
dns
You see a DNS request and response, as shown below.

Every time you visit a site, your operating system send a DNS request for the domain without encryption, unless you are using a good VPN or an encrypted DNS protocol like DoH.
This is bad for privacy, but very convenient for network security monitors. If you want to know what your staff are doing, just monitor the DNS traffic and you'll easily who went where, and when.
from scapy.all import *
def findDNS(p):
if p.haslayer(DNS):
print p.summary()
print p.display()
sniff(prn=findDNS)
Many pages of data scroll by as the page loads, as shown below.
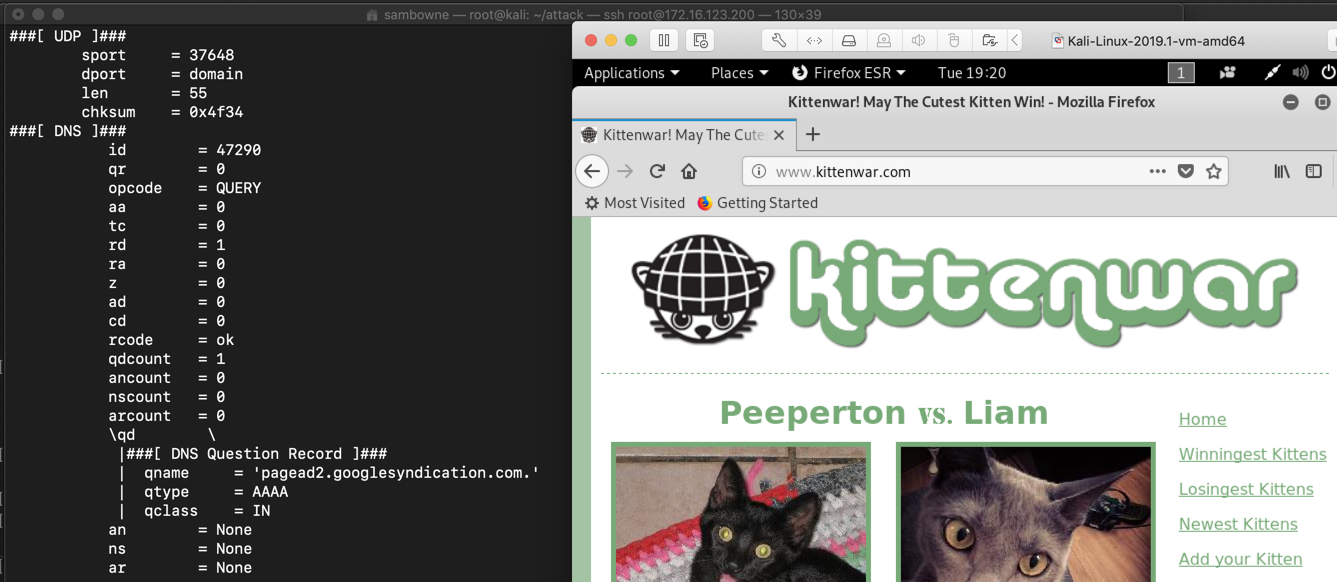
This is too much data--it's too messy.
from scapy.all import *
def findDNS(p):
if p.haslayer(DNS):
print p[IP].src, p[DNS].summary()
sniff(prn=findDNS)
The output is much cleaner now, as shown below.

http://target1.bowneconsulting.com/php/randomdomain.php
The page makes several calls to the server with different subdomains, as shown below.
You may need to refresh the page a few times to see different domain names.
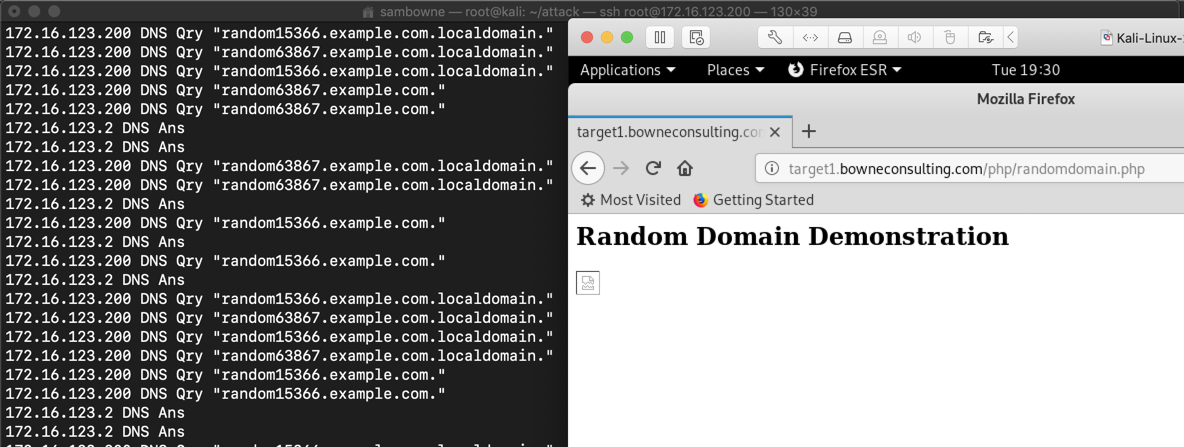
Malware frequently uses long, random-looking domain names, either to reach command-and-control servers or to exfiltrate stolen data.
http://target1.bowneconsulting.com/php/dnschal1.php
Refresh the page a few times. Monitor DNS and find the flag.
http://target1.bowneconsulting.com/php/dnschal2.php
Refresh the page a few times. Monitor DNS and find the flag.
http://target1.bowneconsulting.com/php/dnschal3.php
Refresh the page a few times. Monitor DNS and find the flag.
Links changed to http:// 4-7-19
Hint #2 added 4-14-19
Revised for WCIL 5-20-19