Warning
Havij is the tool LulzSec and Anonymous use to earn long prison terms. It's so easy it will make you sick. ONLY SCAN SYSTEMS YOU HAVE PERMISSION TO ATTACK.Using the "Find Users" Page
In a Web browser, go tohttp://ad.samsclass.info/sqlol/search.htm
A "Find Users" page opens, as shown below:
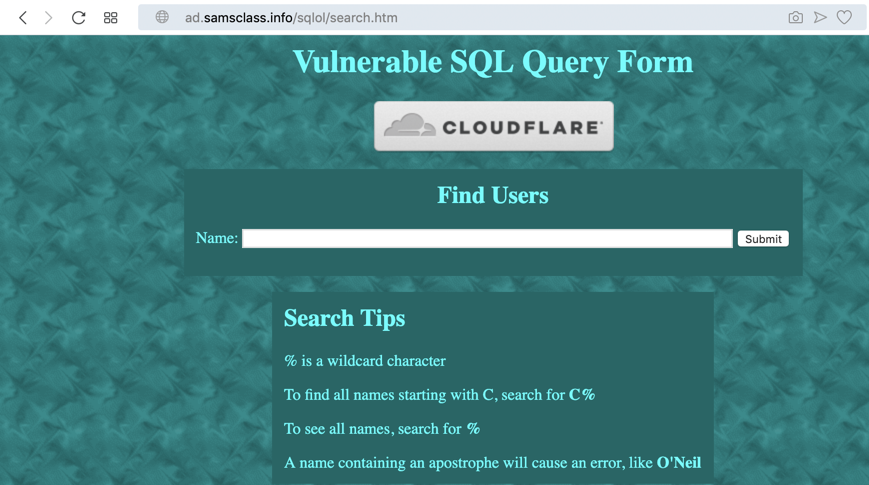
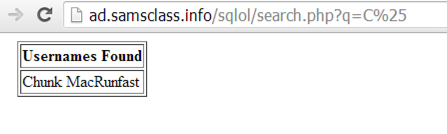
In the Name field, type
C%
You should see the username "Chunk MacRunfast", as shown below:
In the browser, click the Back button to return to the "Find Users" page.
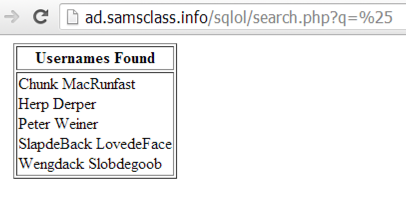
In the Name field, type
%
You should see all five usernames, as shown below:
Breaking the "Find Users" Page
Apparently the designers of this site don't regard usernames as confidential. But the database also contains social security numbers, and those really are confidential.The whole point of SQL injection is that a simple form like this can be tricked into revealing more data than the designer intended to reveal.
In the browser, click the Back button to return to the "Find Users" page.
In the Name field, type this name, as shown below.
O'Neil
You should see an error message, as shown below:
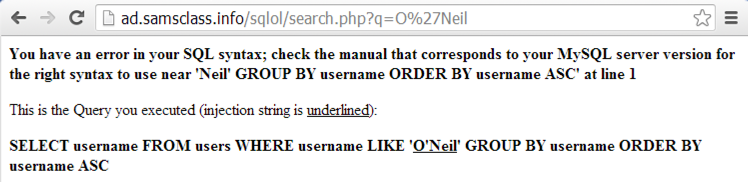
This is the kiss of death--an error like this means that you have lost control of the database, and an attacker can often extract all the data.
We'll steal the data with Havij, which is absurdly easy to use. In the browser, click the Back button to return to the "Find Users" page.
In the Name field, type
x
You should see the results page, as shown below:
No users were found, but that's not a problem. What we really want is the URL of this page, as shown in the address bar:
http://ad.samsclass.info/sqlol/search.php?q=x
Installing 7-Zip
On your Windows machine, in a Web browser, go to:Install Havij with the default options. If you are using a 64-bit Windows system, use the 64-bit version.
Installing Havij
Havij is a free and powerful SQL Injection attack tool.On your Windows machine, in Internet Explorer, Edge, or Firefox, go to:
https://samsclass.info/123/proj14/Havij1.15Free.rar
Don't try to use Chrome--Chrome will block this file.
After the file downloads, view it in File Explorer.
Right-click the file and click 7-Zip, "Extract here".
Double-click the Havij installer and install Havij with the default options.
If it doesn't launch automatically, click Start, type Havij into the Search box, and run Havij. It does not require Administrator privileges.
Using Havij to Steal Data
In the Havij window, paste this URL into the Target field:http://ad.samsclass.info/sqlol/search.php?q=x
In the Havij window, click the Analyze button.
The Log at the bottom of the Havij window should show "Current DB: sqlol", as shown below:
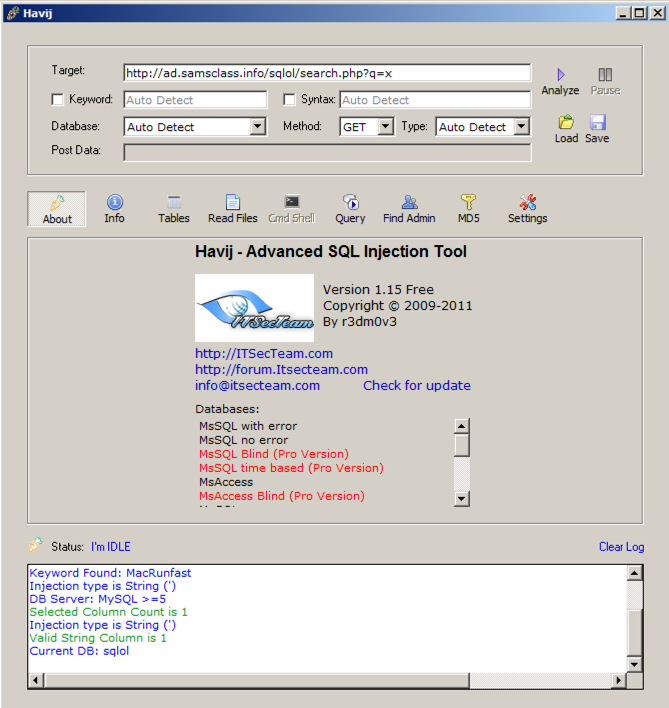
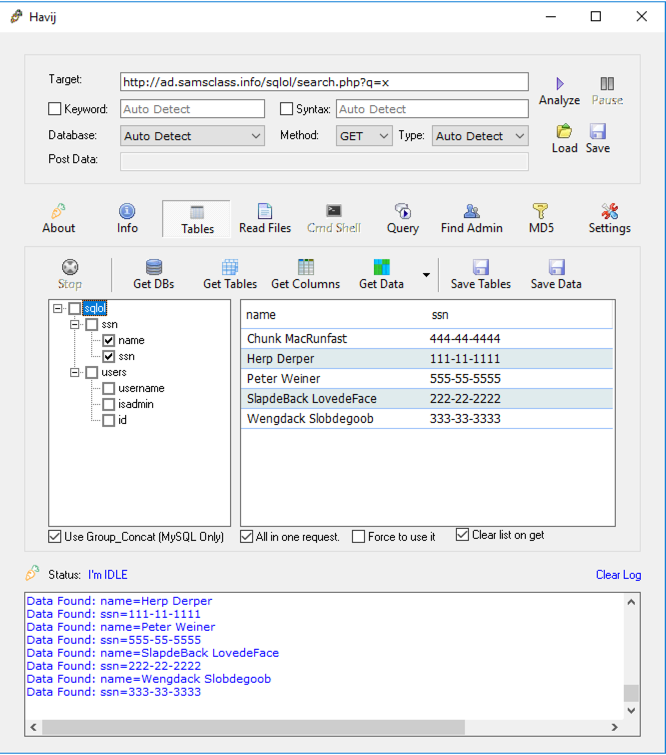
In the upper center of the Havij window, click the Tables button.
In the lower bar that appears, click the "Get Tables" button.
The tables "ssn" and "users" appear, as shown below:
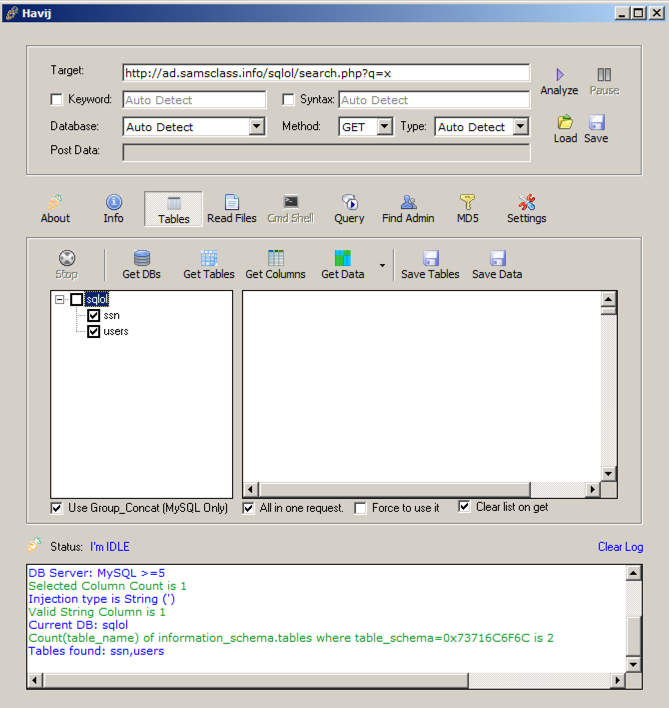
In the left-center pane of the Havij window, check the ssn and users boxes.
In the center of the Havij window, click the "Get Columns" button.
The column names appear, as shown below:
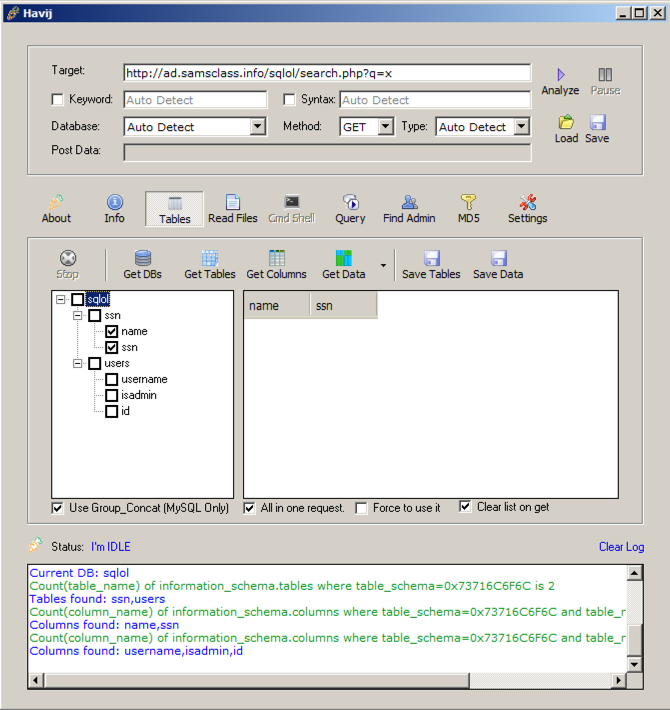
In the left-center pane of the Havij window, in the "ssn" table section, check the name and ssn boxes.
In the center of the Havij window, click the "Get Data" button.
The names and SSNs appear, as shown below:
Fixing the Vulnerability with Input Validation
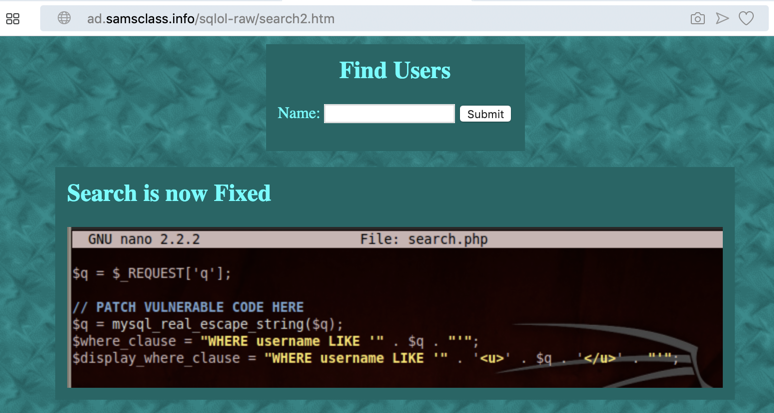
In your browser, go tohttp://ad.samsclass.info/sqlol-raw/search2.htm
A "Find Users" page opens, as shown below:
In the Name field, type
O'Neil
Now, instead of an error, you see a chart showing that no results were found, as shown below:
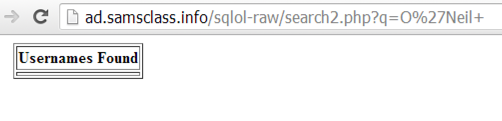
You can see how the fix works: the URL shows the original search string of O'Neil but the top of the results Web page shows the escaped version O\'Neil
This is what the "mysql_real_escape_string" function does. This is not a complete solution for SQL injection, but it will stop simple attack tools like Havij.
Using Havij Again
In the Havij window, paste this URL into the Target field:http://ad.samsclass.info/sqlol-raw/search2.htm?q=x
In the Havij window, click the Analyze button.
The Log at the bottom of the Havij window shows red error messages, as shown below, because the site is no longer vulnerable.
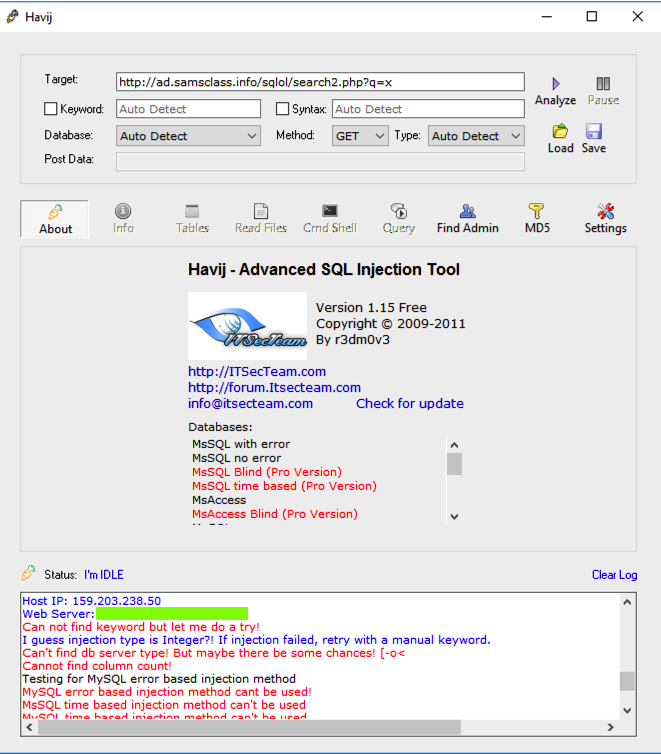
H 16.1: Web Server version (15 pts)
Scroll up a few lines in the Havij Status box to see the Web Server version, covered by a green box in the image above. That's the flag.Source
https://github.com/SpiderLabs/SQLol
Integrated with Canvas 11-1-18
Last image corrected 11-13-18
Ported to new soring engine 7-12-19