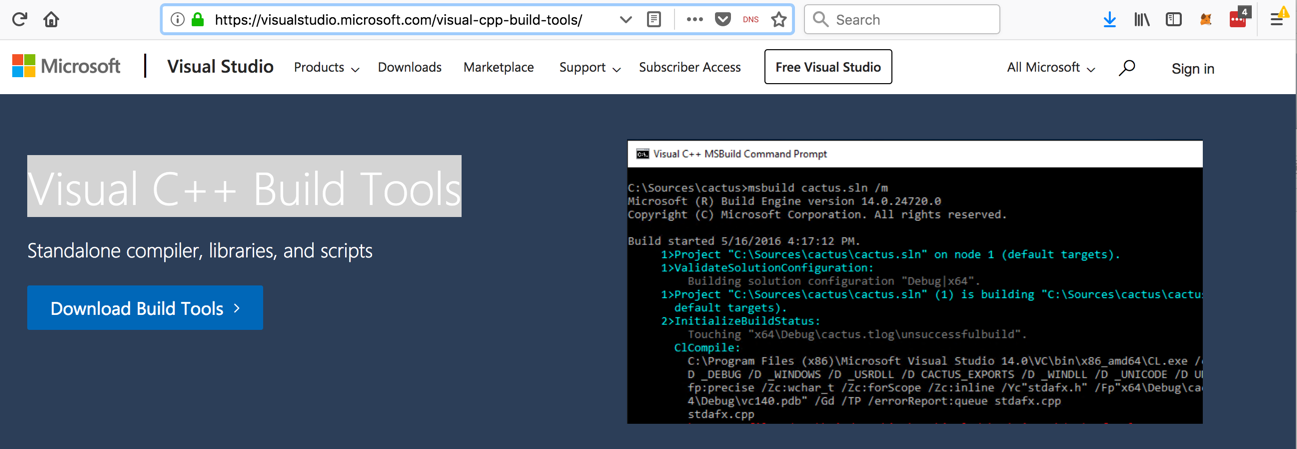
On the next page, in the "Build Tools for Visual Studio 2017" section, click the Download button, as shown below.在下一页的“Visual Studio 2017的构建工具”部分中,单击“ 下载”按钮,如下所示。
Save the vs_buildtools__935747363.1537797301.exe file in your Downloads folder.将vs_buildtools__935747363.1537797301.exe文件保存在Downloads文件夹中。
Double-click the the vs_buildtools__935747363.1537797301.exe file.双击vs_buildtools__935747363.1537797301.exe文件。
A box pops up, as shown below.弹出一个框,如下所示。
Click Continue .单击继续 。
Wait while software downloads and installs, as shown below.等待软件下载和安装,如下所示。
A large window appears, as shown below.出现一个大窗口,如下所示。
At the top left, click " Visual C++ build tools ".在左上角,单击“ Visual C ++构建工具 ”。
Click the Install button.单击“ 安装”按钮。
Wait while software downloads and installs., as shown below.等待软件下载并安装。,如下所示。
When the installation completes, you should see the screen shown below.安装完成后,您应该看到如下所示的屏幕。
Click Launch .单击“ 启动” A Developer Command Prompt window opens, as shown below.将打开“开发人员命令提示符”窗口,如下所示。
Making the pwd Program in C++用C ++编写pwd程序
In the Developer Command Prompt window, execute these commands:在Developer Command Prompt窗口中,执行以下命令: mkdir c:\127 mkdir c:\ 127
cd c:\127 cd c:\ 127
notepad pwd.cpp记事本pwd.cpp
A box pops up, asking "Do you want to create a new file?".弹出一个框,询问“你想创建一个新文件吗?”。 Click Yes .单击是 。 Enter this code, as shown below:输入此代码,如下所示:
#include <iostream> #include <iostream>
using namespace std; using namespace std;
int test_pw() int test_pw()
{ {
char pin[10]; char pin [10];
int x=15, i; int x = 15,i;
cout << "Enter password: "; cout <<“输入密码:”;
cin >> pin; cin >> pin;
for (i=0; i<10; i+=2) x = (x & pin[i]) | for(i = 0; i <10; i + = 2)x =(x&pin [i])| pin[i+1];销第[i + 1];
if (x == 48) return 0; if(x == 48)返回0;
else return 1;否则返回1;
} }
void main() void main()
{ {
if (test_pw()) printf("Fail!\n"); if(test_pw())printf(“失败!\ n”);
else printf("You win!\n"); else printf(“你赢了!\ n”);
} }
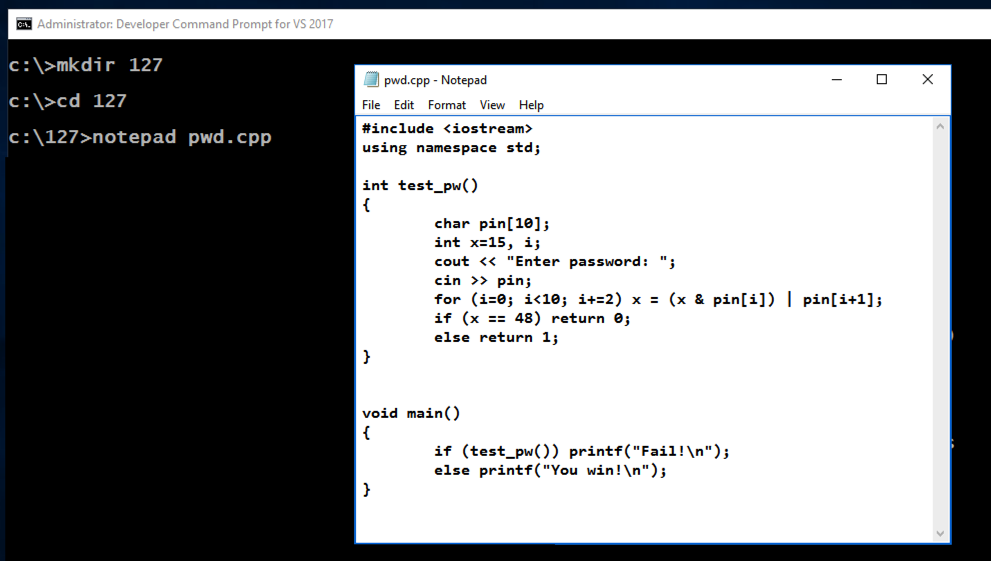
In Notepad, click File , Save .在记事本中,单击“ 文件” ,“ 保存” 。
In the Developer Command Prompt window, execute these commands:在Developer Command Prompt窗口中,执行以下命令:
copy pwd.cpp pwdn.cpp copy pwd.cpp pwdn.cpp
cl /EHsc pwd.cpp cl / EHsc pwd.cpp
cl /EHsc /GS- pwdn.cpp cl / EHsc / GS- pwdn.cpp
dir *.exe dir * .exe
Two versions of the program are produced.制作了两个版本的程序。 The "pwd.exe" program has stack protections, but "pwdc.exe" does not, so it's slightly smaller, as shown below. “pwd.exe”程序具有堆栈保护,但“pwdc.exe”没有,因此它稍微小一些,如下所示。 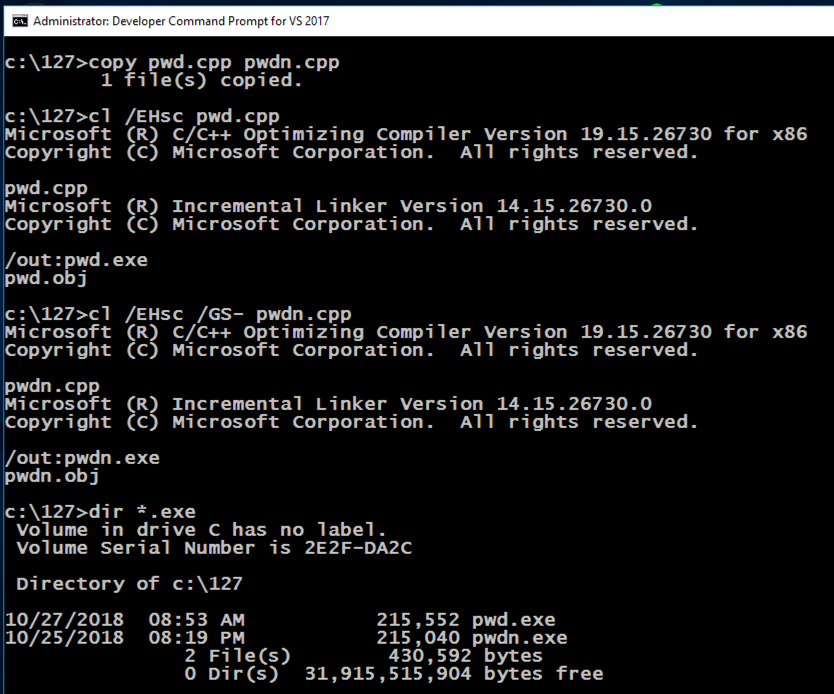
Installing IDA Freeware安装IDA免费软件
In a Web browser, go to:在Web浏览器中,转到: https://www.hex-rays.com/products/ida/support/download_freeware.shtml https://www.hex-rays.com/products/ida/support/download_freeware.shtml
Download and install the Windows version, as shown below.下载并安装Windows版本,如下所示。
Viewing pwd.exe in IDA在IDA中查看pwd.exe
Double-click the " IDA Freeware " shortcut on your desktop.双击桌面上的“ IDA免费软件 ”快捷方式。 In the "IDA: Quick start" box, click New , as shown below.在“IDA:快速启动”框中,单击“ 新建” ,如下所示。
Navigate to the C:\127\pwd.exe file and double-click it.导航到C:\ 127 \ pwd.exe文件并双击它。
In the "Load a new file" box, click OK .在“加载新文件”框中,单击“ 确定” 。
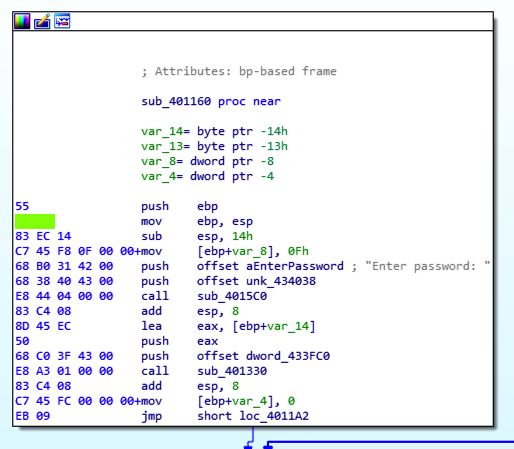
IDA opens, showing some assembly code, as shown below. IDA打开,显示一些汇编代码,如下所示。
From the IDA menu, click View , " Open subviews ", Strings .在IDA菜单中,单击“ 查看” ,“ 打开子视图 ”,“ 字符串” 。
Double-click " Enter password ", as shown below.双击“ 输入密码 ”,如下所示。
The .rdata section appears, showing stored strings.出现.rdata部分,显示存储的字符串。 On the line containing "Enter password", find "DATA XREF".在包含“输入密码”的行上,找到“DATA XREF”。 Point to the address after the "DATA XREF" marker, as highlighted in yellow in the image below, and double-click it.指向“DATA XREF”标记后的地址,如下图中黄色突出显示,然后双击它。
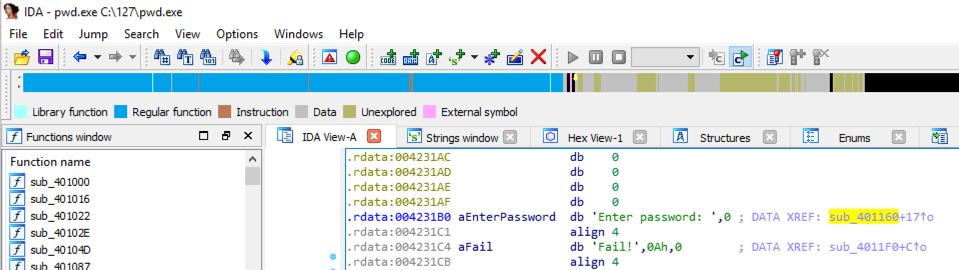
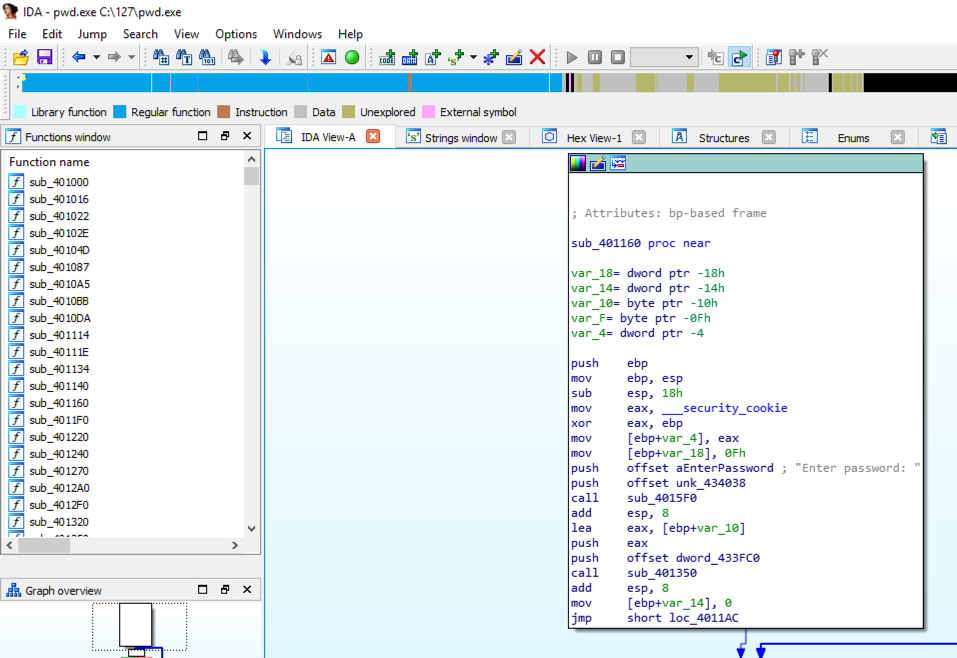
The function prologue appears, with a line containing "security_cookie", as shown below.出现函数序言,其中包含一行“security_cookie”,如下所示。
Viewing pwdn.exe in IDA在IDA中查看pwdn.exe
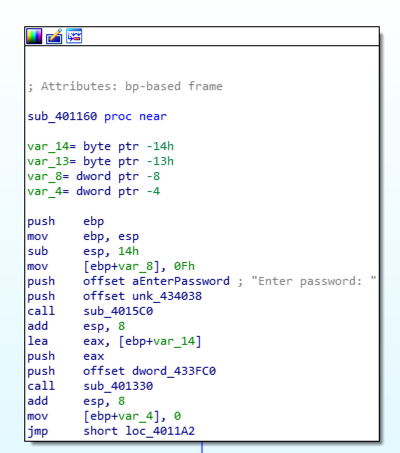
Repeat the process to see the prologue for pwdn.exe .重复此过程以查看pwdn.exe的序言。 The "security_cookie" line is gone, as shown below. “security_cookie”行已经消失,如下所示。
ED 301.1: Viewing Opcode Bytes (15 pts) ED 301.1:查看操作码字节(15分)
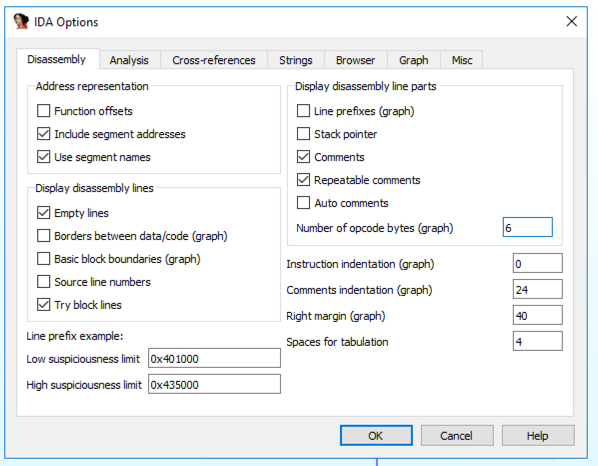
From the IDA memu, click Options , General .从IDA备忘录中,单击选项 , 常规 。 Enter a "Number of opcode bytes" of 6 as shown below.输入6的“操作码字节数”,如下所示。 Then click OK .然后单击确定 。
Find the hexadecimal values covered by a green box in the image below.找到下图中绿框所覆盖的十六进制值。 That's the flag.那是旗帜。
Posted: 10-27-18发表时间:10-27-18