
Log in to with:
"Command Prompt" is found, as shown below.

Click "Command Prompt".
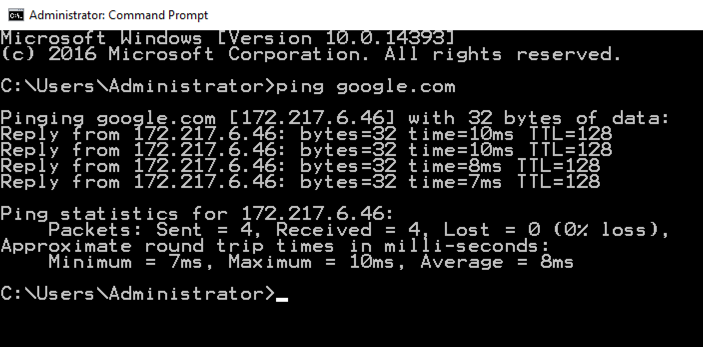
In the Command Prompt window, execute this command, as shown below.
ping google.com
Type FIREWALL.
In the Search results, click "Windows Firewall", the second result in the image below.
In the Windows Firewall box, on the left side, click "Turn Windows Firewall on or off".
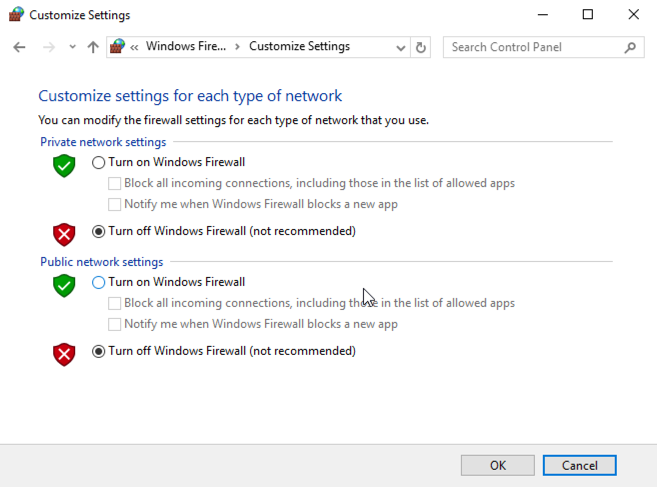
Check both of the boxes labelled "Turn off Windows Firewall (not recommended)", as shown below.
Click OK.
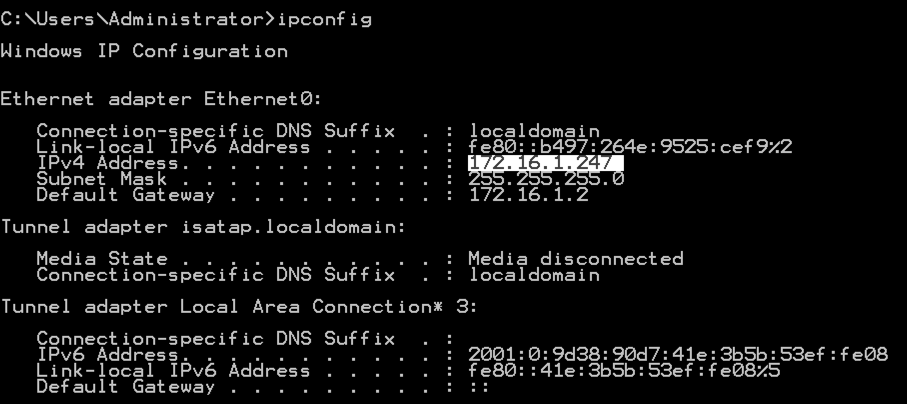
ipconfig
On your Linux machine, in the Terminal window, execute this command, as shown below, replacing the IP address with the IP address of your Windows Server 2016 machine.
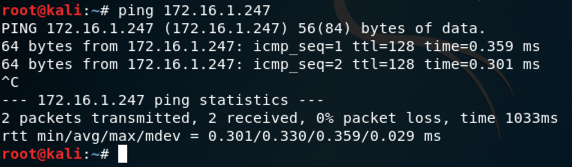
ping 172.16.1.247
You should see replies, as shown below. If you do not, perform the "Troubleshooting" steps in the box above. You should also make sure the Windows firewall is off, as explained in an earlier project.
sudo apt install nmap -y
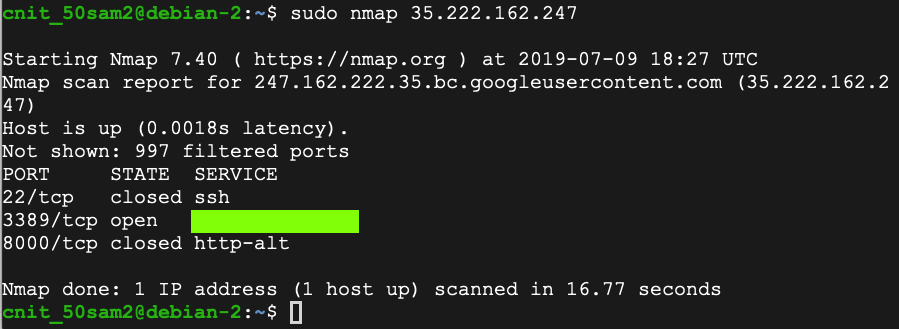
sudo nmap 172.16.1.243
Type FIREWALL.
In the Search results, click "Windows Firewall", the second result in the image below.

In the Windows Firewall box, on the left side, click "Turn Windows Firewall on or off".
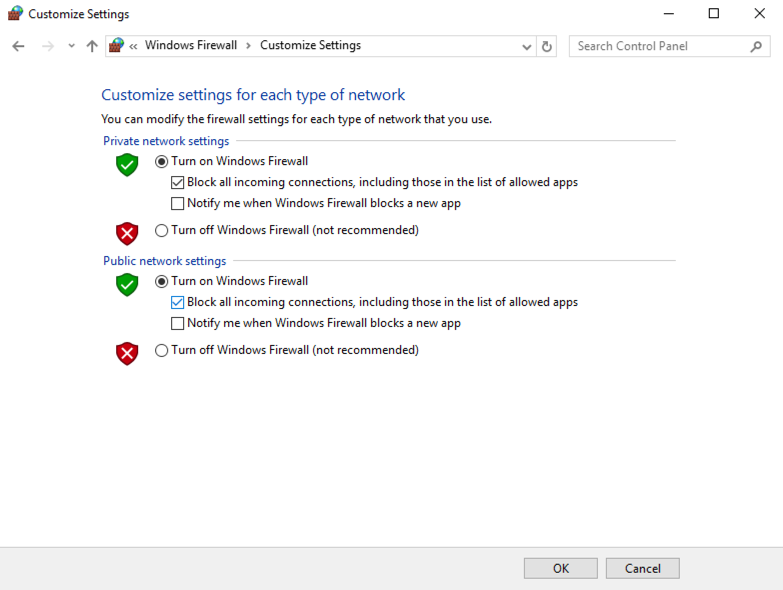
Check both of the buttons labelled "Turn on Windows Firewall", and both the boxes labelled "Block all incoming connections...", as shown below.
Click OK.
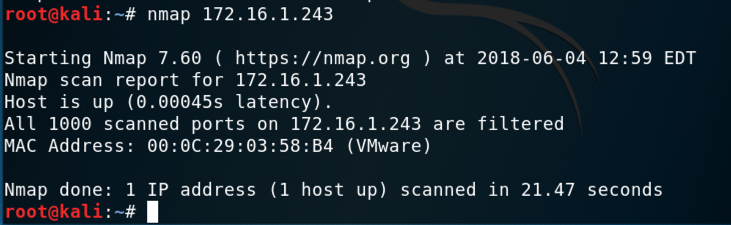
nmap 172.16.1.243
https://svn.nmap.org/nmap/docs/nmap.usage.txt
These are the most important ones:
Scan your Windows server with operating system detection, and then scan UDP port 53.
Your results should be similar to those shown below.
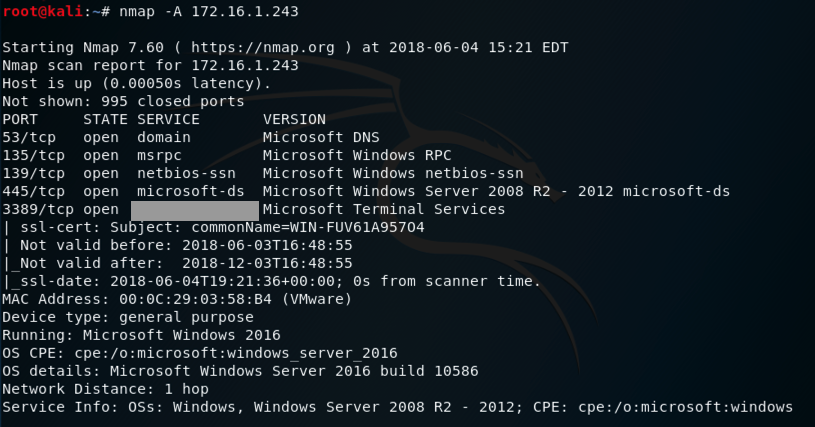
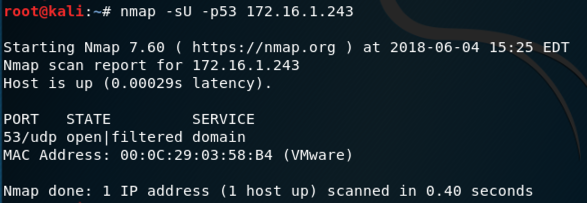
That port number is the flag.
That port number is the flag.
Moved to local server 3-21-19
Forms removed 7-9-19