

Archived APK
This project requires the 2016 version of the app, which was still the version in Google Play in Feb, 2021.If that version is no longer available, use this archived copy of the app:
Fill in the form, as shown below, but don't click the "Sign Up" button yet.

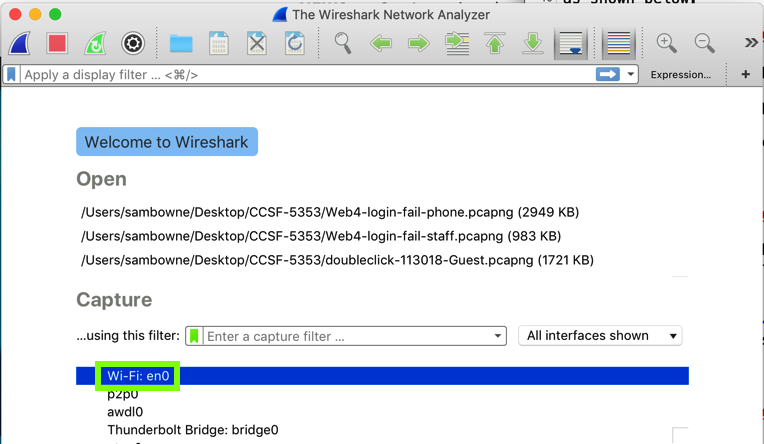
In the main Wireshark window, double-click the network interface that is being used to reach the Internet. On my system, it is "Wi-Fi: en0", outlined in green in the image below.
Wirehark starts displaying packets. At the top, in the Filter bar, enter this display filter:
http
On your Android device, in EquityPandit, click the "Sign Up" button.
In Wireshark, two POST requests appear, as shown below.
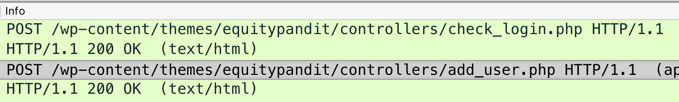
Right-click the second POST request, the one calling "add_user.php", and click Follow, "TCP Stream".
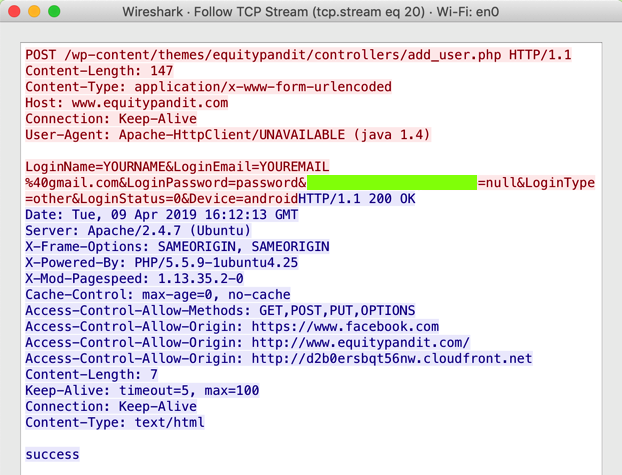
The request appears, as shown below, containing your username and password in plaintext.
M 204.1: Recording Your Success (15 pts)
The flag value is the portion of the request covered by a green rectangle in the image above.
M 204.2: Find the Server (10 pts extra)
Uninstall the EquityPandit app and install this app instead:Execute a login request. The flag is the domain name of the server it sends a POST request to.
Incompatible Version
If you get a message saying saying the app is incompatible with this version of BlueStacks, upgrade to BlueStacks 5 Beta.This worked on 2-28-2021.
M 204.3: Flag1 (5 pts extra)
Use the same app: A30.2.apk.Launch the app on your Android device.
Use the app, tap the available items, and explore the app to find an activity showing a flag labeled "Flag1".
M 204.4: Find the Server (5 pts extra)
Install this appExecute a login request. The flag is the domain name of the server it attempts to connects to.
M 204.5: Find the Stored Password (10 pts extra)
Use the original EquityPandit app. Create an account and log in.From Kali, connect to your Android device with adb connect.
If you are not root, first root your device. To root BlueStacks, see a later project.
Open a shell on the Android device with adb shell
Now you can use normal Bash commands, including these:
Find the locally stored copy of your password. The name of the file containing it is the flag.
M 204.6: Find the Logged Password (10 pts extra)
Use the original EquityPandit app.In Settings, click Apps, EquityPandit, "Clear data", OK.
Then click "Force stop", OK.
Create an account, if necessary, and log in.
From Kali, find your Android device with the netdiscover command.
Connect to it with adb connect.
View the log with adb logcat
Find your password in the log, as shown below. The flag is the word covered by a green box in the image below.
M 204.7: Find My Password (10 pts extra)
I made an account on the EquityPandit system with this email address: topsecret@mailinator.comFind my password. My password is the flag.
Note: don't perform any scans or attacks against any server--we don't have authorization for that.
It is possible to get my password by using the app itself, without performing any attack at all.
If you have any questions, talk to your supervisor or your instructor before taking any questionable actions.