Project 6: Wireshark (30 pts)
What You Need for This Project
- Any computer. Wireshark runs on every OS.
Installing Wireshark
If your computer doesn't already have it,
go to
https://www.wireshark.org/
Download and install the latest version.
I wrote these instructions using Wireshark 2.6.1
for the Mac on 6-28-18.
Examining Layers 1-4
Download this file and double-click it to open it in Wireshark:
FTPlogin.pcapng
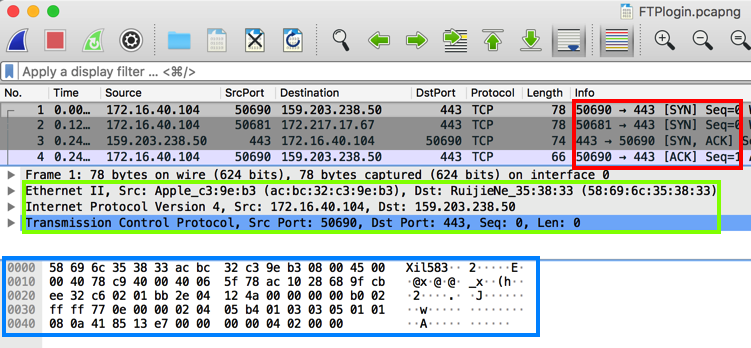
Find these features, as shown below:
- Packet List in the top pane, showing one line per packet.
Notice the TCP handshake performed by packets 1, 3, and 4, outlined
in red in the image below.
- Packet Details in the middle pane, showing the first four TCP layers. Notice MAC addresses at layer 2, IP addresses at layer 3, and TCP port numbers at layer 4, outlined
in green in the image below.
- Packet Bytes in the bottom pane, showing raw data in hexadecimal and ASCII form, outlined
in red in the blue below.
6.1 Finding an FTP Password
FTP is a very unsafe protocol, because it sends
passwords over the network without encryption.
To demonstrate that, we'll steal a password.
In Wireshark, at the top, in the "Apply a display filter" box,
type ftp and press the Enter key.
Wireshark filters the packets, showing only the packets
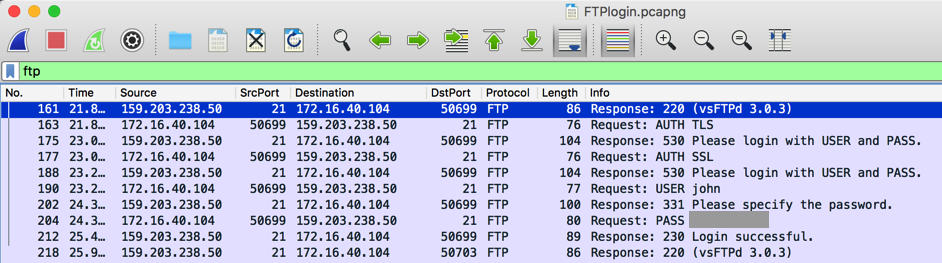
using File Transfer Protocol. On the right side,
you can see the login process for a user named
"john". Find John's password, which is covered by a gray
box in the image below.
6.1: Recording Your Success (5 pts)
Use the form
below to record your success.
6.2 Finding an HTTP Password
HTTP also sends
passwords over the network without encryption.
To demonstrate that, we'll steal a password.
Download this file and double-click it to open it in Wireshark:
httplogin.pcapng
In Wireshark, at the top, in the "Apply a display filter" box,
type http and press the Enter key.
Wireshark filters the packets, showing only the packets
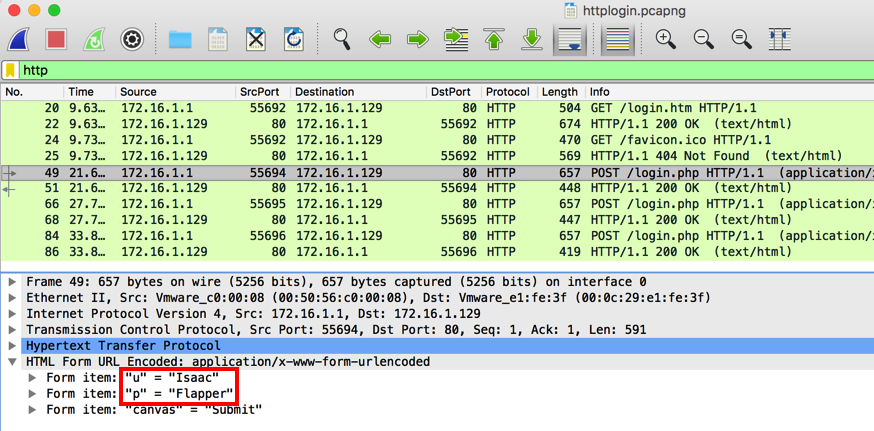
using HTTP. In the Packet List, in the "Info" column,
find the first POST request, as shown below,
and click it.
In the Packet Details, expand the "Hypertext
Transfer Protocol" container. The username of
"Isaac" and password of "Flapper" are visibie,
as outlined in red in the image below.
Following a TCP Stream
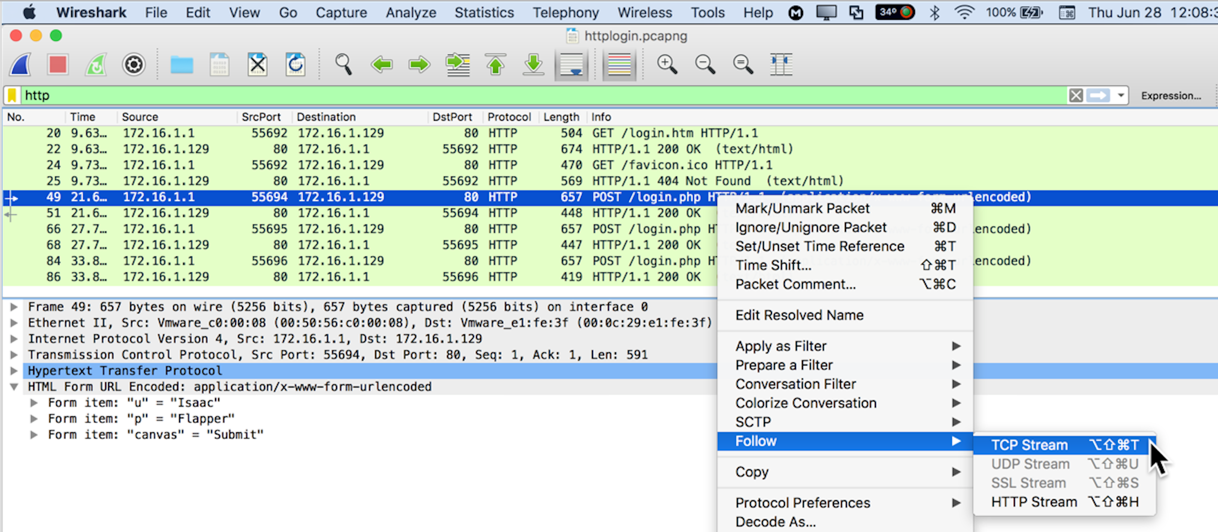
In the Packet List, in the "Info" column,
right-click the first POST request,
click Follow,
and click "TCP Stream",
as shown below,
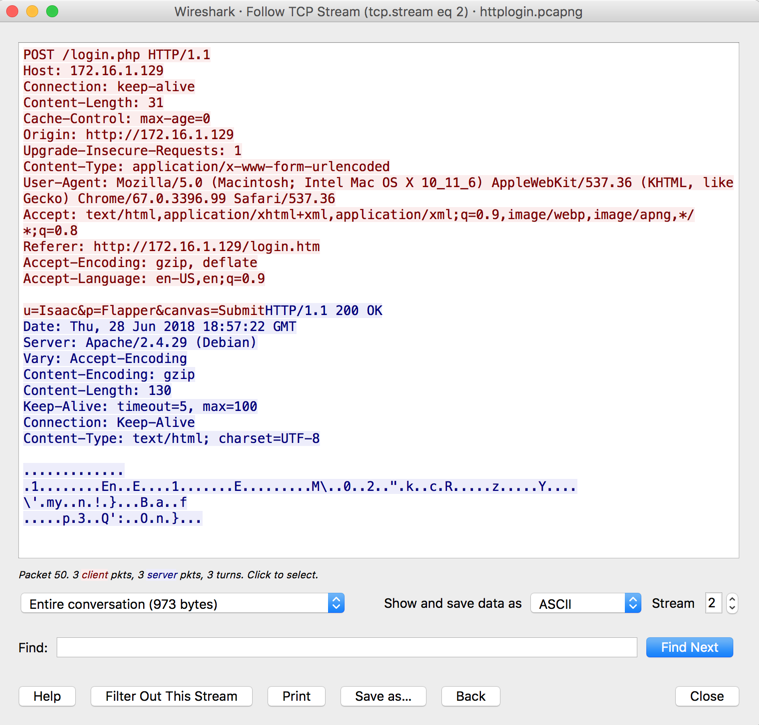
The conversation is shown, with the client's
transmission in red, and the server's response
in blue, as shown below.
The TCP Stream is often very helpful, but not in
this case, because the reply is zipped.
Restoring the Packet Filter to "http"
Close the "Follow TCP Stream" box.
In Wireshark, at the top, in the "Apply a display filter" box,
on the right side, click the X to clear the filter.
In the "Apply a display filter" box,
type http and press the Enter key.
All the "http" packets appear, as shown below.
Viewing the HTTP Reply
In the Packet List, in the "Info" column,
click the packet following the first POST request,
which is labelled "HTTP/1.1 200 OK",
as shown below.
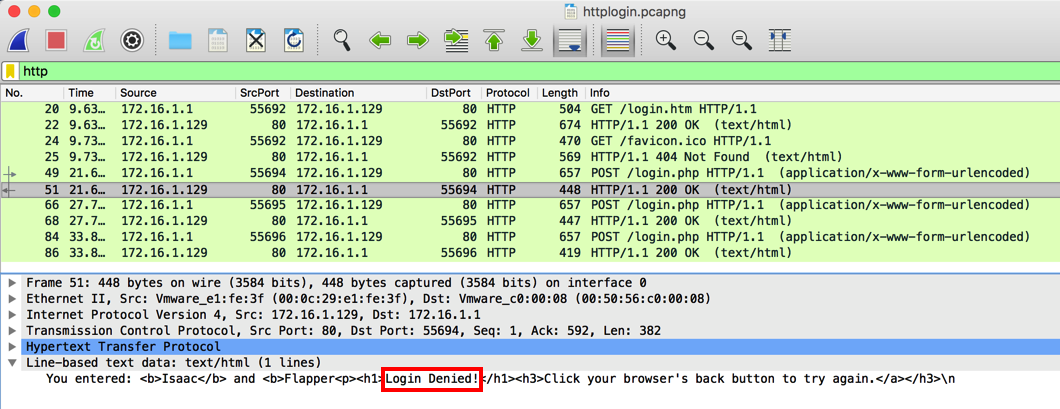
In the Packet Details, expand the "Line-based
test data" container. The
server's reply is now readable, saying
"Login Denied!",
as outlined in red in the image below.
Finding Isaac's Password
Isaac made several attempts to log in
before finally entering the correct password.
Find the password that worked and enter it
into the form below.
6.2: Recording Your Success (10 pts)
Use the form
below to record your success.
6.3 HTTP Basic Authentication
HTTP Basic authentication
obfuscates passwords with Base64 encoding before
transmitting them, which is not
much better than sending them in
cleartext, because Wireshark
automatically decodes them.
Download this file and double-click it to open it in Wireshark:
BasicLogin.pcapng
A user named WALDO logged in. Find Waldo's password and enter it
into the form below.
6.3: Recording Your Success (15 pts)
Use the form
below to record your success.
Posted: 3-24-19






