I used to use the "Katoolin" tool but it has been deprecated, and the recommended replacement "Tool-X" fails to install the Metasploit dependencies, so it's easier to just install these tools directly.
https://console.cloud.google.com
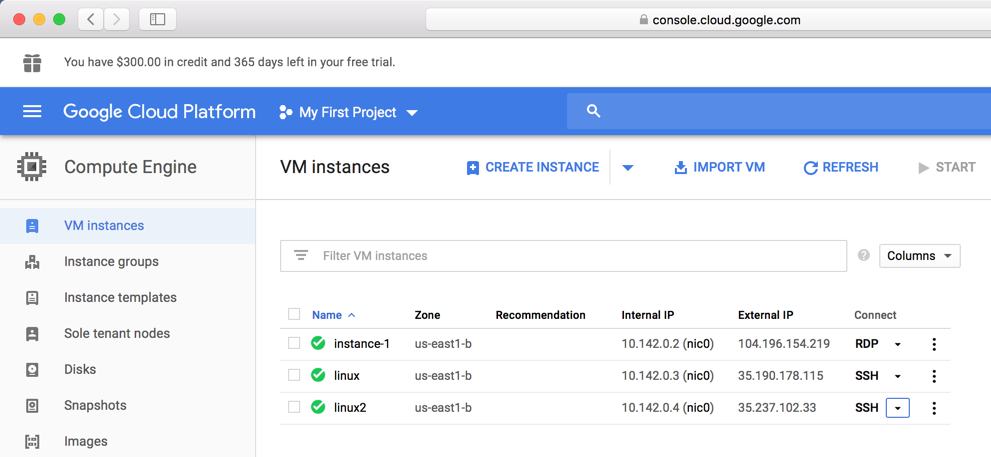
Log in to Google, and you should see your Google Cloud Platform Console.
On the left side, click "Compute Engine". as shown below.

curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
chmod 755 msfinstall
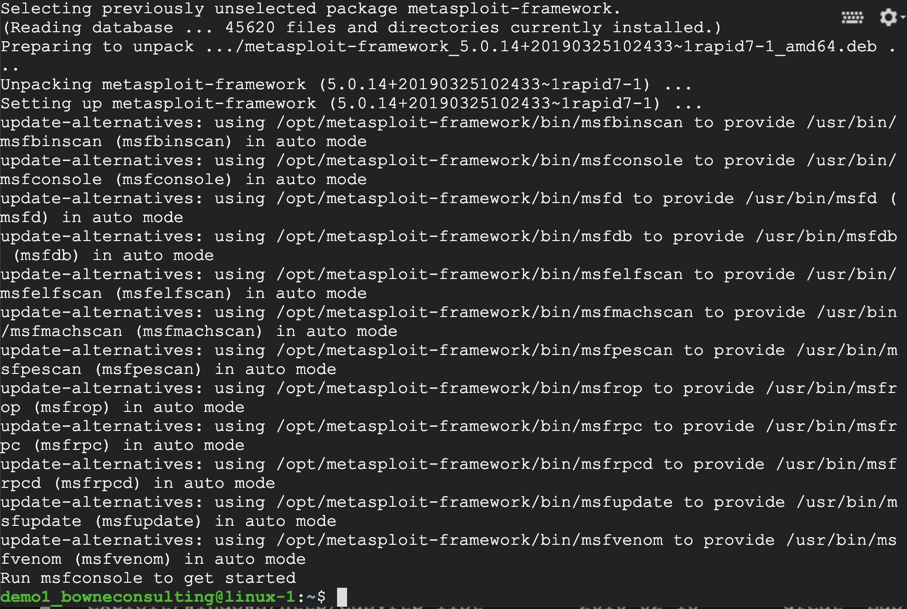
sudo ./msfinstall
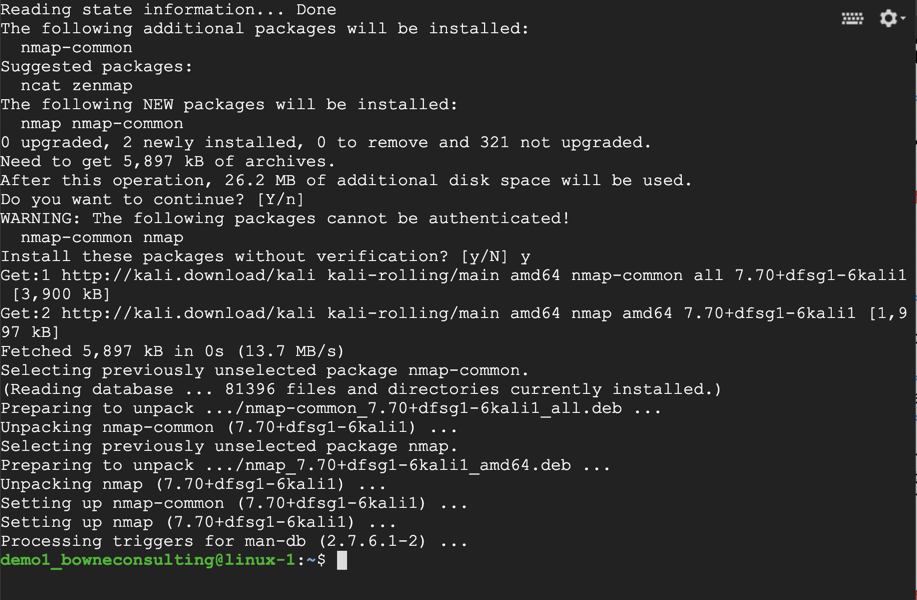
sudo apt install nmap
Nmap installs, as shown below.
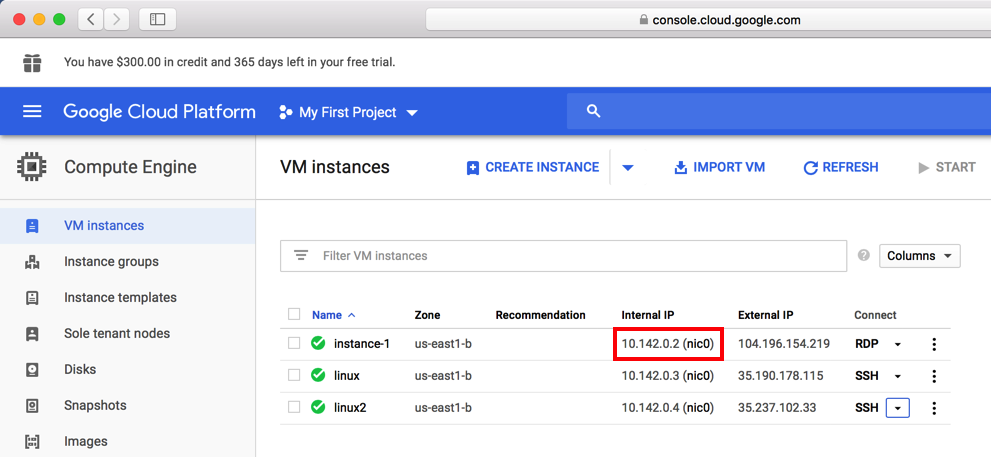
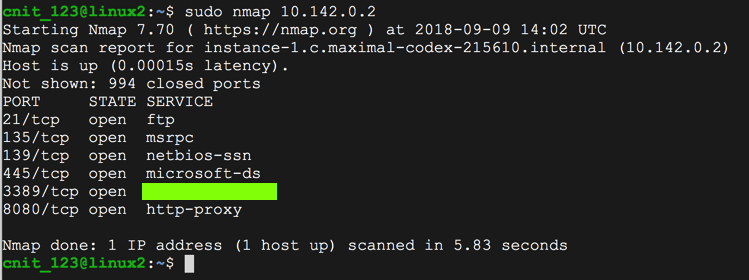
sudo nmap 10.142.0.2
Find the service name, which is covered by a green box in the image below. Enter it into the form below.
Moved to local server 3-21-19
Updated to remove Katoolin 3-25-19
Form removed 7-9-19