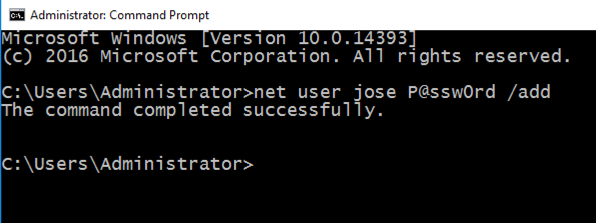
Type in CMD and press Shift+Ctrl+Enter.
If a "User Account Control" box pops up, click Yes.
In the Administrator command prompt window, execute this command, which creates a user named "jose" with a password of "P@ssw0rd".
net user jose P@ssw0rd /add

Download the correct version for your operating system, which is probably the 64-bit version, as shown below.
Install it with the default options.
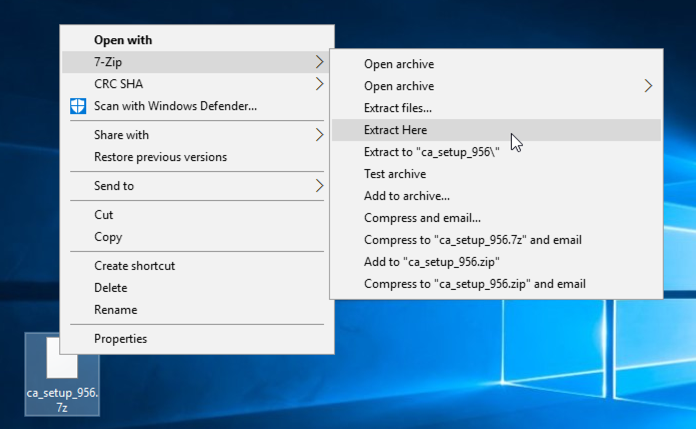
Right-click the downloaded file, point to 7-Zip, and click "Extract Here", as shown below.
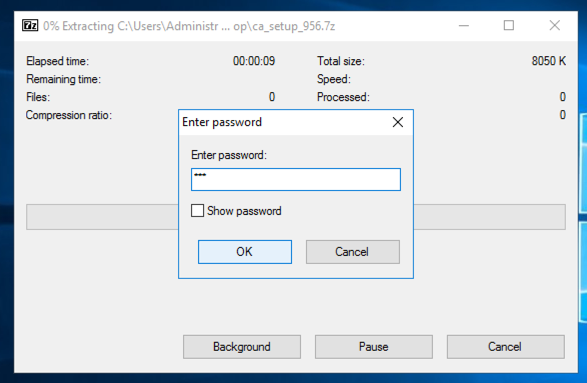
Enter a password of sam as shown below. Click OK.
Double-click the ca_setup file. Install the software with the default options, as shown below.
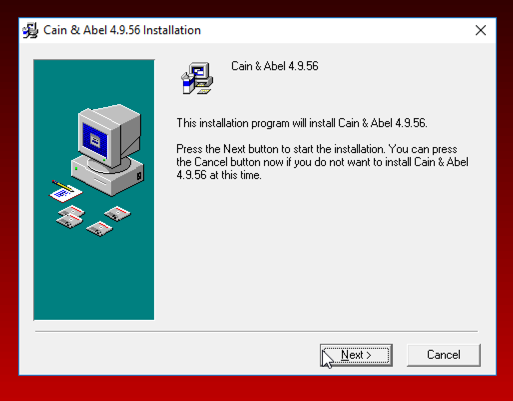
When you see the message below, asking whether to install WinPcap, click the "Don't install" button.
Troubleshooting
If you get a warning box saying "Found some malware", as shown below, you need to tell Windows Defender not to remove Cain.
At the lower left of the desktop, click the magnifying-glass "Search" icon and type DEFENDER. Open Windows Defender.
In Windows Defender, click Settings and turn off "Real-time protection" as shown below.
Close Windows Defender and run the ca_setup file again.
If this is your personal machine, remember to turn "Real-time protection" back on when you complete the project.
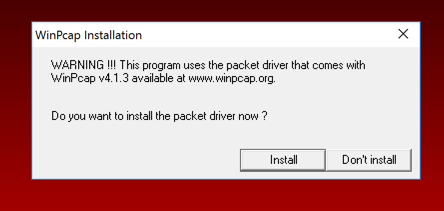
https://www.winpcap.org/install/
Click "Installer for Windows", as shown below. Download and install the software with the default options.
If a "User Account Control" box pops up, click Yes.
In Cain, on the upper set of tabs, click Cracker.
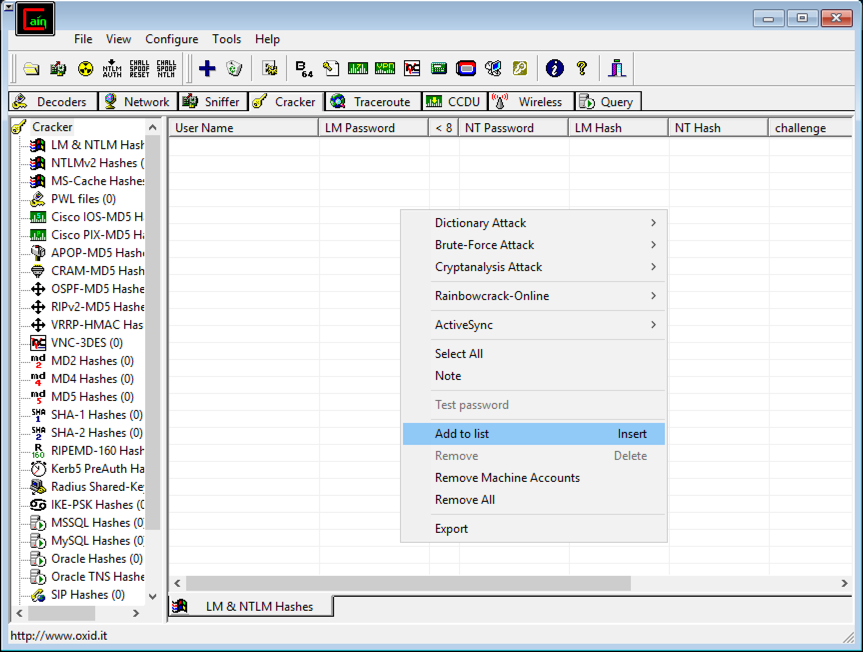
In Cain, move the mouse to the center of the window, over the empty white space.
Right-click and click "Add to list...", as shown below.
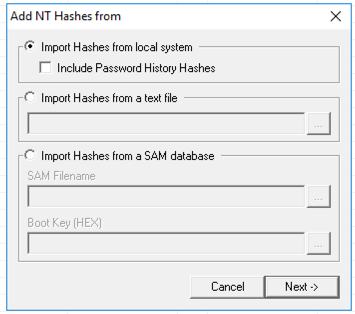
In the "Add NT Hashes from" box, accept the default selection of "Import Hashes from local system", as shown below, and click Next.
The password hashes appear, as shown below.
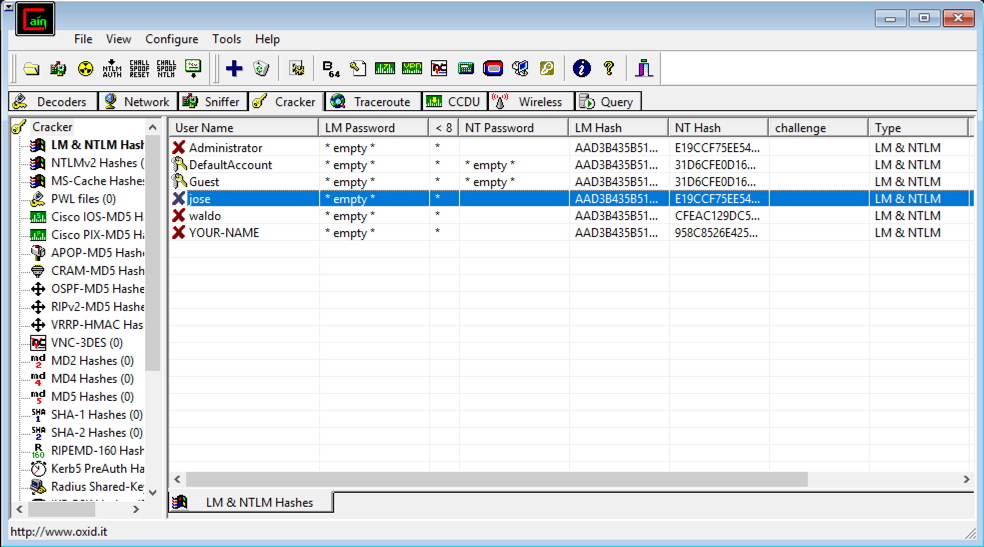
LM hashes date from the 1980's, and are so weak Microsoft no longer uses them. The LM hash values Cain shows are just dummy filler values that no longer include any information about real passwords.
NT hashes are Microsoft's "more secure" hash, used by Windows NT in 1993 and never updated in any way. As you will see, these hashes are also very weak and easily cracked, compared with Linux password hashes.
Cracking four Linux hashes took about 20 seconds using a dictionary of 500 words when I did it, but as you will see, you can crack four Windows passwords using a dictionary of 500,000 words in about a second. Windows password hashes are more than 10,000 times weaker than Linux hashes.
Notice that your NT password hash for "Jose" starts with E19CC, just like mine, shown in the image above. This is because Microsoft doesn't add a random "salt" to passwords before hashing them--every user on every Windows machine on Earth has the same salt if they are using a password of P@ssw0rd.
That means you can often crack Windows password hashes by just Googling them, as shown below, because many lists of common passwords and hashes have been uploaded to the Internet over the last 20 years.
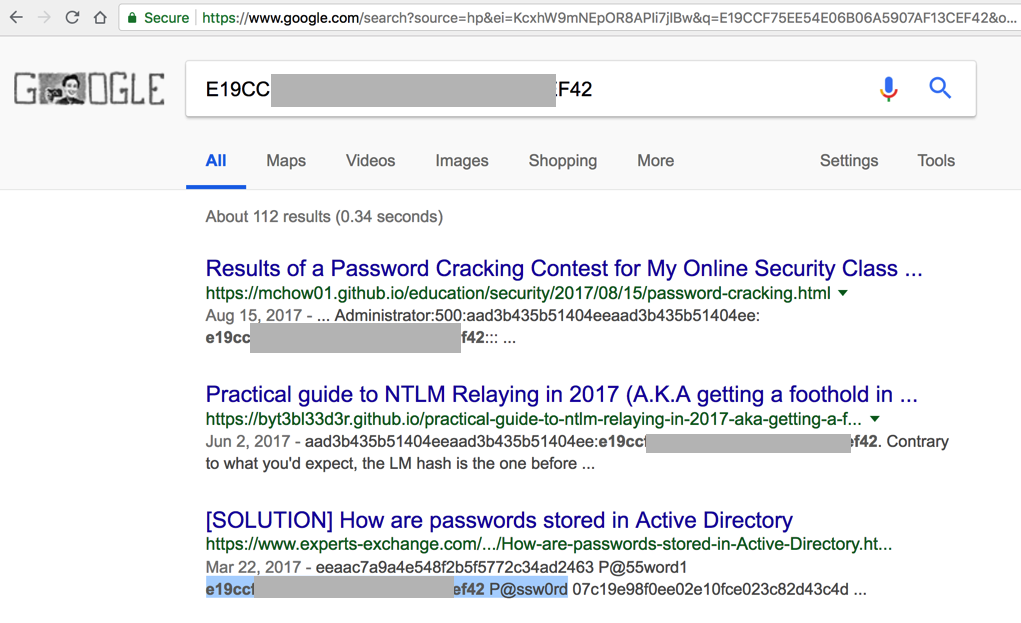
However, in this project, we'll use hashcat, which is a very powerful way to crack passwords.
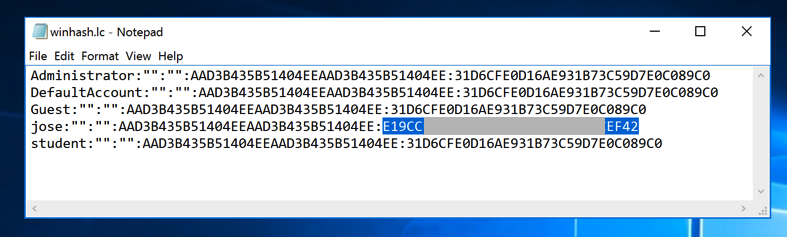
Open the win1.lc file in Notepad.
Carefully highlight the NT hash for Jose, as shown below, right-click it, and click Copy.
cd
nano win1.hash
The hash appears, as shown below:
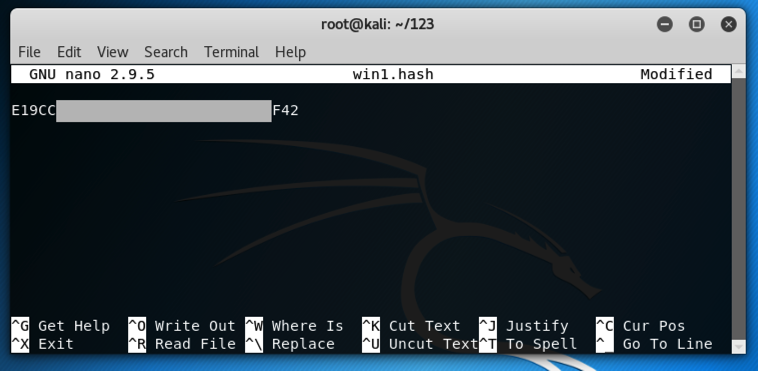
Press Ctrl+X, Y, Enter to save the file.
In a Terminal window, execute these commands to extract them:
gunzip /usr/share/wordlists/rockyou.txt.gz
head /usr/share/wordlists/rockyou.txt
In a Terminal window, execute these commands:
cd
mkdir hash
cd hash
wget https://hashcat.net/files/hashcat-2.00.7z
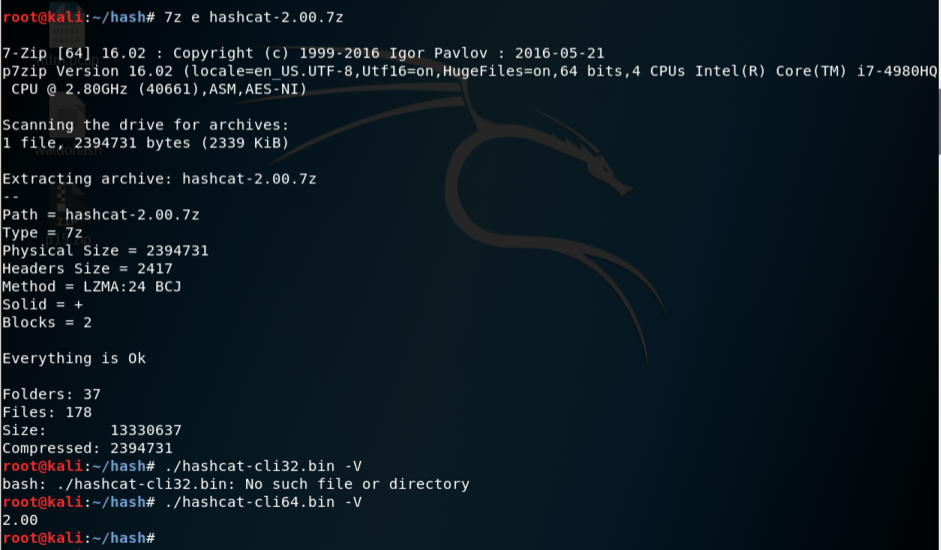
7z e hashcat-2.00.7z
./hashcat-cli32.bin -V
./hashcat-cli64.bin -V
Make a note of which version works on your system. I used a 64-bit Kali system, so the working version was hashcat-cli64.bin, as shown below.
Troubleshooting
If that download link doesn't work, right-click this link and save the file:
cd
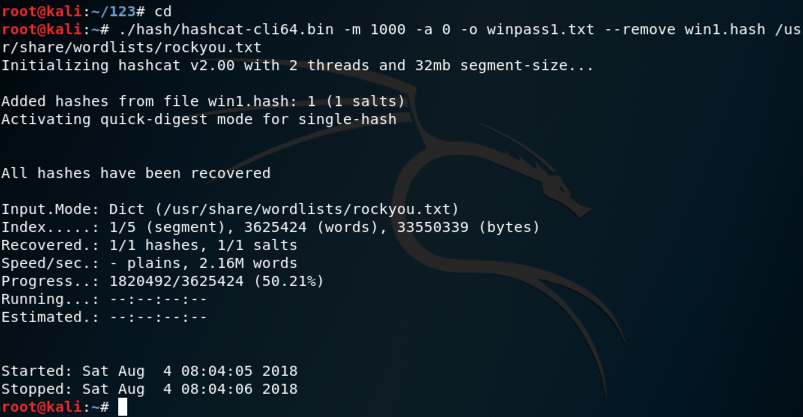
./hash/hashcat-cli64.bin -m 1000 -a 0 -o winpass1.txt --remove win1.hash /usr/share/wordlists/rockyou.txt
You see a message saying "All hashes have been recovered", as shown below.
Explanation: This uses hashcat with these options:
In a Terminal window, execute this command:
cat winpass1.txt
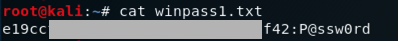
curl https://samsclass.info/123/proj10/win2.hash > win2.hash
cat win2.hash

./hash/hashcat-cli64.bin -m 1000 -a 0 -o winpass2.txt --remove win2.hash /usr/share/wordlists/rockyou.txt
cat winpass2.txt
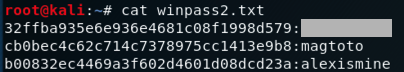
Enter the password for the hash beginning with "32ff" into the form below.
http://hashcat.net/files/hashcat_user_manual.pdf
http://contest-2010.korelogic.com/wordlists.html
http://www.scovetta.com/article-2.html